 The U.S. federal government last week moved to ban the use of a Russian brand of security software, Kaspersky Lab products, by federal agencies amid concerns the company has possible links to Russian state-sponsored cyberespionage activities.
For organizations concerned about how this ban will affect their IT operations, BeyondTrust can assist U.S. federal government agencies in discovering known and unknown assets (i.e. shadow IT) with Kaspersky Lab products installed on them. In four simple steps using Retina CS, U.S. federal government agencies can find and remove the banned software and be compliant per the U.S. federal government mandate.
To find and remove Kaspersky products, BeyondTrust customers should follow these step-by-step instructions:
Discover instances of Kaspersky Lab within your environment using BeyondTrust Retina CS
1) Log into the BeyondTrust IT Risk Management Platform (BeyondInsight)
2) Automate the process of discovering instances of Kaspersky Lab products, and automate certain actions taken when an instance is found using BeyondTrust Smart Rules.
The U.S. federal government last week moved to ban the use of a Russian brand of security software, Kaspersky Lab products, by federal agencies amid concerns the company has possible links to Russian state-sponsored cyberespionage activities.
For organizations concerned about how this ban will affect their IT operations, BeyondTrust can assist U.S. federal government agencies in discovering known and unknown assets (i.e. shadow IT) with Kaspersky Lab products installed on them. In four simple steps using Retina CS, U.S. federal government agencies can find and remove the banned software and be compliant per the U.S. federal government mandate.
To find and remove Kaspersky products, BeyondTrust customers should follow these step-by-step instructions:
Discover instances of Kaspersky Lab within your environment using BeyondTrust Retina CS
1) Log into the BeyondTrust IT Risk Management Platform (BeyondInsight)
2) Automate the process of discovering instances of Kaspersky Lab products, and automate certain actions taken when an instance is found using BeyondTrust Smart Rules.
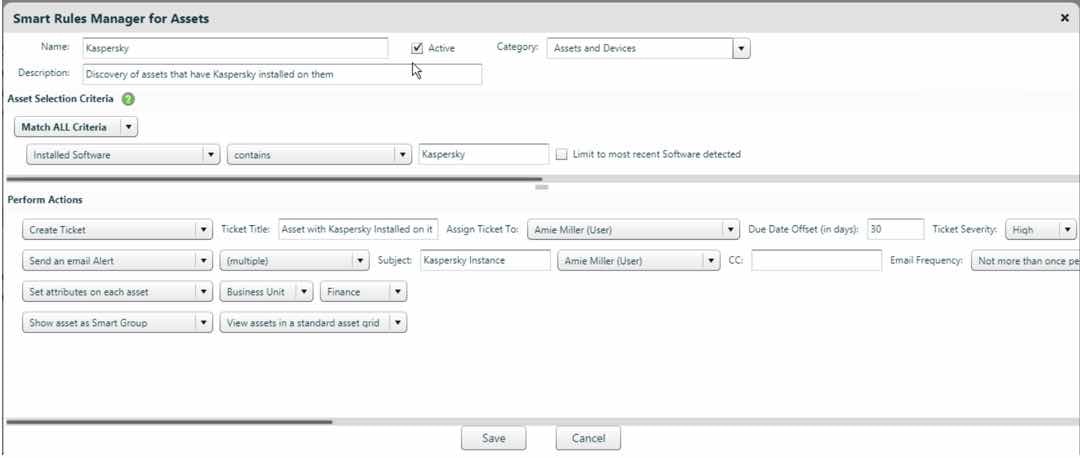
| 1. Click on assess (vulnerability scan) or assets or navigate to smart groups |
| 2. Click on manage smart rules |
| 3. Under smart rules manager for assets click on new button at the bottom |
| 4. Provide a name for the rule i.e. Kaspersky |
| 5. Choose assets and devices from the category drop down |
| 6. Description (optional) i.e. Discovery of assets that have Kaspersky installed on them |
| 7. Under sub heading “asset selection criteria” |
| 8. Choose match ALL criteria |
| 9. Installed software |
| 10. “contains” |
| 11. Type in “Kaspersky” or applicable Kaspersky Lab product SW package name |
| 12. Uncheck limit to most recent software detected |
- The creation of a help desk ticket with the pertinent attributes such as who to assign the ticket to, due date offset, severity, email alert
- Export of data to ServiceNow or BMC Remedy
- Send email alert
- Setting of asset attributes – business unit, criticality, geography, and manufacture
- Logically group affected assets into a collection
 3) Once the smart rule is created you can run a Software Report scan against it to discover all the assets with Kaspersky Lab products on them within your environment, or run a Software Report scan on various IP address groups within your environment. Any asset discovered within your environment will be automatically assigned to the smart group and have the action performed on it as outlined within the smart rule.
