 In our quest for a complete picture of enterprise risk, those of us in the IT and cyber security worlds endlessly collect data on users, endpoints, servers, web applications and more. We scour the far corners of our networks, obsessively looking for a mere trace of evidence that might give us an advantage over mostly invisible and well-armed foes. And as a result, the majority of IT and security pros now struggle with the deluge of data that is blasted at them almost daily.
For sure, more data is better. But how can you make sense of it all? And more importantly, how will you prioritize your most critical threats, respond to incidents quickly and clearly communicate progress to others?
Most vulnerability management solutions generate vast amounts of data, reported across hundreds of pages, listing found vulnerabilities along with their associated CVSS severity levels, CVE identifiers, and recommendations for corrective actions. While these reports provide valuable data, they lack the additional context to prioritize which assets or vulnerabilities to focus on - leaving organizations unable to identify their greatest threats.
Since you will never be in a position to fix all of your open vulnerabilities, you must be smarter about which ones to fix first, second and third, as well as last. Retina CS provides results-driven reporting and analytics that put risk into focus by enabling you to prioritize vulnerabilities by answering critical qualifying questions such as:
In our quest for a complete picture of enterprise risk, those of us in the IT and cyber security worlds endlessly collect data on users, endpoints, servers, web applications and more. We scour the far corners of our networks, obsessively looking for a mere trace of evidence that might give us an advantage over mostly invisible and well-armed foes. And as a result, the majority of IT and security pros now struggle with the deluge of data that is blasted at them almost daily.
For sure, more data is better. But how can you make sense of it all? And more importantly, how will you prioritize your most critical threats, respond to incidents quickly and clearly communicate progress to others?
Most vulnerability management solutions generate vast amounts of data, reported across hundreds of pages, listing found vulnerabilities along with their associated CVSS severity levels, CVE identifiers, and recommendations for corrective actions. While these reports provide valuable data, they lack the additional context to prioritize which assets or vulnerabilities to focus on - leaving organizations unable to identify their greatest threats.
Since you will never be in a position to fix all of your open vulnerabilities, you must be smarter about which ones to fix first, second and third, as well as last. Retina CS provides results-driven reporting and analytics that put risk into focus by enabling you to prioritize vulnerabilities by answering critical qualifying questions such as:
- Does a known exploit exit?
- Can it be exploited remotely and by someone without privilege?
- Is there active malware using it?
- Can it be fixed via a patch or configuration change or is it a zero-day?
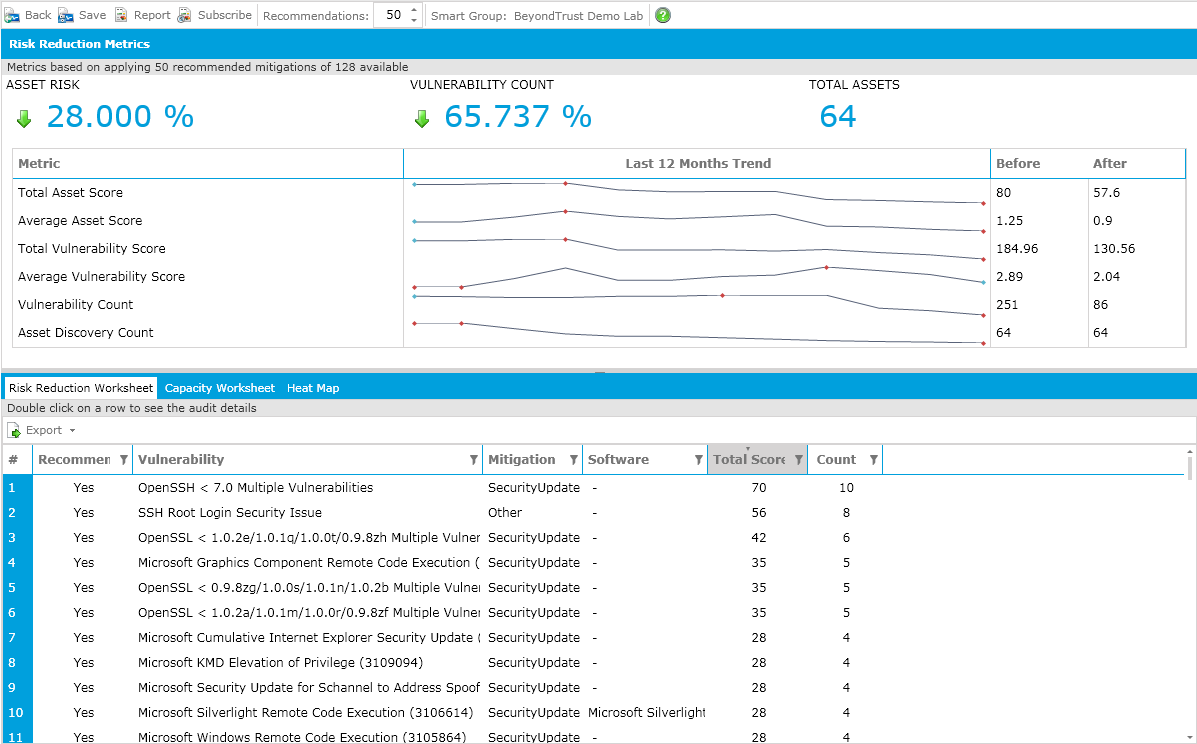
 Return on Remediation Analysis predicts the impact of risk reduction efforts before you commit resources.
