On June 27, 2017 a number of organisations across Europe began reporting significant system outages caused by a ransomware strain referred to as Petya. The ransomware is very similar to older Petya ransomware attacks from previous years, but the infection and propagation method is new, leading to it being referred to as NotPetya. Due to the sudden and significant impact of the attack, it was immediately likened to the WannaCry outbreak causing concerns globally.
The best defence against this threat is to remove admin accounts, allow list applications and patch systems. This prevents the attacker from gaining a foothold, launching payloads and exploiting known vulnerabilities.
There is some confusion about the initial delivery mechanism of the malware, with speculation about phishing emails. Microsoft analysis points to MeDoc accountancy software executing a malicious command matching the known attack pattern of this malware. This would indicate the infection occurred due to a compromised supply chain.
NotPetya Analysis
Our initial analysis shows that “patient zero”, the first user targeted, must be an admin user for the attack to succeed. Without admin rights, the malware is unable to overwrite the critical system areas, capture credentials or embed itself in the operating system. Much of the functionality, including clearing event logs and overwriting boot records, is reliant on admin privileges.
Once an infection has occurred, the attackers primary method of spreading is using LSADump a modified version of the Mimikatz tool used to perform Pass the Hash attacks by exploiting admin accounts and credentials stored in memory. This explains how organisations who believe they were patched with MS17-010 were still impacted. Removal of admin rights is key to preventing this type of credential theft and lateral movement, which is often used by malware and hackers.
It’s important to consider that even temporary use of administrator accounts can leave credentials in memory that can be abused by an attacker. This is a mistake many organisations make by allowing domain admins to remote into users’ endpoints exposing the credentials. Privilege management not only prevents theft of credentials but can also remove the need for risky administrator logins.
The malware also contains code for the EternalBlue exploit, which was used by WannaCry to spread. In March, Microsoft released a patch for this for all systems, including the now unsupported Windows XP. Those organisations who have not yet patched and are still vulnerable should disable SMBv1 on unpatched systems and segregate these systems at a network level to prevent the spread.
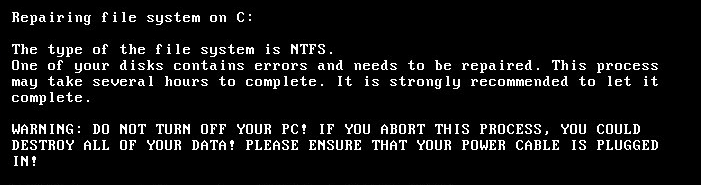
Figure 1- Screen during encryption
Once a system is infected the malware triggers a reboot which causes the attackers boot loader to be executed. This displays a fake Chkdisk screen which appears to be repairing the disk whilst encrypting the files. In the event this screen appears users should power off immediately to preserve as much data as possible. As the malware crashes the system to trigger the reboot organisations should consider disabling reboot on system error.
The email addresses linked to this malware have been suspended by the providers and there is no evidence that paying the ransom will result in files being decrypted. The best advice is to never pay ransom demands.
Key NotPetya findings and security recommendations:
The NotPetya malware attack highlights the importance of proactive measures such as least privilege, allow listing and patching. These measures are proven to be the most effective defences against the majority of cyber attacks.
Here's a summary of key NotPetya findings and security recommendations:
- Admin accounts were the primary targets to gain a foothold and propagate within a network
- Removal of admin rights is a key mitigation strategy
- Where possible organisations should patch with MS17-010, or disable SMBv1
- The attackers email account has been disabled so even if organisations pay the ransom they have no way to contact the attackers and arrange decryption
- The malware is only designed to spread across a local network, so is less likely to spread with the same speed as WannaCry
- The attackers use multiple tools dropped to disk including Microsoft’s PSExec, which is not native to the Windows OS. These can be blocked with Application Control.
- Deny network login to all local admin accounts (https://technet.microsoft.com/en-us/library/dn745900(v=ws.11).aspx#SEC_Deny_Network_Logon)
- Implement LAPS for local admin accounts to ensure unique & rotated local admin passwords. (https://technet.microsoft.com/en-us/mt227395.aspx)

James Maude, Field Chief Technology Officer
James Maude is the Field Chief Technology Officer (FCTO) at BeyondTrust. With his broad experience in security research, both in academia and industry, James has spent the past decade analyzing cyber threats to identify attack vectors and trends in the evolving security landscape. He is an active member of the security community and hosts Adventures of Alice and Bob, a podcast that shines a light on the people making a difference in security. As an expert voice on cybersecurity, he regularly presents at international events and hosts webinars to discuss threats and defense strategies.











