 Last week, Equifax announced a data breach exposing more than 143 million records. Now, Equifax in Argentina is the latest victim to poor cybersecurity hygiene, web application assessments, and insufficient vulnerability management.
As reported by BBC News and Krebs on Security, the Argentina based Equifax internal website was identified as having a default username of “admin” and password of “admin” exposed to internal employees and available to anyone within Equifax Argentina that could guess the basic, default combination. The data behind the portal was sensitive to say the least. It contained disputes and claims against Equifax lodged by Argentinians (regardless of email, phone, or fax) and their DNI number (documento nacional de identidad) — a non-private version of the United States Social Security Number (SSN). This raises high concerns around the policies and procedures Equifax used to store, process, and secure sensitive information internally as well as data lost during the breach earlier this month.
Now that the facts are out, there are several really difficult concepts to deal with. First, the internal website at Equifax Argentina would have failed a PCI Assessment as early as 1999. As illustrated below from BeyondTrust’s Retina CS Enterprise Vulnerability Management, multiple CVE’s from 1999 covering NT Authentication for accounts and passwords are in violation of using default credentials, and accounts and usernames with the same string.
Last week, Equifax announced a data breach exposing more than 143 million records. Now, Equifax in Argentina is the latest victim to poor cybersecurity hygiene, web application assessments, and insufficient vulnerability management.
As reported by BBC News and Krebs on Security, the Argentina based Equifax internal website was identified as having a default username of “admin” and password of “admin” exposed to internal employees and available to anyone within Equifax Argentina that could guess the basic, default combination. The data behind the portal was sensitive to say the least. It contained disputes and claims against Equifax lodged by Argentinians (regardless of email, phone, or fax) and their DNI number (documento nacional de identidad) — a non-private version of the United States Social Security Number (SSN). This raises high concerns around the policies and procedures Equifax used to store, process, and secure sensitive information internally as well as data lost during the breach earlier this month.
