Fifteen years ago there was a revolution in information technology operations. Different teams that managed networks and systems merged their practices and technology under frameworks like Computer Associates Unicenter and IBM Tivoli. Today, these solutions have evolved to CA Spectrum, SolarWinds, and SpiceWorks. These are all fantastic technologies that have proven that the fusion of information technology operations and network management could occur, and in fact are complementary when running from the same tool, same interface, and share information.
Now, fast forward to today and consider the concepts of vulnerability management and privileged identity management. Two very different teams and technology but unified in many concepts and well documented as best practices. Consider the SANS 20 Critical Security Controls:
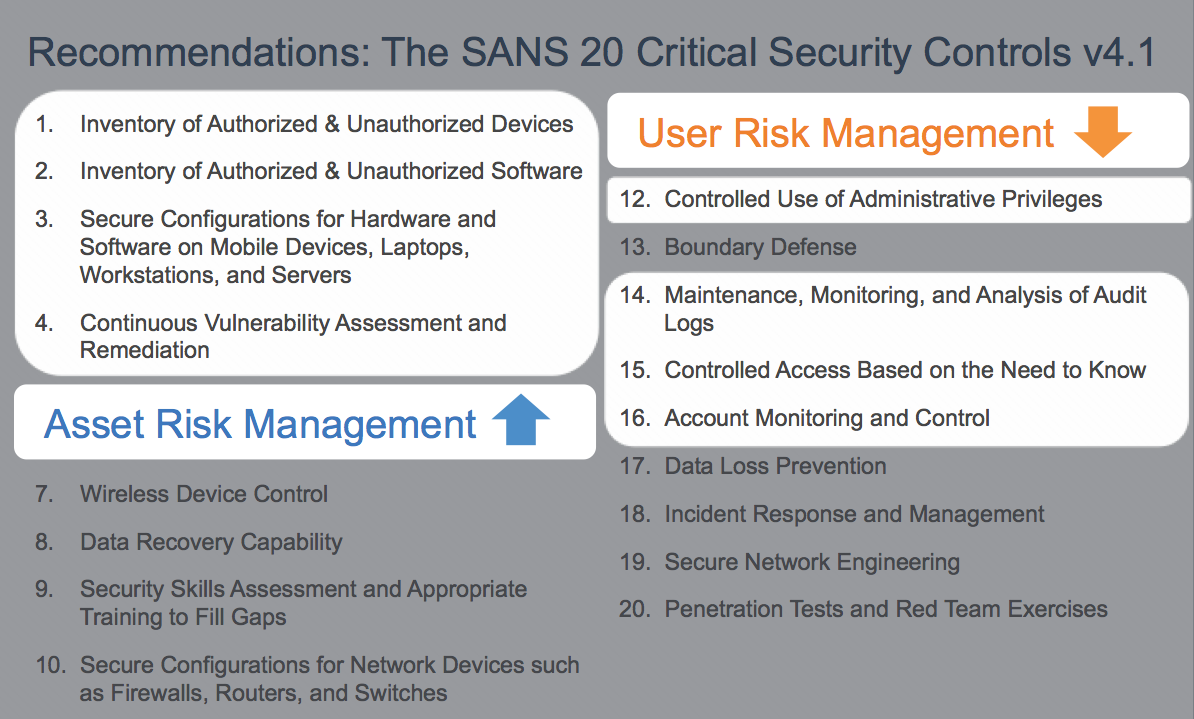
Asset and User Risk Management (Vulnerability and Privilege) occupy 8 of the 20 controls; 40%. Recently we hosted a webinar with SANS Analyst, Dr. Eric Cole who touched on just this; the 8 Critical Security Controls specifically designed to address user and asset-based risks. Access the recording here.
What if one platform can manage these disciplines in a single pane of glass and share common information? BeyondInsight represents the next generation of unification for tools for IT operations and security management teams. It capitalizes on what the industry already accepts for properly securing and maintaining assets and drives home the value with a single vendor, single solution, and lower total cost of ownership while doing a better job than any best-of-breed solutions for each discipline.
