
The Office of Management and Budget (OMB) released their latest report to Congress last month. According to the Federal Information Security Modernization Act’s (FISMA) Annual Report to Congress, during FY 2015, Federal agencies reported 77,183 cybersecurity incidents, a 10% increase over the 69,851 incidents reported in FY 2014.
The Federal government has taken unprecedented steps toward updating its IT infrastructure and bolstering cybersecurity in the last several months through the Consolidated and Further Continuing Appropriations Act, 2015 (P.L. 113-235), and the FY 2017 President’s Budget proposal for a $17 billion investment in resources for cybersecurity. Despite those efforts, the OMB report reveals a trend – there’s still a coverage gap in two critical areas of agencies’ cybersecurity programs – privileged access management and threat analytics.
FISMA Section 3555 requires the Inspector Generals of each agency to evaluate their department’s cybersecurity practices and programs in ten areas. The table below is a summary of findings for 9 of the 10 program areas (excluding ISCM):
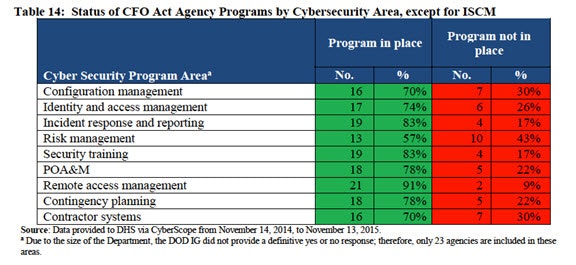 Programs not in place were more prevalent in the areas of configuration management, identity and access management, and risk management, with up to fifteen agencies not having one or more of these programs.
Programs not in place were more prevalent in the areas of configuration management, identity and access management, and risk management, with up to fifteen agencies not having one or more of these programs.
According to Table 14, 30% of agencies have no program in place for Configuration Management, and 26% have no program in place for Identity and Access Management.
The FISMA control families for Configuration Management include requirements for threat analytics, which are described as capabilities that identify deviations from the approved baselines, visibility at an enterprise level. For Identification and Authentication (represented in the report as identity and access management), the FISMA requirements include capabilities for strong authentication, multi-factor authentication, and privileged access management. These controls represent a great opportunity for agencies to protect their sensitive data and address the root cause of many recent breaches, including the OPM breach – unauthorized access through methods such as compromised privileged credentials.
Acing Your FISMA Audit With BeyondTrust
This annual report to Congress shows that there is much work to be done to reduce cyber risk to Federal networks. For agencies that are struggling with where to begin, we have developed a quick, 3-step path to improving adherence to FISMA requirements.
Step 1: Implement Privileged Password and Session Management
BeyondTrust PowerBroker Password Safe automates password and privileged session management, providing secure access control, auditing, alerting and recording for any privileged account. By improving the accountability and control over privileged access, IT organizations will reduce security risks and meet compliance requirements.
By combining PowerBroker Password Safe’s privileged password and privileged session management solutions with existing identity and access management tools, agencies can address the requirements for both strong authentication and privileged access management by ensuring privileged credentials protected.
Step 2: Extend Privileged Access Control to Use Endpoints
BeyondTrust PowerBroker for Windows, PowerBroker for Mac, and PowerBroker for Unix & Linux are least privilege management software products that reduce the risk of privilege misuse on physical and virtual Microsoft Windows and Mac desktops and Unix and Linux Servers. By implementing least privilege, agencies can eliminate administrator privileges, simplify the enforcement of least privilege policies, maintain application access control, and logs privileged activities. As a result, IT closes security gaps, improves operational efficiency, and achieves compliance objectives faster.
Step 3: Improve Visibility Over Areas That Pose the Greatest Risks
BeyondTrust helps agencies pinpoint deviations from the approved baselines and provide visibility at the organization’s enterprise level. BeyondInsight is an advanced threat analytics platform that enables IT and security professionals to identify the data breach threats typically missed by other security analytics solutions.
BeyondInsight pinpoints specific, high-risk users and assets by correlating low-level privilege, vulnerability and threat data from a variety of BeyondTrust and third-party solutions.
Want to learn more about how BeyondTrust¹s solutions can help your organization? Download our white paper, Meeting NIST SP800-53 Requirements with BeyondTrust Solutions.

Sandi Green, Product Marketing Manager, BeyondTrust
Sandi Green is the Product Marketing Manager for PowerBroker Password Safe, PowerBroker for Windows, and PowerBroker Mac at BeyondTrust. She has over 20 years of sales and solutions marketing experience with technology companies that served a variety of industries ranging from life sciences, human capital management, consumer packaged goods and most recently IT security. When she’s not following the latest trends in Cybersecurity, she’s busy following college football and basketball. Follow her on Twitter at @SandiGreen3.








