The U.S. Securities and Exchange Commission (SEC) has revealed that it’s fallen victim to a hack. In its recent “Statement on Cybersecurity, published by its Chairman, Jay Clayton, it was revealed that its controversial Electronic Data Gathering, Analysis, and Retrieval (EDGAR) system had been compromised last year and "may have provided the basis for illicit gain through trading".
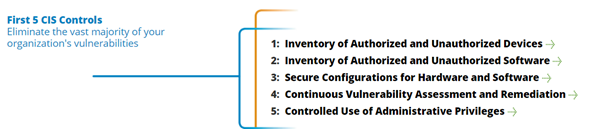
Unfortunately, this is not the first time the SEC has exposed financial data. In 2014, the SEC inspector general revealed that hundreds of agency laptops, potentially containing sensitive market data, could not be accounted for. If you look at the SANS institute’s CIS critical security controls, number 1 on the list is “Inventory of Authorized and Unauthorized Devices”. Put simply, you can secure what you don’t know about.
What about the more recent EDGAR breach? This system was designed to handle electronic filings of corporate statements. These statements relate to finances and events that may impact the business and include draft documents. The system is designed to ensure fairness by releasing all the relevant data to the public at the same time preventing individuals trading on advanced information.
As a result of the breach, it is believed that hackers may have accessed advanced information to gain an advantage in trades. Interestingly the breach occurred due to a software vulnerability in a test version of EDGAR. This is where alarm bells start ringing in terms of security best practice. In this case, it appears that a test system was connected to live SEC data and made publicly accessible. Given that test systems are generally not secured to the same level as production systems this is a huge red flag.
If we again look again at the CIS controls we see that secure configuration and vulnerability assessment and remediation are key controls to prevent an attacker easily exploiting a system. In this case ensuring that any system with access to sensitive data is secured. Moving beyond that it is important to harden the system by having an inventory (allow list) of authorized software and control administrative privileges. These last steps are key to stopping attackers leveraging a vulnerability to easily install backdoors and abuse privileged accounts access to data.
Given that the vulnerability was only patched after the breach was discovered it appears that just like the Equifax incident, this is a classic example of organizations failing to get the basics right around securing systems. No matter if a system is test or production if it contains business information it needs to be secured properly. Repeatedly it has been proven that applying the top 5 CIS controls or as an alternative the ASD top 4, mitigate the majority of cyber threats that seem to plague organizations globally.
Although it appears that the SEC has a good deal of work to do in improving their security posture this is hopefully a wakeup call to other organizations who may be sitting on a time bomb of unpatched systems, unauthorized applications and excessive use of admin privileges.

James Maude, Field Chief Technology Officer
James Maude is the Field Chief Technology Officer (FCTO) at BeyondTrust. With his broad experience in security research, both in academia and industry, James has spent the past decade analyzing cyber threats to identify attack vectors and trends in the evolving security landscape. He is an active member of the security community and hosts Adventures of Alice and Bob, a podcast that shines a light on the people making a difference in security. As an expert voice on cybersecurity, he regularly presents at international events and hosts webinars to discuss threats and defense strategies.