Here is how it works:
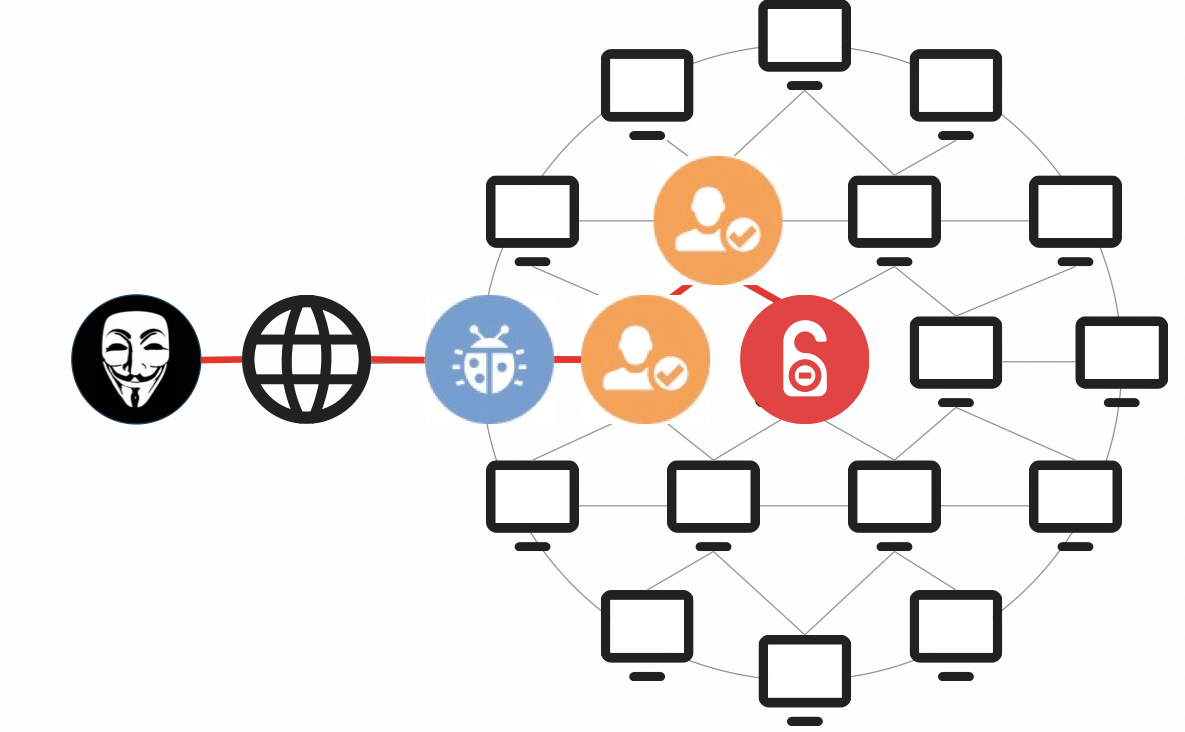
An external attacker might first take advantage of a vulnerability on a relatively low-level asset (maybe starting with phishing or another client-side attack). Often, that’s all they need to gain a foothold in the environment. In organizations with privilege management challenges, the attacker could then take advantage of excessive user privileges to traverse the network until they find high-value assets and data and potentially use a vulnerability along the way to gain access to the systems they wish to compromise. In either scenario, privileges and vulnerabilities go hand in hand in order for the attacker to successfully exploit the environment.
BeyondInsight unifies vulnerability and privileged access data together in one solution. The logging privileged access, controlling privileged users, securing administrative passwords, and assessing vulnerabilities all are displayed and reported in one coherent solution. Below is a screen shot from PowerBroker for Windows, "Risk Compliance Report", which fuses Windows Privileged Access to Applications Launched with Vulnerabilities in real-time!
