Use Jump Items to Access Endpoints from the iOS Access Console
To access an individual endpoint without end-user assistance, install a Jump Item on that system from the Jump Clients page of the /login administrative interface. The following Jump Item types are supported by the mobile access console:
- Remote Jump
- Remote VNC
- RDP
- Shell Jump
Jump Items are listed in Jump Groups. If you are assigned to one or more Jump Groups, you can access the Jump Items in those groups, with the permissions assigned by your admin.
Your personal list of Jump Items is primarily for your individual use, although your team leads, team managers, and users with permission to see all Jump Items may have access to your personal list of Jump Items. Similarly, if you are a team manager or lead with appropriate permissions, you may see team members' personal lists of Jump Items. Additionally, you may have permission to access Jump Items in Jump Groups you do not belong to and personal Jump Items for non-team members.
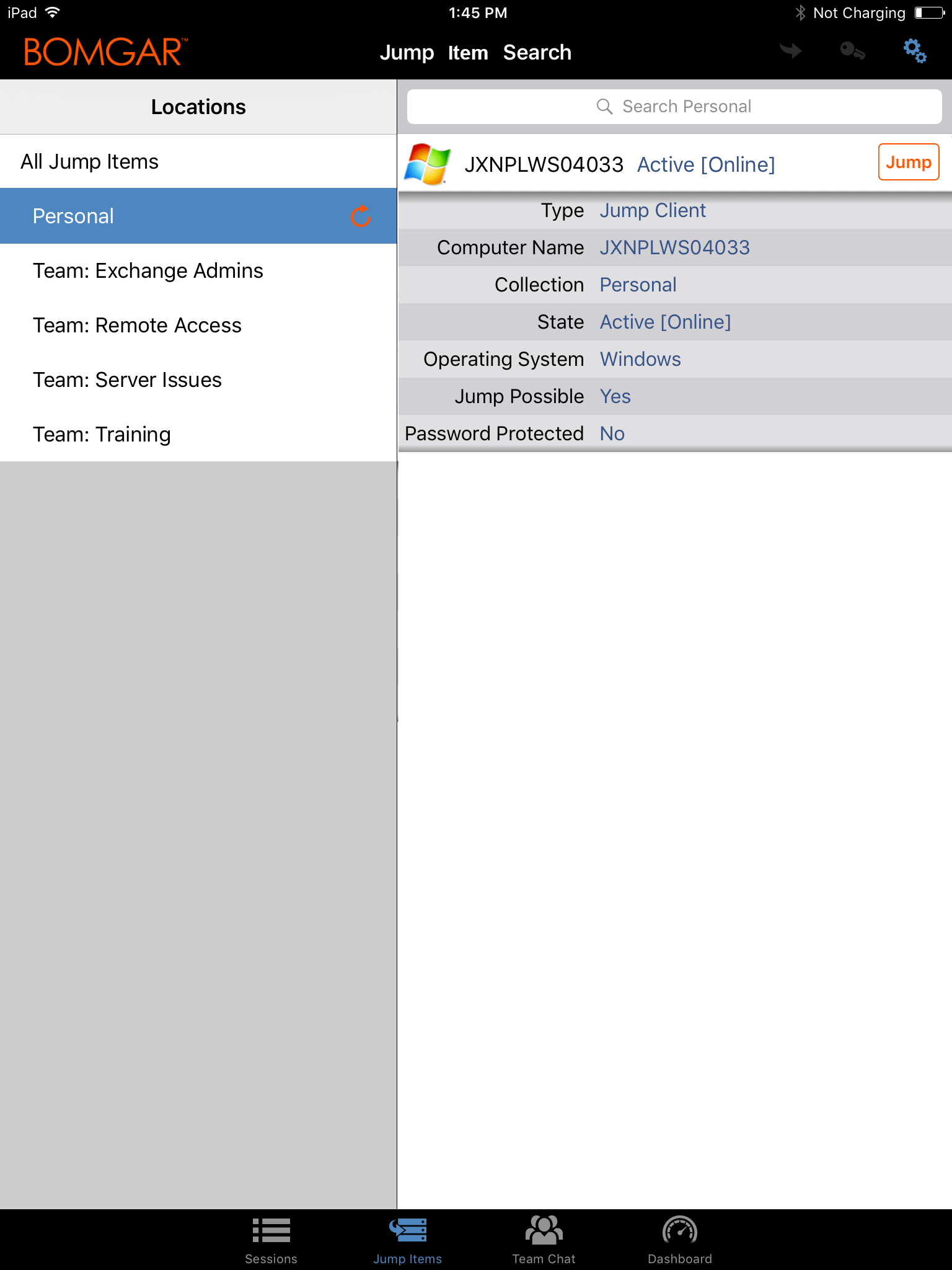
To locate a Jump Item, tap on the Jump Items tab at the top of the screen.
