Privileged Remote Access Jumpoint Guide: Unattended Access to Computers in a Network
With BeyondTrust Jump Technology, a user can access and control remote, unattended computers in any network. Jump Technology is integral to the BeyondTrust software offerings.
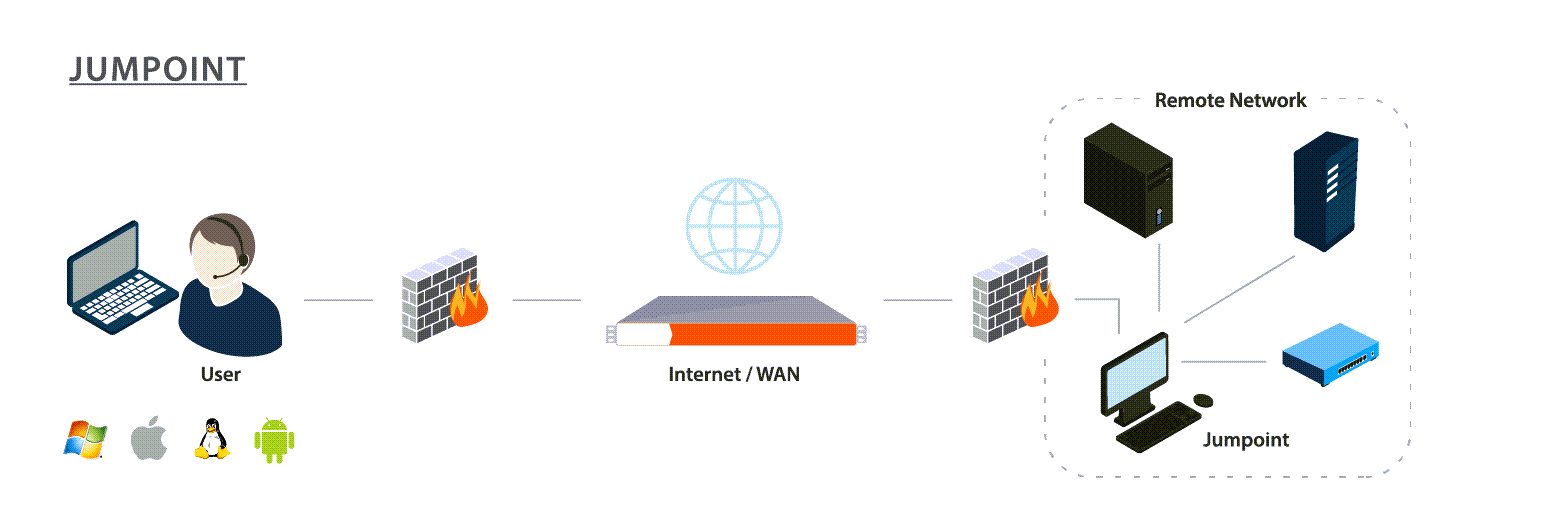
A Jumpoint acts as a conduit for unattended access to Windows and Linux computers on a known remote network. A single Jumpoint installed on a computer within a local area network is used to access multiple systems, eliminating the need to pre-install software on every computer you may need to access.
Within the local area network, the BeyondTrust user's computer can initiate a session to a Windows system directly without using a Jumpoint, if appropriate user permissions are enabled. A Jumpoint is needed only when the BeyondTrust user's computer cannot access the target computer directly.