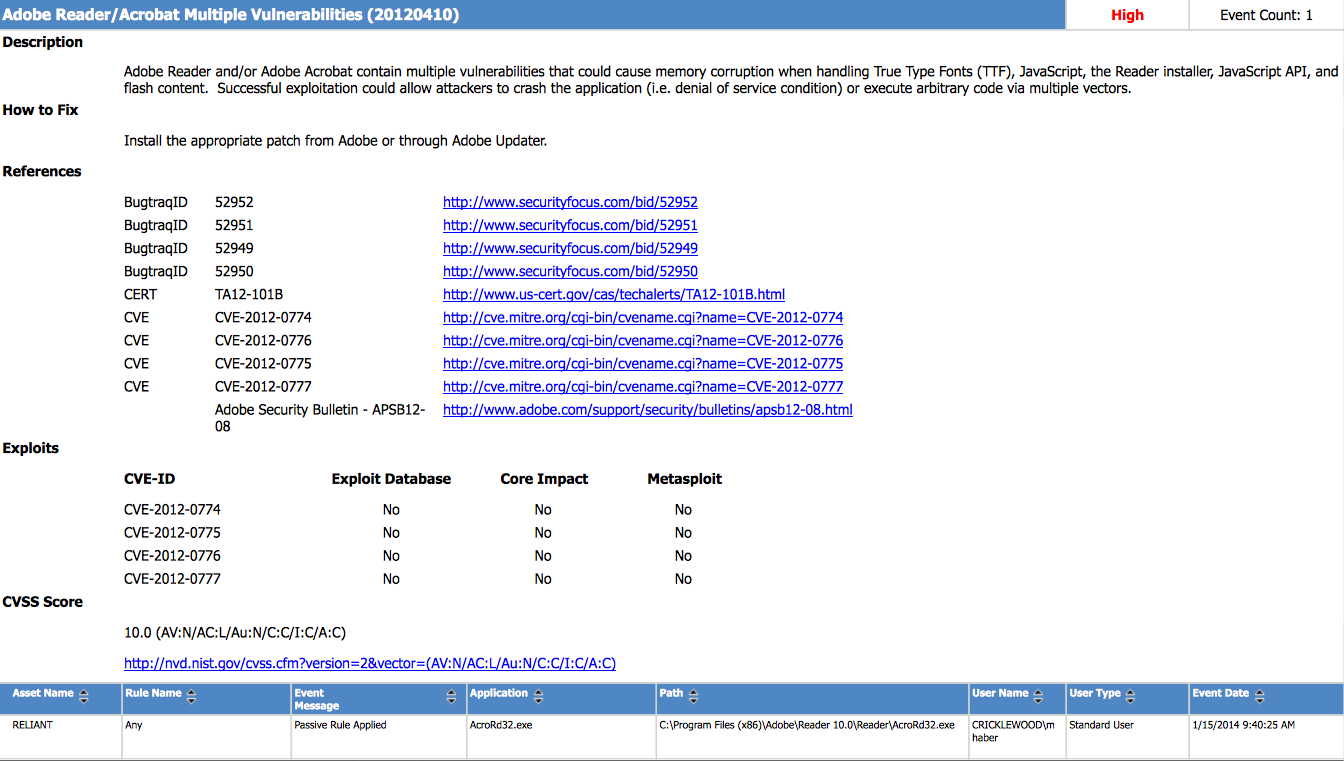
The report details that a vulnerable application was launched, what the user permissions were, the username, and all the vulnerability details. This unification is just one example of the new capabilities within BeyondInsight to unify vulnerability and privileged identity management. Whether you are using Retina for vulnerability management, PowerBroker for Privileged Account Management, or both, you will find that the data truly belongs hand-in-hand. In addition, considering recent attacks against Target, the NSA, and KickStarter; this technology is your best offense and defense from attacks that link operational weaknesses to vulnerabilities.
For more information on BeyondInsight, please click here. Our team is ready to help you manage your risks better than ever before. BeyondTrust, going Beyond Traditional Security.

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.








