
There are many good reasons for wanting to stamp out today’s known vulnerabilities – securing intellectual property, ensuring business availability, protecting customer privacy, and complying with regulatory standards.
Another reason, albeit somewhat pessimistic, would be to make room for the next wave of vulnerabilities, lurking just around the corner. As the attack surface continues to expand and become more diverse, we will likely be faced with new threats that make us rethink our approach to managing vulnerabilities. Here are just a few to consider.
Internet of Things (IoT)
While the Internet of Things, sometimes referred to tongue-in-cheek as the “Insecurity of Things”, is still emerging, the threats presented by its rapidly expanding cyberattack surface are no laughing matter.
Intel recently reported that, by 2020, an estimated 200 billion smart devices will comprise the internet of things. Everything from cars, IP cameras, and DVRs to medical devices and baby monitors. And, if you think attacks on these types of devices are still science fiction, consider the recent Distributed Denial of Service (DDoS) attack on Dyn that caused a massive internet outage across the United States. Or the same Mirai IoT botnet that took the entire country of Liberia offline.
Malware Gone Mobile
While, to date, most attacks on smartphones have been of the ad-hoc variety, maturity in mobile malware, combined with an increasing number of Android and IOS vulnerabilities, are making conditions favorable for more frequent attacks.
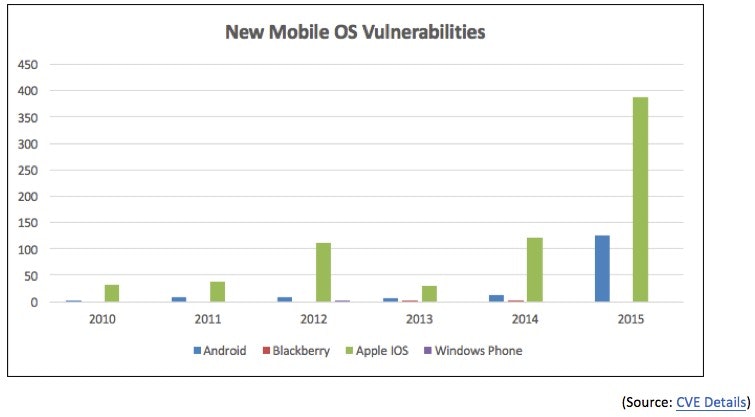
Last year, we witnessed the advent of overlay malware – malicious programs that use screen switching and pop-up tricks to fool users and snip sensitive data, including passwords, account information, and payment card details, directly from mobile phones. Some experts, including the folks at IBM X-Force, say overlay malware represents “the next quantum leap in mobile threats.”
Hardware-based Attacks
As devices, and their associated operating systems and applications, become more hardened, attackers will look lower down the stack for vulnerabilities to exploit – including a device’s firmware, and BIOS. While evidence of such attacks is still rare, last year, Intel’s Advanced Threat Research team discovered what appears to be the first of its kind UEFI rootkit – which has already been traced to attacks observed in the wild.
If we cannot address today’s known vulnerabilities, how can we as a security community expect to tackle billions of IoT devices, malware for mobile phones and vulnerabilities buried deep within hardware?
It’s time to change the game!
By mobilizing our “security villages” (yes you have one), and automating their interactions, we can collect data from a variety of trusted sources, correlate it into a clear picture of risk, and take swift and decisive actions to mitigate vulnerabilities and threats. Connect threat and vulnerability intelligence. That’s how we flip the game on our adversaries and take control of vulnerabilities that have been plaguing us for more than a decade.
Want to take your vulnerability management game to the next level? Download our latest white paper, Change the Game in Vulnerability Management, to discover how orchestrating your cyber defenses can keep you steps ahead of the bad guys.
For more, contact us today!

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








