 A few weeks ago, we published a blog on how to optimize PowerBroker for Windows rules to mitigate the threat of ransomware. We received great feedback on the success of the sample rules and also a few recommendations to fine tune them for unique environments. To that end, we have compiled the feedback into this blog so you can follow best practice recommendations to ensure you are not a victim. Check out the best practices below:
A few weeks ago, we published a blog on how to optimize PowerBroker for Windows rules to mitigate the threat of ransomware. We received great feedback on the success of the sample rules and also a few recommendations to fine tune them for unique environments. To that end, we have compiled the feedback into this blog so you can follow best practice recommendations to ensure you are not a victim. Check out the best practices below:
- Some applications, especially ones that are geographically based, are not digitally signed (yet) by their manufacturers and they are executed from %APPDATA% (C:\Users\*\AppData\Local\ or C:\Users\*\AppData\LocalLow\). While creating a simple wildcard passive Path Rule allows them to execute, it also can allow ransomware like TeslaCrypt to execute as well. The best recommendation is to identify each of the applications that need to execute from these locations and create Hash Rules. Hopefully, your environment only has a couple of applications that fall into this category, and we strongly recommend contacting each of these vendors and request they begin digitally signing their applications. Then, a simple Publisher can properly solve the execution issue with whatever privileges are needed.
- To ensure everything is working correctly, the Deny Rule should always be the last in the rule list. All passive and privilege rules should process first and then anything that has not matched will be denied.
- If there is a desire to block / deny applications before the last Deny Rule, consider applying rules to specific applications, paths, and temporary directories (i.e. c:\ or C:\windows\temp\).
- To ensure the best user experience, keep the rule base small, around 50 rules maximum. This will keep the performance optimized with minimal or no impact to the end user.
- All acceptable applications should have passive rules by Publisher (preferred and best practice) or a global path and subdirectory. Remember to include child applications when necessary. For example, “C:\Program Files\Custom Applications\*” as a passive rule with all children.
- If multiple applications that are unsigned and in various directories are installed, rules will be needed for each. Standardizing on a trusted directory structure would help minimize the number of rules and places malware can be deposited and executed on the system.
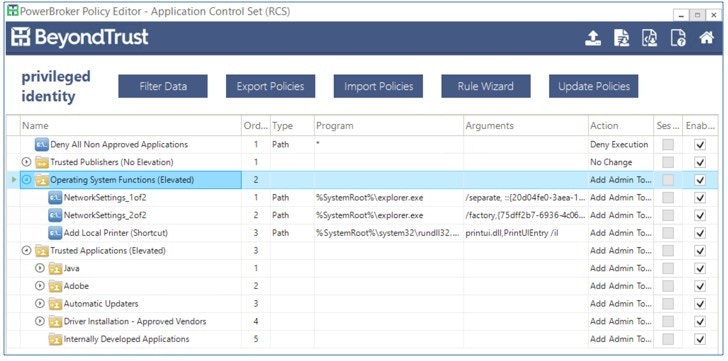 PowerBroker for Windows - sample rule base.[/caption]
Our solutions can mitigate much more than least privilege risks and a few simple rules can defend against the most common ransomware and exploit toolkits. If you have any other questions or recommendations for optimizing the rule base, please feel free to contact BeyondTrust Technical Support or your Account Manager.
PowerBroker for Windows - sample rule base.[/caption]
Our solutions can mitigate much more than least privilege risks and a few simple rules can defend against the most common ransomware and exploit toolkits. If you have any other questions or recommendations for optimizing the rule base, please feel free to contact BeyondTrust Technical Support or your Account Manager.

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.








