Locky is the latest in an ever increasing range of ransomware threats used by cyber criminals in an expanding and increasingly lucrative market. . What makes Locky special is that it appears to have come from the same group behind several large Dridex campaigns showing that they are possibly diversifying their range of attacks.
The Locky strain has been observed in the Avecto malware labs and by other researchers spreading via Word documents attached to phishing emails. These typically look like invoices and come from a variety of domains. So far, the campaign seems to be very successful and well-orchestrated with a global impact across all industries.
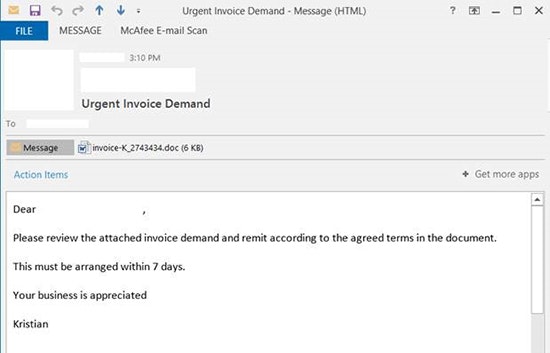
Figure 1: Locky Phishing Email
When the user enables the macros in the malicious document the Locky malware executable is dropped in the user’s temporary directory and executed. This then renames and encrypts all the users documents, changes their wallpaper to a ransom demand and will also attempt to silently delete backup shadow copies of the filesystem.
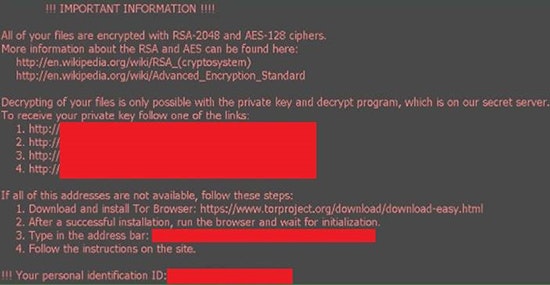
Figure 2: Locky Ransom Demand
The problem for traditional security solutions trying to prevent threats such as Locky is they are reliant on detecting it to prevent it. Even if a detection solution could detect 99 out of 100 threats it only takes 1 instance of Locky to go unnoticed to inflict serious damage. In the case of Locky it took most AV vendors days to catch up.
So how can Defendpoint help?
Defendpoint is designed to handle unknown, undetectable threats in a straightforward and proactive way. When the user downloads an unknown email attachment, clicks a malicious link or opens a document from the internet the content is seamlessly isolated in a Sandbox. This ensures that the malicious document and exploits are unable to access the user’s private data preventing it being stolen or encrypted.
As well as the secure isolation provided by Defendpoint’s Sandbox it also provides a unique context for Application Control. We know that content originating from untrusted external sources should not be launching new applications or running Windows tools such as PowerShell. This makes it easy to block any payloads or scripts dropped to disk within the Sandbox without limiting the user’s ability to run applications or access these tools.
This is of course all made possible by the fact that Defendpoint provides a least privilege environment with several secure anti-tamper features. This prevents the circumventing of security measures by both malware and rogue users.
What happens when Locky tries to run on a Defendpoint protected endpoint?
It’s stopped dead in its tracks, the payload is contained within the Sandbox and prevented from launching. When the user next logs off the Sandbox is regenerated and all traces of the malware are wiped from the disk.
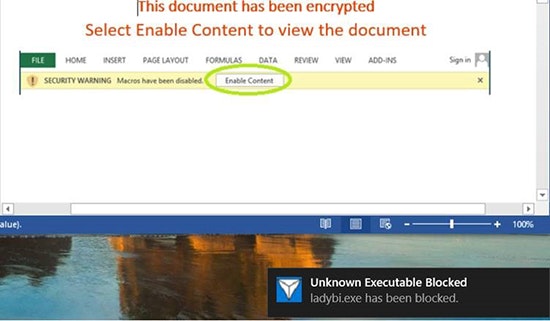
Figure 3: Application Control Blocks Payload in Sandbox
All of this occurs without detection or analysis, it works just as well for present day attacks as future ones.
So if you want to start getting ahead of malware threats and safeguarding your endpoints start thinking proactively and learn that prevention is possible.

James Maude, Field Chief Technology Officer
James Maude is the Field Chief Technology Officer (FCTO) at BeyondTrust. With his broad experience in security research, both in academia and industry, James has spent the past decade analyzing cyber threats to identify attack vectors and trends in the evolving security landscape. He is an active member of the security community and hosts Adventures of Alice and Bob, a podcast that shines a light on the people making a difference in security. As an expert voice on cybersecurity, he regularly presents at international events and hosts webinars to discuss threats and defense strategies.