Note – BeyondTrust common practice is to run a scan with privileged credentials for best results.
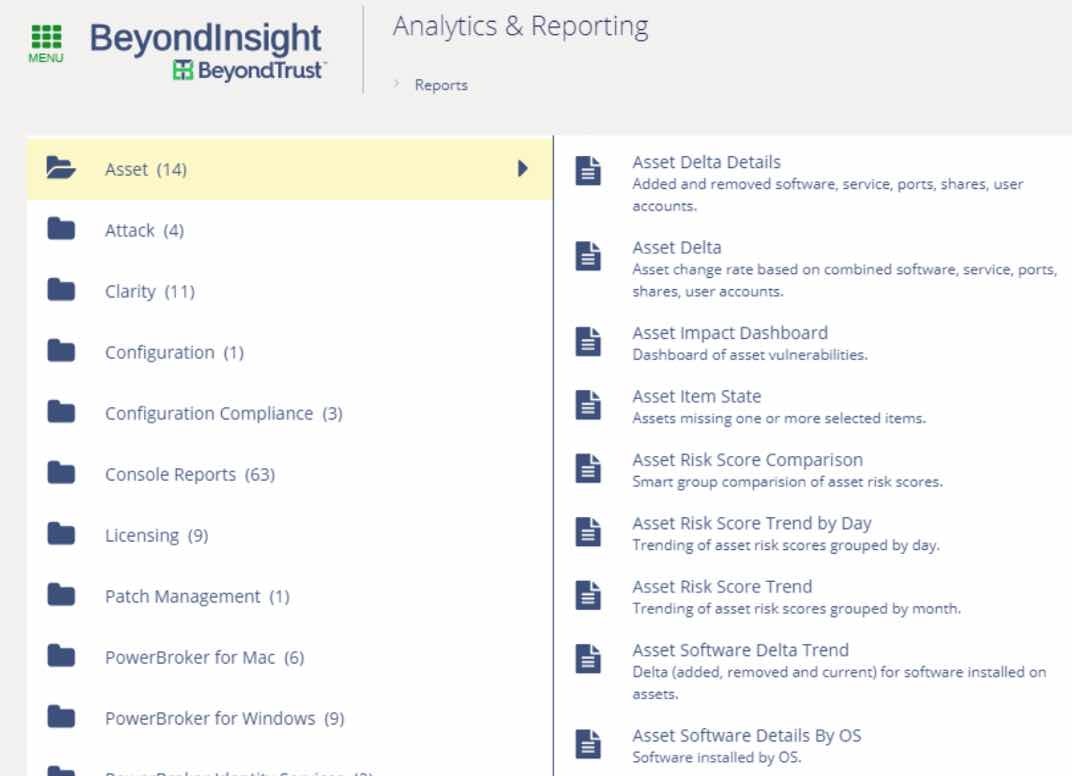
4) Once ALL (known/unknown) of the assets with Kaspersky Labs are discovered within your environment, BeyondTrust – by means of its robust reporting functionality, Analytics and Reporting – will allow you to systematically track progress by using one of its 270+ reports such as the report titled Asset Software Delta Trend. You will be able to display the changes (added, removed and current) in the software installed on the selected assets.
For a representation of this capability, please see the screenshot below.
3) Once the smart rule is created you can run a Software Report scan against it to discover all the assets with Kaspersky Lab products on them within your environment, or run a Software Report scan on various IP address groups within your environment. Any asset discovered within your environment will be automatically assigned to the smart group and have the action performed on it as outlined within the smart rule.
Note – BeyondTrust common practice is to run a scan with privileged credentials for best results.
4) Once ALL (known/unknown) of the assets with Kaspersky Labs are discovered within your environment, BeyondTrust – by means of its robust reporting functionality, Analytics and Reporting – will allow you to systematically track progress by using one of its 270+ reports such as the report titled Asset Software Delta Trend. You will be able to display the changes (added, removed and current) in the software installed on the selected assets.
For a representation of this capability, please see the screenshot below.
 Next Steps
If your organization must be compliant with the mandate to remove Kaspersky Lab products, or would like to see a demonstration on the critical discovery and automation capabilities of Retina CS Enterprise Vulnerability Management, contact us today.
Next Steps
If your organization must be compliant with the mandate to remove Kaspersky Lab products, or would like to see a demonstration on the critical discovery and automation capabilities of Retina CS Enterprise Vulnerability Management, contact us today.

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