Return on Remediation Analysis predicts the impact of risk reduction efforts before you commit resources.
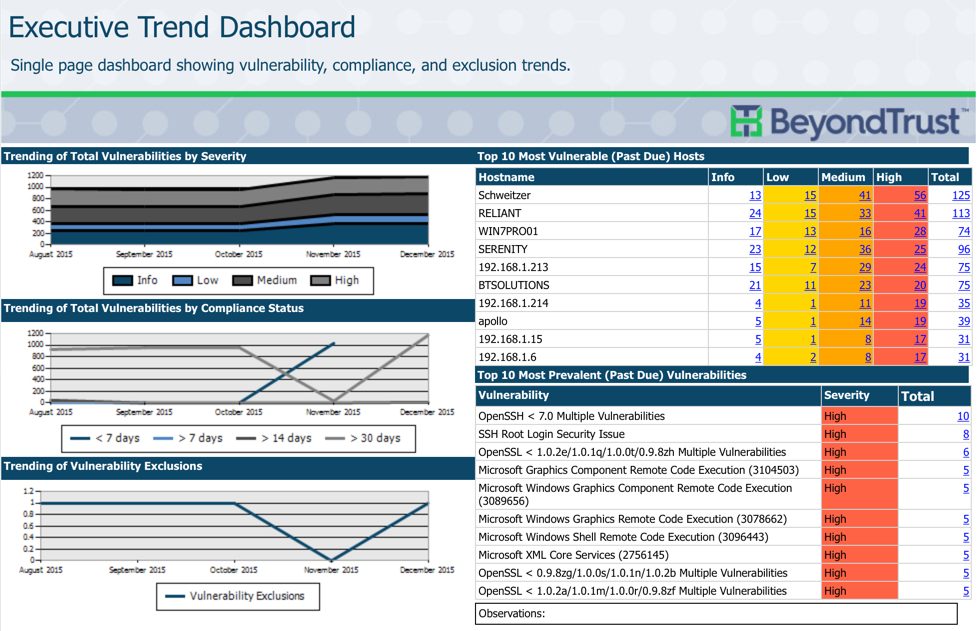
 Executive Trend Dashboards combine multiple metrics such as vulnerability, compliance and exclusion trends all in a single window, for quick review by executive team members.
Executive Trend Dashboards combine multiple metrics such as vulnerability, compliance and exclusion trends all in a single window, for quick review by executive team members.