Select a location and touch the Refresh button. Once you have found the endpoint you wish to access, select the entry to view details.
Tap the Jump button to begin a session.
Depending on the permissions your administrator has set for your account, an end-user or third party may be prompted to accept or deny the session. If no response is received within a defined interval of time, the session will either start or cancel as set in your account permissions.
End-User and Third-Party Authorization
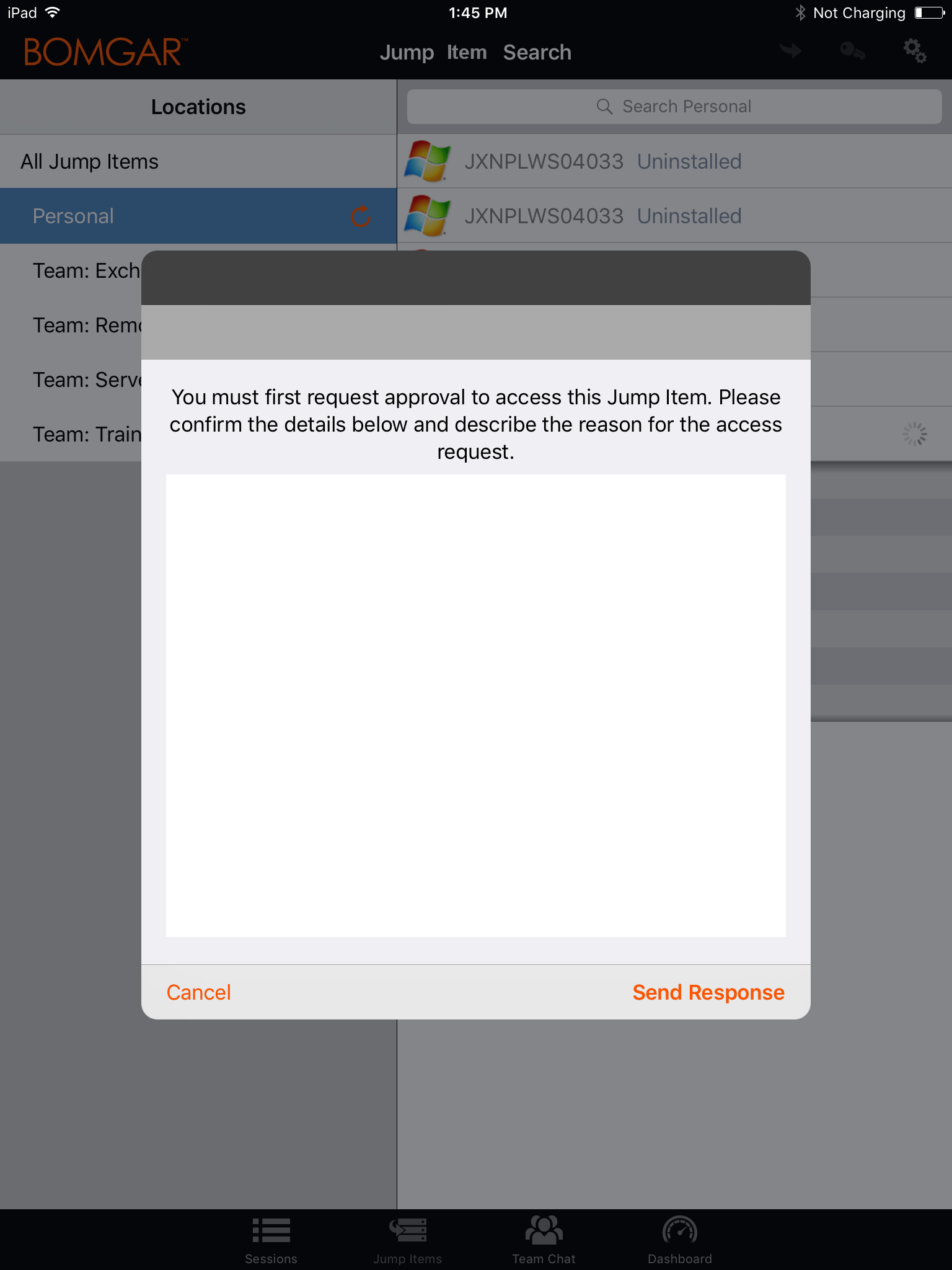
Depending on the configuration of Jump Items within the /login administrative interface, a Jump Item may have a Jump Policy associated with it, and the policy may define an authorization component that forces you to request permission from a third-party or an administrator before you are able to start an access session with the Jump Item.
For more information about how to configure third party and end-user notifications and approval, please see Jump Policies: Set Schedules, Notifications, and Approval for Jump Items.
