At the beginning of this month, US-CERT issued a security alert relating to a string of breaches that had been targeting Point of Sale (POS) systems. The alert details that attackers were leveraging brute forcing tools to target common remote desktop applications such as Microsoft’s Remote Desktop, Apple Remote Desktop, Splashtop and LogMeIn among others. These brute-force attempts were typically made against administrator or privileged accounts, which then allowed the attackers to deploy malware specifically designed to steal consumer payment data from POS terminals.
These attacks re-emphasize the need for organizations to implement basic security measures. For instance, remote management systems just shouldn’t be so directly accessible. And passwords definitely shouldn’t be so easily susceptible to brute force attempts. These basics are widely considered as best practices to any security consultant worth their mettle. But if that’s the case, why do we continue to see so many companies fall short?
In large part, it’s simply easier said than done. We know we should deploy strong passwords throughout our organizations, but using the built-in operating system tools for managing passwords enterprise-wide can be cumbersome at best. Likewise, not having a streamlined process for vulnerability management can make you blind to the various remote desktop/administration tools that increase your overall attack surface. Vulnerability management is after all not simply about discovering individual vulnerabilities that require patching, but rather analyzing your overall configuration to figure out ways to reduce your attack surface.
BeyondTrust helps companies overcome these types of challenges by providing solutions that enable businesses to more easily implement security best practices. Our Retina Vulnerability Management solution not only identifies vulnerabilities, but also helps you analyze configuration. It provides insight into where you are leveraging common remote desktop/management solutions – and then enables you to disable/protect such systems through configuration at the application, operating system or network level.
When it comes to mitigating brute-force attacks, effectively using and managing complex passwords is critical. The reality is that brute forcing remote administration protocols should be a terribly difficult thing for an attacker to do if you have, a) properly configured the application to reduce its attack surface, and b) properly used complex passwords that make the required number of iterations of brute-force password guesses simply infeasible.
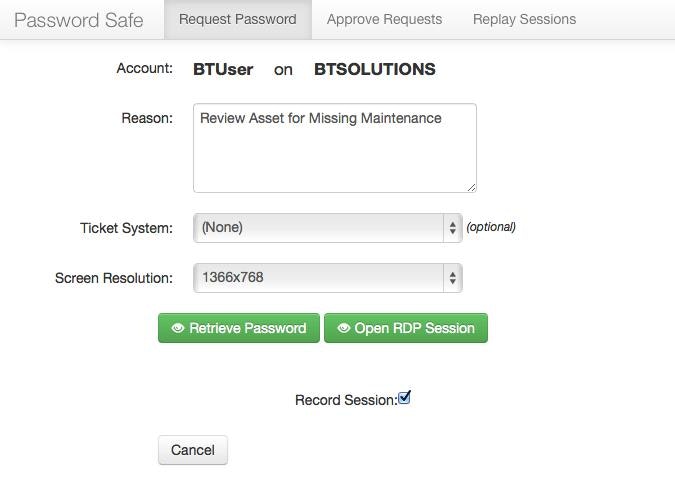
One of the reasons a lot of companies fail to create and rotate complex passwords is because the various operating systems and applications we use have very rudimentary methods of enacting a proper password management process. At BeyondTrust, we enable companies to overcome these password management hurdles through our PowerBroker Password Safe product. Password Safe allows organizations to properly manage, secure, maintain, and delegate complex passwords. This enables businesses to have complex passwords that are frequently changed and also to delegate control of passwords via administrative sessions.
For example, you can delegate access to a Microsoft Remote Desktop or Linux SSH session where an employee directly receives an authenticated session, without having to actually know the complex and frequently changing password itself. This is just one of the many examples of how Password Safe can minimize the complexity of implementing privileged password management as a security best practice.
It’s important to understand that the world of vulnerabilities and privileges is one that directly intersects, as many demonstrated by these Backoff POS attacks and many others. While the origins of an attack might start with a vulnerability or configuration weakness, giving an attacker a foothold in your environment, the final stage of an attack before your data is stolen often results from the abuse of existing user accounts, passwords and privileges.
Most IT and security teams have a wide gaps in their abilities to understand and correlate risks from vulnerabilities and privileges in their organizations. This is a gap that attackers continue to exploit on an increasing basis. BeyondTrust is the first and only company to combine class-leading vulnerability management and privilege management solutions into a single IT risk management and reporting console via our BeyondInsight solution. If you have not checked out BeyondInsight, please get in touch so we can show you how these two worlds are colliding and what you can do about it.

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