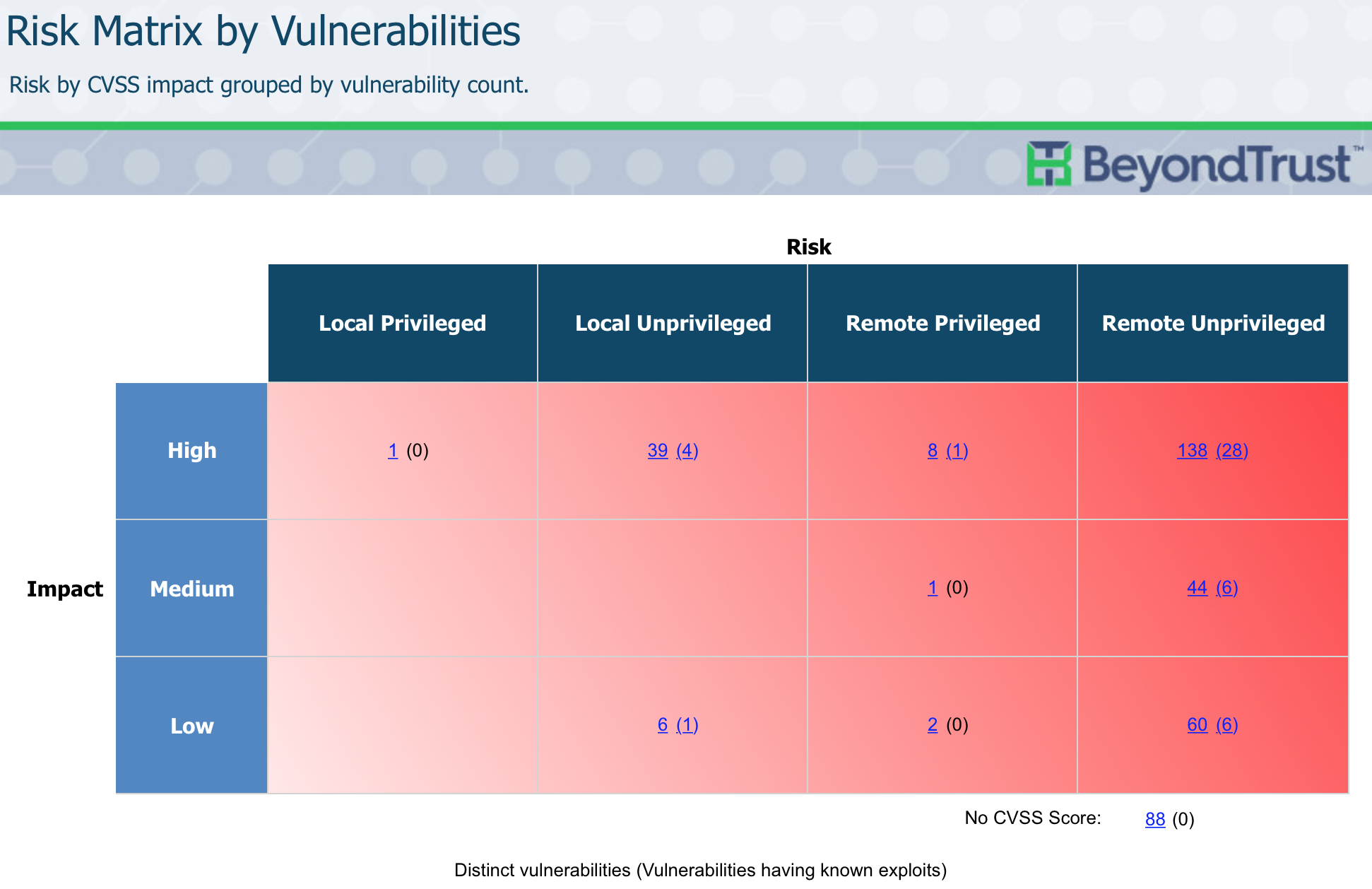
 In addition to over 270 standard reports, Retina CS gives you unmatched capabilities to build custom reports, with only the data and within only the context you specify – enabling you to communicate risk and share progress exactly the way you like.
Want to learn more about Retina’s award-winning features? Download our latest white paper, 10 Reasons to Rethink Your Vulnerability Management, and see how Retina’s cutting-edge capabilities can keep you steps ahead of the bad guys.
For more, contact us today!
In addition to over 270 standard reports, Retina CS gives you unmatched capabilities to build custom reports, with only the data and within only the context you specify – enabling you to communicate risk and share progress exactly the way you like.
Want to learn more about Retina’s award-winning features? Download our latest white paper, 10 Reasons to Rethink Your Vulnerability Management, and see how Retina’s cutting-edge capabilities can keep you steps ahead of the bad guys.
For more, contact us today!

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