Now that the facts are out, there are several really difficult concepts to deal with. First, the internal website at Equifax Argentina would have failed a PCI Assessment as early as 1999. As illustrated below from BeyondTrust’s Retina CS Enterprise Vulnerability Management, multiple CVE’s from 1999 covering NT Authentication for accounts and passwords are in violation of using default credentials, and accounts and usernames with the same string.
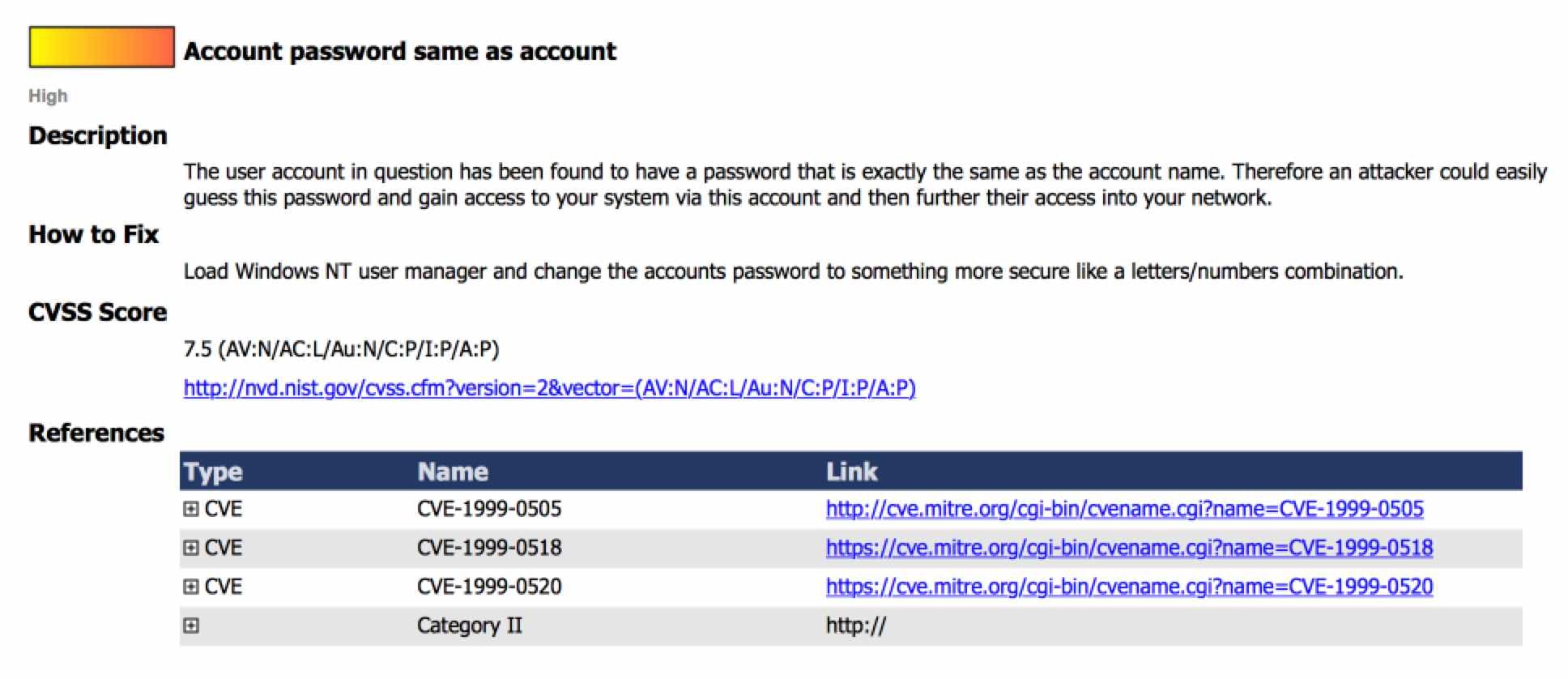 How could this application have every passed an audit? In addition, CWE calls out audit CWE-521: Weak Password Requirements specifically for web applications if the username and password was form based and not NT challenge and response. This clearly demonstrates to me, in conjunction to the previous breach, that as a tier one PCI merchant, they could not even manage their own regulatory compliance initiatives internally but provided credit reporting services to everyone else.
There is a second part to this finding in Argentina that is even more disturbing, the protection of privileged account access. This revelation of a default admin account and password combination violates multiple sections of the PCI DSS requirements.
How could this application have every passed an audit? In addition, CWE calls out audit CWE-521: Weak Password Requirements specifically for web applications if the username and password was form based and not NT challenge and response. This clearly demonstrates to me, in conjunction to the previous breach, that as a tier one PCI merchant, they could not even manage their own regulatory compliance initiatives internally but provided credit reporting services to everyone else.
There is a second part to this finding in Argentina that is even more disturbing, the protection of privileged account access. This revelation of a default admin account and password combination violates multiple sections of the PCI DSS requirements.
