Malware is an ever evolving field and as such security should be seen as a journey not a destination. One of the latest malware evolutions is the practice of Malvertising where attackers place malicious content in seemingly innocent adverts. When the user views the page the advert is loaded and the malware attempts to exploit the machine.
Why Malvertising?
There are a few advantages for the attacker over phishing emails or websites. As the adverts are often displayed on well-known websites the attackers can wait for victims to come to them. They can also exploit the users in the popular website to push fake updates and malware to the user. The attackers can remain anonymous, hiding behind the 3rd party ad-networks that buy and sell advertising space on websites. In more recent cases attackers use the marketing tools created by ad-networks to target specific demographics or industries.
Where are the attacks?
Throughout 2014 several major websites including yahoo.com, java.com and youtube.com have all been hit by malvertising campaigns.

One recent high profile example targeted the popular news site The Huffington Post. On the 31st of December researchers noticed the Canadian version of the site www.huffingtonpost.ca was infected, this was followed in early January by the main US site www.huffingtonpost.com. The source of the infection was traced to an advert on the AOL ad-network (advertising.com) which redirected to a Flash exploit and VB Script that silently downloaded and ran malware on the victim's machine.
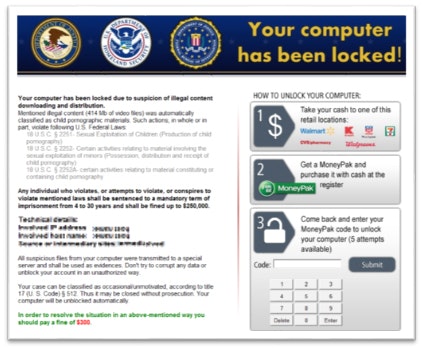
In this case the malware dropped was Kovter a type of ransomware that attempts to lock the computer until a "fine" has been paid for viewing illegal material. The malware uses geolocation to tailor the ransom message to the local law enforcement using FBI and police logos.
This recent campaign was estimated to be generating upwards of $25,000 of revenue per day for the attackers, with little chance of retribution. With this kind of revenue we can expect to see many more of these attacks throughout 2015.
What's the answer?
From the website owners point of view this is tricky, they rely on the income that advertising generates in order to survive. Ultimately the ads served up on their pages are out of their control and they are at the mercy of ad-networks. The ad-networks do attempt to screen content, however as they don't host the adverts criminals can redirect or swap out the ad after it has been screened.
As the problem will ultimately land on the endpoint we should start there. Keeping endpoints fully patched and using modern browsers can help prevent common attacks that exploit known vulnerabilities. However this only works against known threats, to deal with 0 days and more advanced attackers we need to look to a proactive defense in depth strategy.
Evidence suggests that to combat increasingly complex attack vectors, organizations need to adopt a layered strategy that prioritizes high-impact solutions, such as privilege management, application control and sandboxing. This proactive approach means you mitigate the risk of being caught out by the next malware campaign.
To find out more about proactive Defense in Depth solutions visit www.avecto.com or talk to one of our advisors.

James Maude, Field Chief Technology Officer
James Maude is the Field Chief Technology Officer (FCTO) at BeyondTrust. With his broad experience in security research, both in academia and industry, James has spent the past decade analyzing cyber threats to identify attack vectors and trends in the evolving security landscape. He is an active member of the security community and hosts Adventures of Alice and Bob, a podcast that shines a light on the people making a difference in security. As an expert voice on cybersecurity, he regularly presents at international events and hosts webinars to discuss threats and defense strategies.








