Spring has sprung! Temperatures are finally headed in the right direction! It must be data breach report season again! Verizon released its annual investigations report yesterday full of insights from 2014 security incidents and associated data breaches.
This year’s version offered a new model to calculate data breach costs (which will make reading the next Ponemon report all the more interesting), emphasized the importance of threat intelligence sharing, and offered new insights around before and beyond the breach, in addition to showcasing its nine incident classification patterns. As always, it was an informative and at times entertaining view into information security; although with few “wow” moments in this year’s edition.
I’ll dispense with a full review of the report; there are plenty of great reviews out there, like this one from searchsecurity.com. Instead, I want to talk about a few topics that stood out to me.
Breaches are increasing
The number of confirmed data breaches increased 55% vs. last year to 2,122. These numbers are a subset of overall security incidents, which increased 26% vs. last year to 79,790. (There were quite a few more data inputs and partners involved in the year’s study.)
Breaches resulting from insider misuse are increasing
This year’s data shows that 10.6% of confirmed data breaches resulted from insider misuse, up from 8% in 2013. The percentage of incidents that came from insider misuse was 20.6% up from 18% in 2013.
Breaches involving the end user are increasing, yet sys admins decreasing
This year’s report shows that more incidents involved the end user than ever before. Take a look at a comparison of the data vs. the 2013 data (published in spring 2014). Source: Verizon Data Breach Investigations Reports, 2015 and 2014.
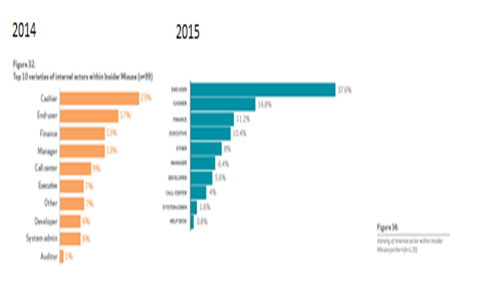
A whopping 37.6% of insider abuse incidents involved the end user in 2014, up from 17% last year. On the upside, however, only 1.6% of incidents were attributed to system administrators this year, down from 6% last year.
What to make of the data
While breaches – especially those from insider misuse – are increasing year over year, all of the tools, process and technology put in place to control and manage administrator access to systems and data might actually be delivering on their intended purposes.
But this focus has come at a cost – end users are increasingly emerging as a greater insider threat. Organizations must tackle this challenge immediately. But how?
Achieving control and accountability over privileged user activity
Seeing this year’s Verizon data doesn’t come as much of a surprise. After all, we did a study recently indicating that more than a fourth of companies have no controls over privileged access. How do you strike the balance between securing the organization’s critical data and systems while still enabling end user productivity?
1. Assemble cross-functional teams, avoiding a siloed view of privilege.
2. Deploy policies for controls and enforcement.
3. Prioritize implementation by the consequences of a breach.
4. Start with removing end-user privileges.
5. Address the risk of privileged password misuse.
Look for a comprehensive privileged account management solution that delivers on every privileged account management scenario, minimizes total cost of ownership, provides a fast time to value, and that provides information to make good risk-based decisions beyond just the privilege silo.
If you would like to learn more about BeyondTrust’s approach to privileged account management or get tips on how to get started with your privileged account management project, read this brief white paper or contact us today.

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








