 While the terminology may vary, for nearly two decades the basic approach to vulnerability management hasn’t changed - discover assets, audit them for vulnerabilities, prioritize and patch them, and report on progress. And while valuable in limiting an attack surface, this find, fix, automate and repeat closed loop method falls short in helping organizations:
While the terminology may vary, for nearly two decades the basic approach to vulnerability management hasn’t changed - discover assets, audit them for vulnerabilities, prioritize and patch them, and report on progress. And while valuable in limiting an attack surface, this find, fix, automate and repeat closed loop method falls short in helping organizations:
- Reduce remediation times for known vulnerabilities.
- Gain insights into new and emerging threats.
- Use vulnerability intelligence to inform least privilege access and increase threat visibility.
- Close vulnerability gaps created by technologies such as cloud, mobile, virtual, Internet of Things (IoT) and Operational Technologies (OT).
- Measure the impact of threats before they’re exploited.
- Evolve their focus from risk reduction to risk management.
- Adding real-time vulnerability intelligence to SIEM solutions for superior targeted attack and breach detection, as well as broader compliance visibility.
- Combining asset intelligence with PAM solutions to make privilege decisions based on an application’s known vulnerabilities, their age, potential risk, and compliance impact.
- Correlating NGFW traffic with detailed vulnerability, malware and attack data for a holistic view of critical asset risks.
- Communicating with NMS and ticketing systems to escalate security and compliance events into existing IT workflows and automatically verify and report results.
- Discovering and classifying cloud-based assets, and their associated vulnerabilities for a clearer picture of risk and compliance in the cloud.
- Inserting security configuration assessment data into GRC solutions so you can track how configuration changes affect compliance.
- Linking to asset management systems to launch vulnerability scans, and generate incident tickets directly from their consoles.
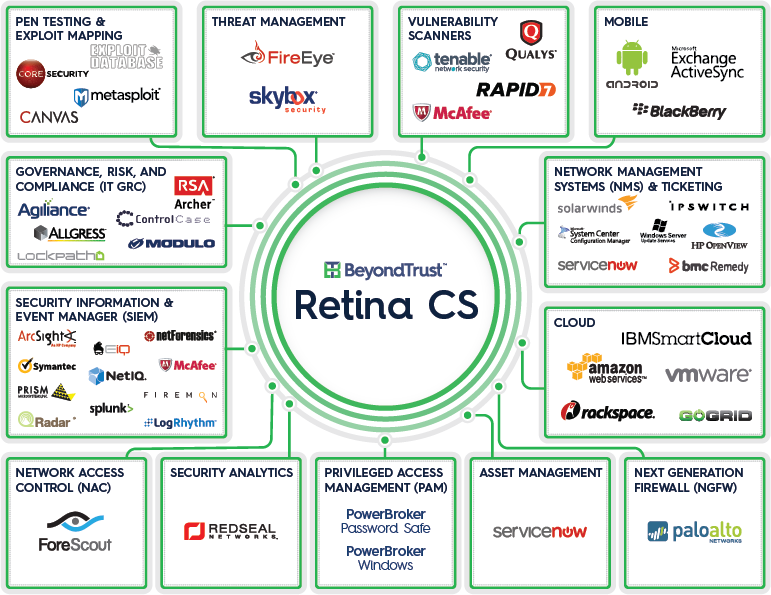 Stop trying to defend against 21st century attacks in isolation. Your adversaries are too smart, well-funded and determined to be turned away by point solutions fraught with blind spots. Enlist the eyes and ears of your entire “security village”, automate their interactions, coordinate their intelligence and surround your foes to uncover and track hidden and emerging threats and to quickly respond to attacks.
Ready to test drive how this can make a difference for you? Try Retina CS for free!
Need more information? Download our latest white paper, 10 Reasons to Rethink Your Vulnerability Management, and see how Retina’s cutting-edge capabilities can keep you steps ahead of the bad guys.
For more, contact us today!
Stop trying to defend against 21st century attacks in isolation. Your adversaries are too smart, well-funded and determined to be turned away by point solutions fraught with blind spots. Enlist the eyes and ears of your entire “security village”, automate their interactions, coordinate their intelligence and surround your foes to uncover and track hidden and emerging threats and to quickly respond to attacks.
Ready to test drive how this can make a difference for you? Try Retina CS for free!
Need more information? Download our latest white paper, 10 Reasons to Rethink Your Vulnerability Management, and see how Retina’s cutting-edge capabilities can keep you steps ahead of the bad guys.
For more, contact us today!

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








