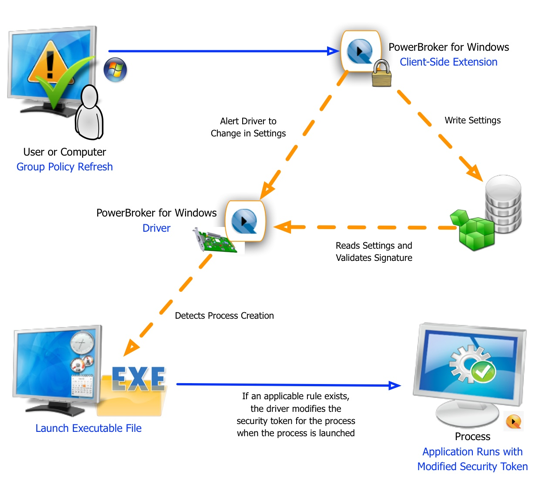
 Again, the user’s privileges never change and the modified application runs with the new security token, which can be customised to any level required for the application to correctly function:
Again, the user’s privileges never change and the modified application runs with the new security token, which can be customised to any level required for the application to correctly function:
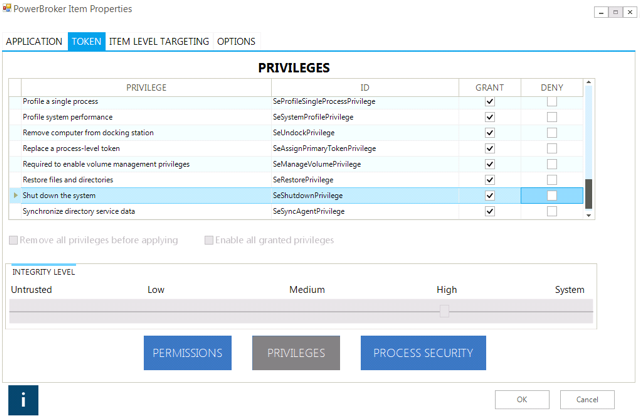 As a result, the user never has a hash that malware or a hacker can leverage against another resource with elevated permissions. In addition, the privileges granted to the application could either be executed as a full administrator or customised to only allow the privileges or process required for the task to execute. For example, the application can be granted full administrative privileges but denied access to shut down the system.
The fact remains that, in most organisations, too many users have excessive privileges. Hacking techniques like Pass-The-Hash have been successfully used to maliciously compromise entire infrastructures. Simply removing privileges can cripple business productivity, since critical applications and tasks can no longer function correctly as a standard user. A tool or technique is needed to bridge that gap, and PowerBroker for Windows is that solution.
PowerBroker for Windows preserves the privileges granted to the user and only modifies the application’s runtime security token to meet the needs of the application (on a per application basis). With over 250 rules in PowerBroker’s sample rules library, you do not need to start from scratch to make this change a reality. Our best practices guide, professional services team, and years of experience in privileged account management can help make hacking techniques like this a moot point for your business.
As a result, the user never has a hash that malware or a hacker can leverage against another resource with elevated permissions. In addition, the privileges granted to the application could either be executed as a full administrator or customised to only allow the privileges or process required for the task to execute. For example, the application can be granted full administrative privileges but denied access to shut down the system.
The fact remains that, in most organisations, too many users have excessive privileges. Hacking techniques like Pass-The-Hash have been successfully used to maliciously compromise entire infrastructures. Simply removing privileges can cripple business productivity, since critical applications and tasks can no longer function correctly as a standard user. A tool or technique is needed to bridge that gap, and PowerBroker for Windows is that solution.
PowerBroker for Windows preserves the privileges granted to the user and only modifies the application’s runtime security token to meet the needs of the application (on a per application basis). With over 250 rules in PowerBroker’s sample rules library, you do not need to start from scratch to make this change a reality. Our best practices guide, professional services team, and years of experience in privileged account management can help make hacking techniques like this a moot point for your business.

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.