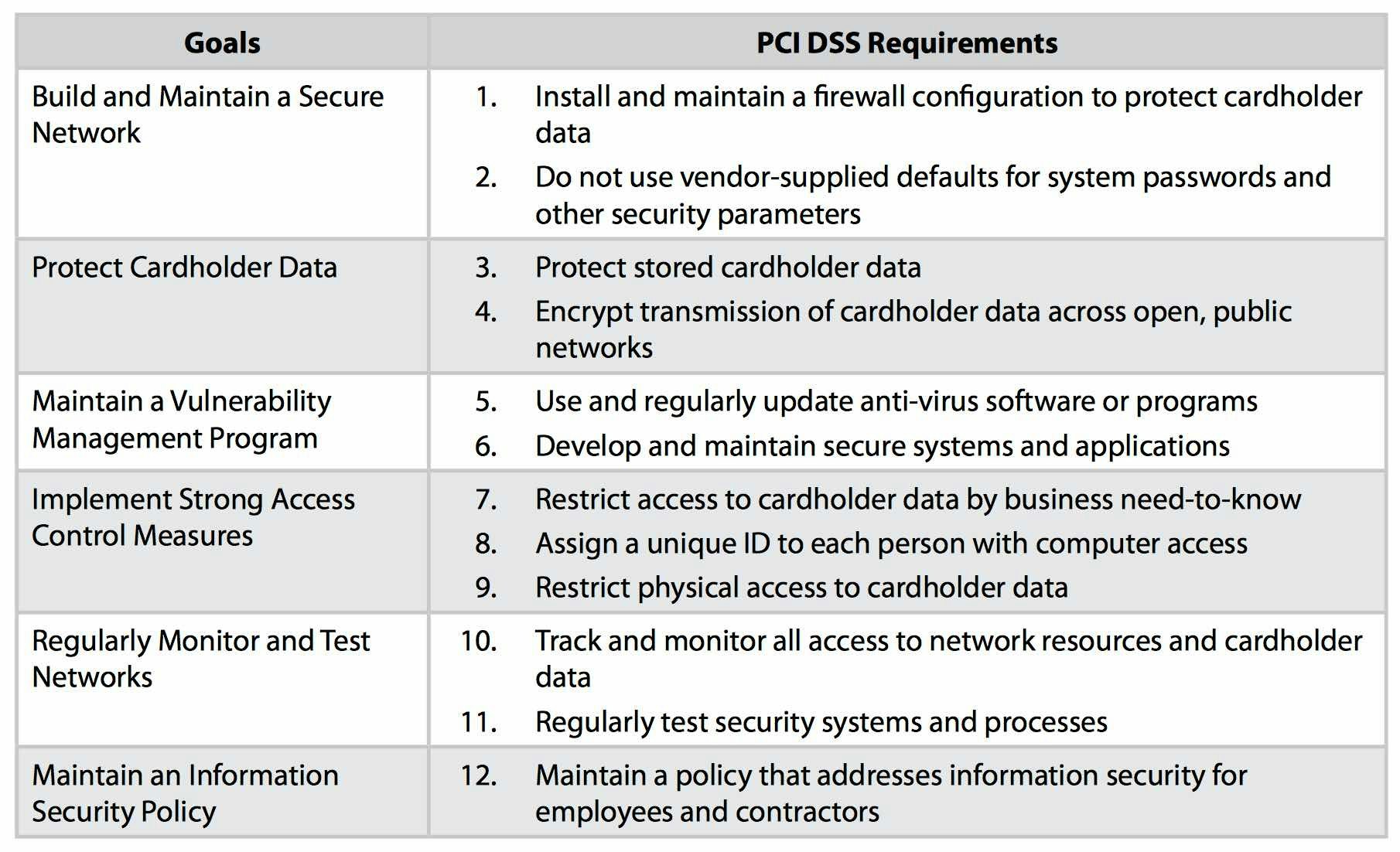 Bluntly speaking, and a very conservative approach finds violations in Sections 2, 3, 6, 7, 8 and 10. If this account was truly an admin, why wasn't privileged access management or even multi-factor authentication used to secure it? Monitoring privileged access is fundamental part of all cybersecurity programs and yet Equifax failed again. The threat from an insider attack or the leakage of sensitive information was huge and who knows how long the exposure has been present.
Unfortunately, we have seen this time and time again. Organizations failing to practice basic cybersecurity hygiene even for the basics of vulnerability management and privileged access management. Maybe I expect more as a vendor in the cybersecurity market. I know no company is perfect. I know every business can improve. But to have security problems at this basic level of CVE’s from 1999 and default admin credentials is shameful. It's time for all organizations to make sure the basics are covered
At BeyondTrust, we can help with the basics of cybersecurity including vulnerability management and privileged access management. Be sure to check back for more information on the Equifax data breach or contact us for a strategy session today.
Bluntly speaking, and a very conservative approach finds violations in Sections 2, 3, 6, 7, 8 and 10. If this account was truly an admin, why wasn't privileged access management or even multi-factor authentication used to secure it? Monitoring privileged access is fundamental part of all cybersecurity programs and yet Equifax failed again. The threat from an insider attack or the leakage of sensitive information was huge and who knows how long the exposure has been present.
Unfortunately, we have seen this time and time again. Organizations failing to practice basic cybersecurity hygiene even for the basics of vulnerability management and privileged access management. Maybe I expect more as a vendor in the cybersecurity market. I know no company is perfect. I know every business can improve. But to have security problems at this basic level of CVE’s from 1999 and default admin credentials is shameful. It's time for all organizations to make sure the basics are covered
At BeyondTrust, we can help with the basics of cybersecurity including vulnerability management and privileged access management. Be sure to check back for more information on the Equifax data breach or contact us for a strategy session today.

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.