After you have tapped the Jump button and requested access, a prompt appears, and you are required to enter a reason for wanting to access the system.
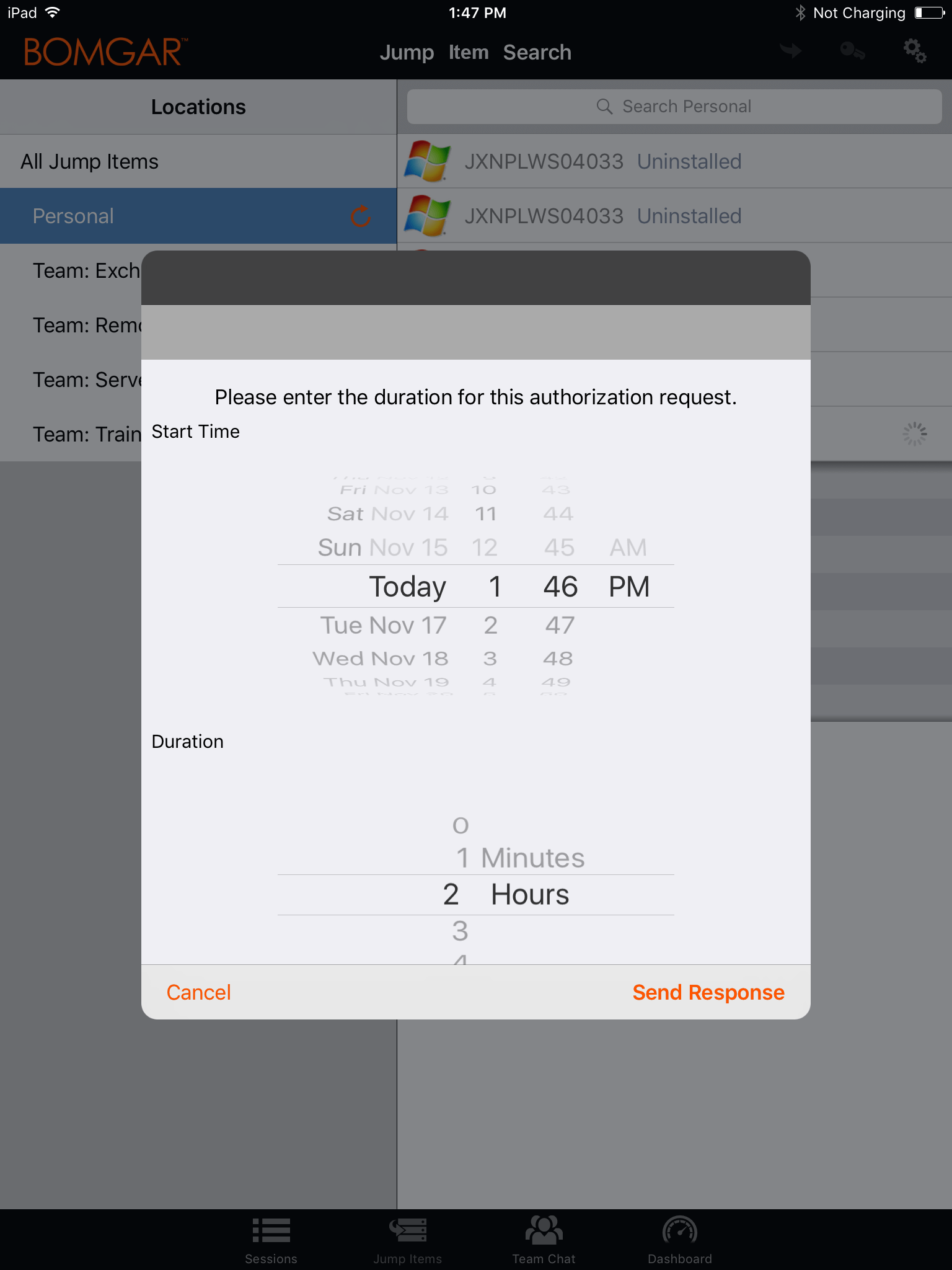
Next, you must indicate when and for how long you will be accessing the system.
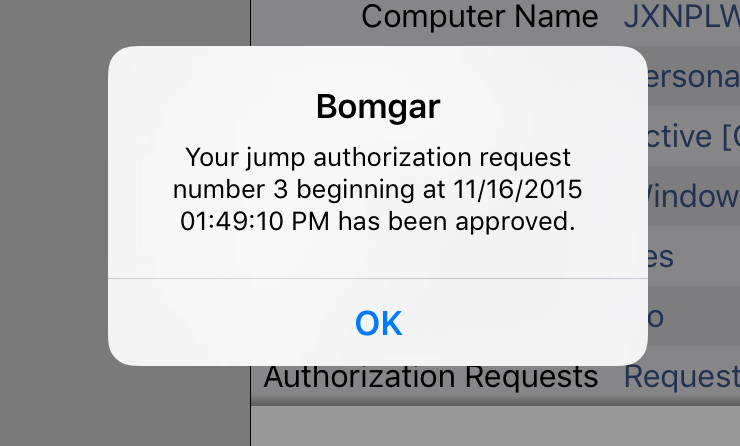
Once the request has been submitted, the third party or person responsible for approving access requests is alerted through an email notification and has the opportunity to accept or deny the request. Although other approvers can see the email address of the person who approved or denied the request, the requestor cannot.After permission has been determined, an authorization notification appears within the Jump Item's information displaying either approved or denied. If access is granted, you can tap the Jump button to begin accessing the system.
After tapping the Jump button, you are presented with a message asking if you would like to begin an access session. If you choose to begin the session, the approving party's comments appear, and you can continue accessing the system.
Automatic Log On Credentials for the Mobile Access Console
Credentials from the Endpoint Credential Manager can be used for RDP and for performing Remote Jump. If a user selects to Jump to a Remote Jump or Remote RDP and no automatic log on credentials are available, a username and password must be entered into the prompt before the access session can begin with the endpoint. If the /login administrative interface has been configured with automatic log on credentials and returns only one set of credentials as being available for a particular user and Jump Item, the credential request is skipped, and the single credential is used to start the session. If there is more than one credential configured in the /login administrative interface, the user has the choice either to choose credentials from the credential store or to enter their own credentials manually.
For more information on credential configuration and management, please see Security: Manage Security Settings.