Let me get this out right off the bat: There is no one solution that is 100% effective in mitigating the risk of ransomware. Some vendors are claiming to have tested hundreds of samples, and that their tool can stop 100% of the samples. I’m sorry, but that is a falsehood. Why? If any single vendor had a solution that solved the problem completely, ransomware would not be such a problem.
Application control solutions, endpoint protection products, and even least privilege solutions have various degrees of success in mitigating ransomware but none are 100% effective. Why? Modern ransomware does not care about privileges, does not always launch separate executables, and sometimes targets obscure devices like smart TVs. We have seen a spike in ransomware that uses Microsoft Office macros to propagate the threats, and even versions that use jscript embedded in a document to conduct malicious activity.
The delivery of the payload is equally as impressive to identify. It can come from an exploitable vulnerability, an errant executable (the easiest to stop), PowerShell script, or embedded as a macro or script in a file or website. What makes this a little more disturbing is that many attacks combine methods and use a command control server to hold encryption certificates verses locally based per infection that can be cured with a vaccine.
Based on these facts, this is why ransomware is so difficult to stop and no one technology – from any vendor – is 100% effective. Sorry – I just need to set the record straight and make sure that marketing claims are not reality.
There are some actions you can perform with products like PowerBroker for Windows to minimize the threat. Unfortunately, nothing will ever replace training users to not click on phishing links or select Run Macros when opening an unknown file. However, here are a few rules that are easy to implement that will block the vast majority of mistakes users can make, stop droppers from executing, and block vulnerable applications from being leveraged against your assets:
Block Untrusted Executables
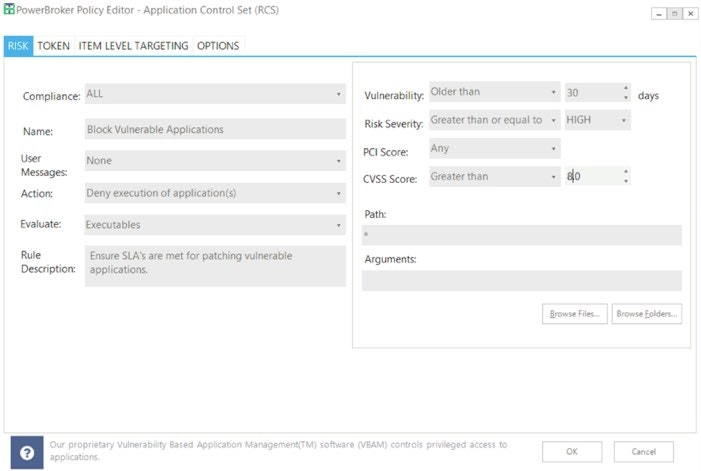
PowerBroker for Windows allows for rules to elevate applications as well as verifying applications meet specific criteria. Below is a screen shot of a basic ruleset elevating specific applications, trusting authorized vendors and custom applications, and denying any other executable that does not meet this criteria. This will stop any non-authorized application from executing regardless of the source if it is not properly digitally signed.
Stopping Droppers
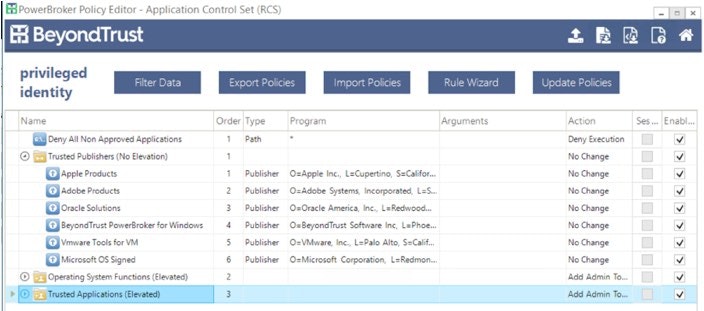
Unfortunately, trusted applications can launch other applications to perform their intended functions. This includes browsers, mail programs, and even PDF readers. The consistent part of this problem is that these executables almost always launch from temporary file directories. Using PowerBroker for Windows File Integrity Rules, administrators can track, alert, and block rogue dropper executables that appear in these directories. Below is a screenshot of what this rule looks like for Microsoft Outlook.
Please note, the temporary directory path can vary per operating system and Outlook version. Multiple rules may be needed to cover each of your deployed platforms.
Blocking Vulnerable Applications
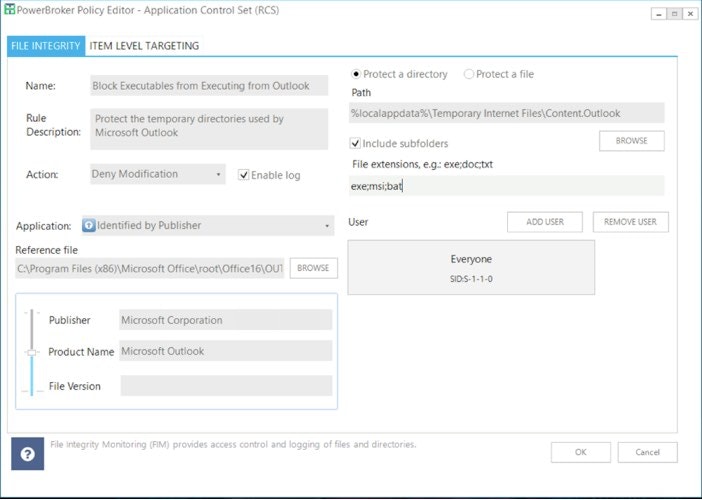
PowerBroker for Windows contains patented technology called Vulnerability Based Application Management (VBAM). This Risk and Compliance feature allows for real-time assessment of vulnerable applications based on the Retina Vulnerability Database and user interaction of a system. To that end, policies can be established to deny (or notify of) the launch of a vulnerable application that could be leveraged in a ransomware attack. This helps ensure service level agreements are being met for patch management and no system is left out that could pose an unacceptable risk. Below is a screenshot of a basic Risk and Compliance rule that will Deny an application from launching if the documented vulnerability is critical and over 30 days old.
While no solution is 100% effective in stopping ransomware, there are plenty of good products that can drastically reduce the risk. Thankfully, creating rules like these in PowerBroker for Windows can accomplish this goal and reduce the overall risk to your assets by adopting the concept of least privileged across all you endpoints (including Mac’s with PowerBroker for Mac).
If you would like to learn more about how PowerBroker can help mitigate the risks of ransomware, contact us today.
For more tips on optimizing PowerBroker for Windows to defend against ransomware, please see Ransomware – Fine Tuning PowerBroker for Windows Rules, Part 2.

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.