 Hopefully you recognize that today is May the 4th – the unofficial Star Wars Day (and a bad pun on “May the force be with you”). Yesterday, May 3rd, was National Password Day, and the news exploded with revelations that Twitter reported a bug in their logging system that exposed potentially all users’ passwords in clear text files.
While no breach was reported, logging passwords in clear text is a major security snafu. As Twitter and the news reported, users logging into Twitter were presented with this ominous message:
Hopefully you recognize that today is May the 4th – the unofficial Star Wars Day (and a bad pun on “May the force be with you”). Yesterday, May 3rd, was National Password Day, and the news exploded with revelations that Twitter reported a bug in their logging system that exposed potentially all users’ passwords in clear text files.
While no breach was reported, logging passwords in clear text is a major security snafu. As Twitter and the news reported, users logging into Twitter were presented with this ominous message:
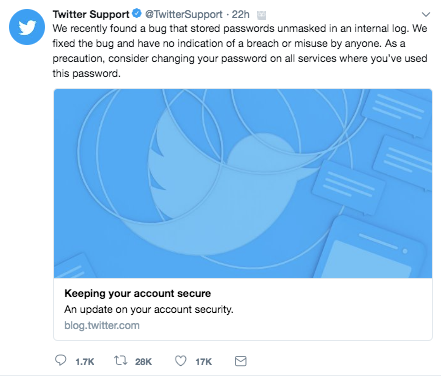
Change your Twitter password now!
For those that ignored the message, please reconsider and change your password. If you continue to ignore the recommendation, may the force be with you. Why? Because your password has been recorded in clear text and only Twitter knows how many copies and were those log files may exist. They are probably in backups, development servers, and who know where else. They could be breached at a later time and exploited. This is why the recommendation is so important to change them right now.In fact, change all of your other passwords, tool!
Your Twitter account is not the only potential application impacted by this notification. This same type of flaw, password re-use, was responsible for some of the most devastating breaches in the past several years, like Yahoo. Re-used Yahoo passwords caused identity theft for many individuals and businesses once their email account and password were stolen and threat actors determined that other sites used the same credentials. People got owned and there was no force, outside of changing your passwords, that protected them. Therefore, there is one additional recommendation on password re-use. If your Twitter account uses the same password as any other account, please go and change all of them now too. Just like Yahoo, once that password finds it out into the wild, every one of those accounts could be in jeopardy too. This is why a security best practice is to keep all of your passwords unique and never re-use them. Consider managing your enterprise social media account passwords with PowerBroker Password Safe. This will protect your business from these types of problems, and if you are already managing Twitter access today, it would be a good thing to force rotation of these passwords to something unique. Today. May the force be with you and protect all your privileged accounts; especially those online.
Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.








