
The latest releases of BeyondTrust PowerBroker for Windows and PowerBroker for Mac feature several exciting enhancements around user behavior monitoring, user-based rules and policy, and third-party integration, giving users unmatched visibility and control over physical and virtual desktops and servers. Here are some highlights of the new features.
PowerBroker for Windows 7.4
User Behavior and Lateral Movement Tracking
News of data breaches, advanced persistent threats, and large-scale hacks remain a constant reminder that no organization is completely safe from cyber-attacks. A common theme of recent attacks is lateral movement – where attackers gain access to a machine within an organization and attempt to move through the network, ultimately gaining access to sensitive data and/or critical systems. Combatting these attacks can be challenging. PowerBroker for Windows version 7.4 provides assistance in the detection and prevention of user behavior related to these activities. With PowerBroker for Windows version 7.4, IT admins can leverage rules to identify activities related to suspicious lateral movement.
PowerBroker for Windows version 7.4 allows administrators to create rules which can monitor common attack vectors targeted during lateral movement attacks.
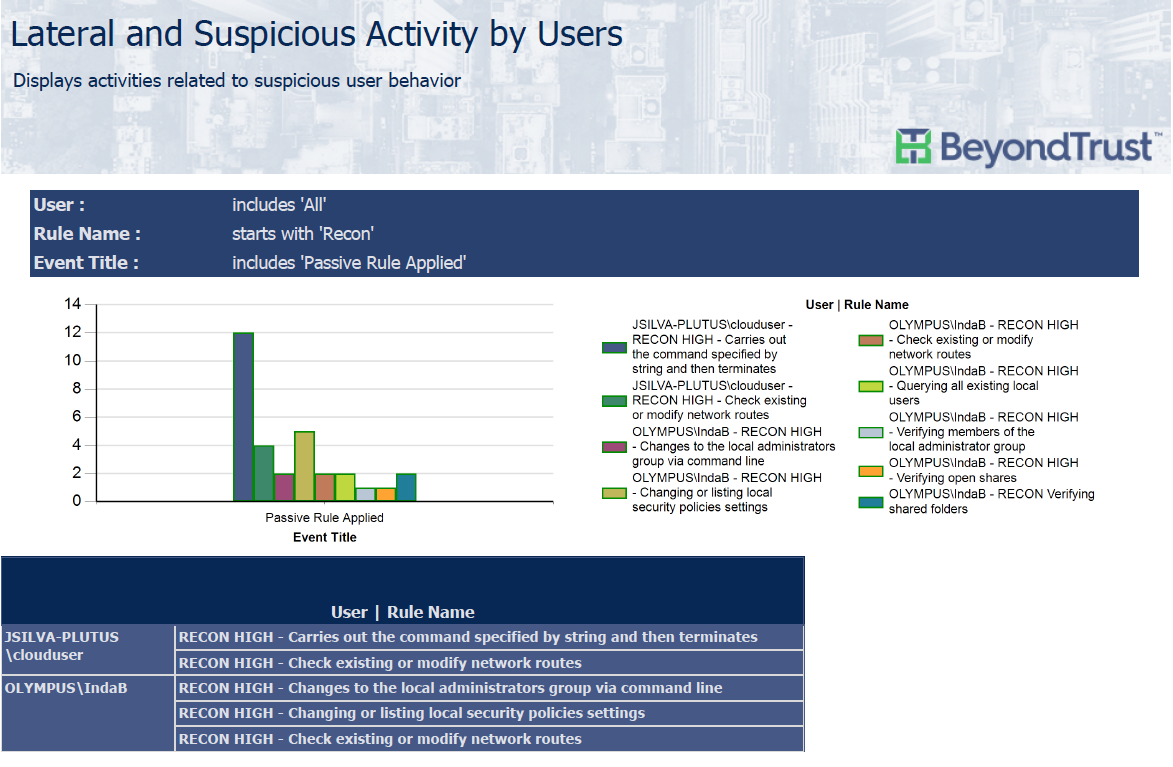 Lateral Movement Report
Lateral Movement Report
Enhanced Logging to Support Integration with PowerBroker Password Safe
PowerBroker for Windows, in unison with PowerBroker Password safe allows companies to securely launch an application as an alternate user in place of the default action of a PBW rule without exposing privileged credentials. This integration also acts as a password change agent for Password Safe in the event that a network-based password cycle fails, most often a result of lack of connectivity. PowerBroker for Windows version 7.4 provides additional logging of these activities to provide a better audit and compliance trail.
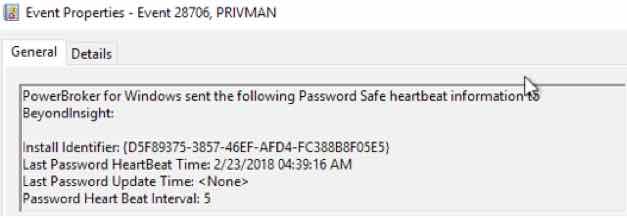 With PowerBroker for Windows version 7.4, events like a Password change are written to the event log.
With PowerBroker for Windows version 7.4, events like a Password change are written to the event log.
Enhanced Compatibility with Third-Party Security Software
Security software is an ever-changing landscape, with new solutions reaching the market. In order to future-proof your security portfolio investment, PowerBroker for Windows is designed to complement your security portfolio— for what you have now, as well as plan for in the future. PowerBroker for Windows version 7.4 has further enhanced its third-party security software compatibility settings.
PowerBroker for Mac 1.4 Highlights
MacOS High Sierra Support (10.13.x)
PowerBroker for Mac now offers support for MacOS High Sierra (10.13x). This provides parity functionality with previously supported versions of the OS and enables organizations to confidently and securely adopt the latest OS version without the risk of excessive user privileges.
Improve Security with User-based Rules and Policy
Central Policy, also referred to as BeyondInsight or Web Services Mode, enables customers to manage their PowerBroker for Mac rule set. Until now this mode only allowed for targeting assets/computers. By following and targeting policy to a user, [in addition to machine-based policy], on whatever PBMac managed device they log into, companies can better ensure a consistent security model and user experience throughout their networks.
 Stacking Policies Add Granularity to Policy via Web Services
Stacking Policies Add Granularity to Policy via Web Services
Many organizations require greater granularity of access policy than what typical web services can provide. For example, every user in Company can perform a basic set of actions, but for a select group of computers in the Company, there should be a special set of policies applicable only to them. If they choose to use web services instead of Group Policy for policy management, the Company should have the same capability available to them and not be limited by a single policy set. PowerBroker for Mac version 1.4.0 adds greater granularity to policy management delivered through web services with new stacking policies.
For a complete demonstration of these new features and even more enhancements not mentioned here, read the PowerBroker for Windows and PowerBroker for Mac new features documents. And if you have any questions or would like a personalized demo, contact us today.

Jason Silva, Sr. Solutions Architect
Jason Silva is a Senior Solutions Architect focused in Privilege Access Management (PAM), Identity and Access Management (IAM), and Least Privilege. Jason brings over 25 years of experience in solutions management to BeyondTrust's Privileged Access Management Solutions enforcing Privileged Password Management and Privileged Session Management, Privileged Endpoint Management, and Secure Remote Access which utilizes a single pane of glass for all management aspects including Automated Account Discovery, Privileged Management and Elevation, Audit and Compliance, and Reporting.








