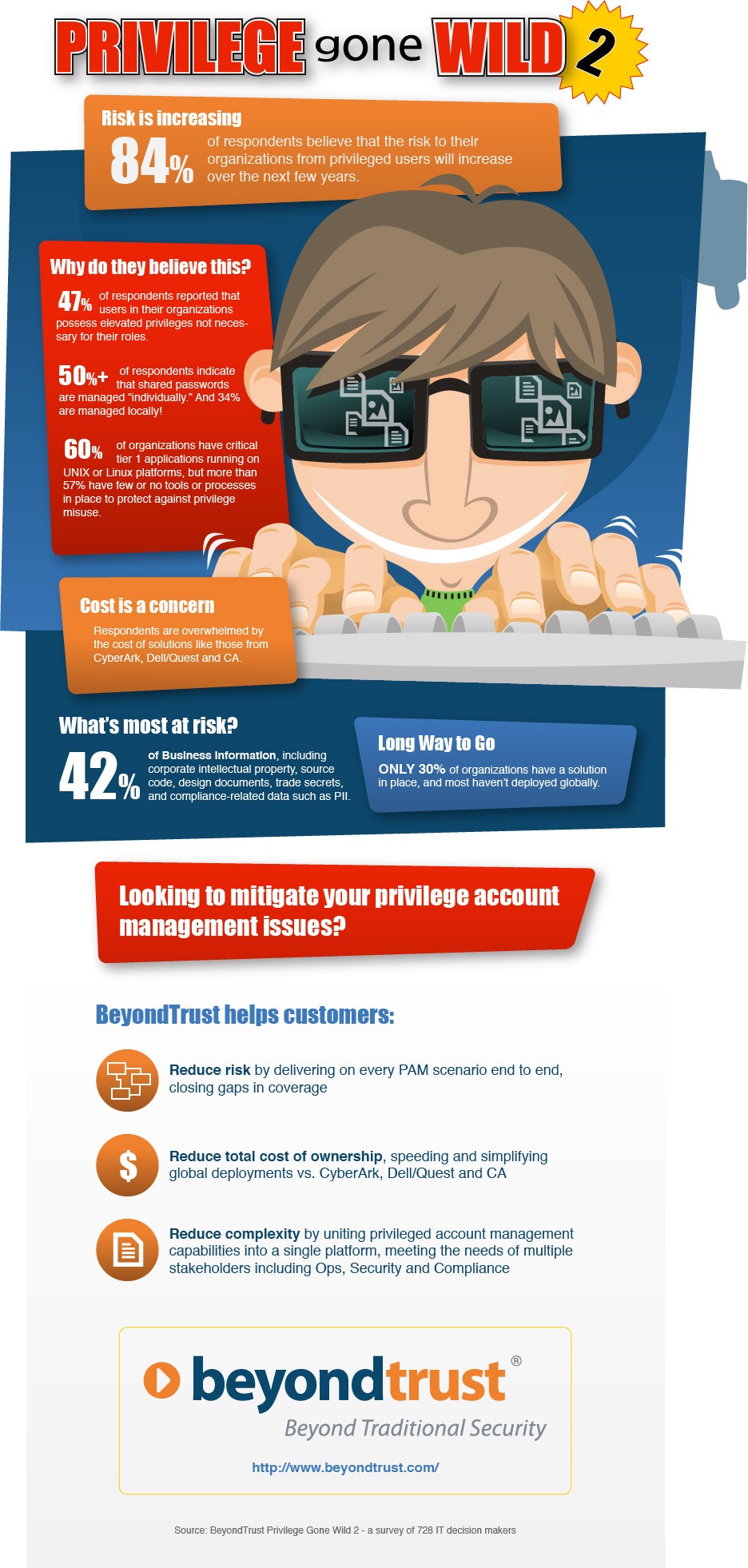
BeyondTrust recently conducted a survey to explore how organizations view the risk of misuse from privileged account misuse, as well as trends in addressing and mitigating those risks. Over 700 information technology professionals participated in the 2015 survey, representing organizations across multiple commercial and government verticals. And while there seems to be improvement over last year, there are still challenges that organizations must address. Some of the most important details from the report include:
- 84% of respondents believe the risk to their organizations from privileged users will increase over the next few years – especially in the area of access to business critical information.
- Nearly half of the survey respondents admitted they have employees with access rights not necessary for their current role, but shockingly, more than one out of four companies indicated they have no controls in place to manage privileged access.
- Privileged account management is viewed as a cross-functional need, with security teams primarily driving purchases – unified reporting is considered critical to meeting needs.
- Two of the most significant areas of weakness include shared passwords where over half of respondents indicated that shared passwords are managed individually; and privileged access to tier 1 systems where 57% of respondents have few or no tools or processes in place to protect against privilege misuse.
- Cost is a concern for organizations wanting to address these challenges, indicating that the most expensive privileged account management solutions available in the market are those from CA, Dell/Quest, and CyberArk.
The good news is that progress is being made. Recent, high-profile breaches involving the abuse of privileged credentials appear to be motivating organizations to take a deeper look as their privileged account management practices. But to help address continued weaknesses, and to accelerate privileged account management deployments, BeyondTrust recommends the following best practices:
1. Assemble cross-functional teams to address privileged account management. Siloed management and reporting just doesn’t work anymore in an era when a privilege problem extends beyond the security team, and external parties require access to internal systems.
2. Deploy policies for controls and enforcement. Policies are only worth the paper they’re printed on unless they are backed up with controls and enforcement. Solutions should seamlessly handle exceptions and simplify through workflow.
3. Prioritize implementation by the consequences of a breach. Factors to consider should include financial, regulatory and reputational costs to the organization. This approach helps build internal best practices for deployments.
4. End-user privileges are a good starting point to address gaps. As seen in the survey results, many organizations do not manage the privileges of any end users. A discovery exercise to identify all the privileged accounts in the organization can provide a baseline. The population of unmanaged end users is an ideal starting point at which to deploy a single solution to address a very large attack vector.
5. Address the risk of privileged password misuse. Unsupervised use of privileged accounts, through shared passwords or ad hoc policies, makes it impossible to control, track, or audit actions. If a breach occurs, whether deliberate or inadvertent, you need the ability to identify what happened, when, and by which user’s credentials.
Privileged account management should be viewed as an exercise in risk reduction. Risk comes in many forms – actual access risk, the risk of missing an audit requirement, or the risk resulting from sloppy administrative practices. A complete privileged account management solution should help you reduce risk, achieve your compliance objectives quickly, and do it all with a low total cost of ownership.
Getting started is the hardest part. For tips on how to get started with your privileged account management project, read the brief white paper summarizing the results of this study.

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








