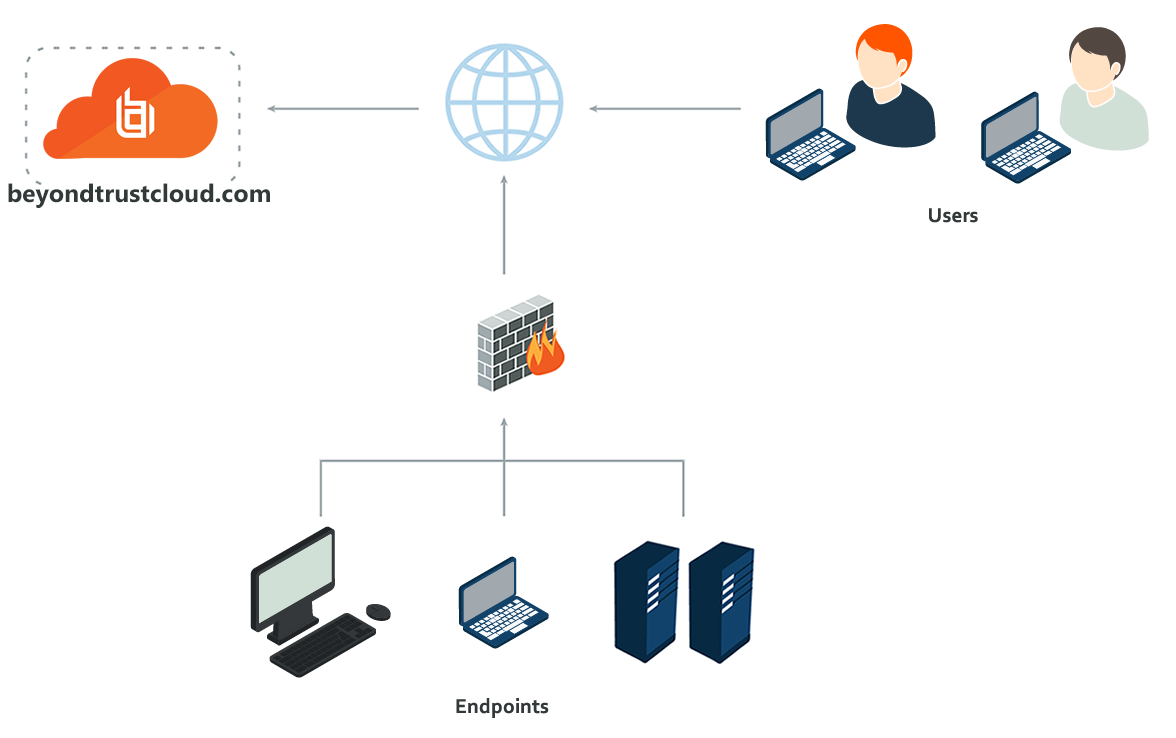
Review BeyondTrust Privileged Remote Access Cloud Network Infrastructure
The architecture of the BeyondTrust Privileged Remote Access application relies on the Privileged Remote Access cloud instance as a central routing point for all communications between application components. All sessions between users and remote systems occur through the server components that run on the B Series Appliance. To protect the security of the data in transit, Privileged Remote Access uses TLSv1.2 to encrypt all application communications.
Customers can configure the security features such that the Privileged Remote Access deployment complies with applicable corporate policies or regulations. Security features include role-based access control, secure password requirements, and a full audit trail.
Privileged Remote Access enables remote control by creating a remote outbound connection from the endpoint system to the Privileged Remote Access cloud instance. The cloud site is designed and tested to ensure it works properly and securely in the cloud infrastructure. Since all Privileged Remote Access sessions are initiated via outbound connections from the client to the B Series Appliance, it is possible to remotely control computers using Privileged Remote Access through firewalls.
Review BeyondTrust Appliance B Series Network Infrastructure
Each Privileged Remote Access cloud site comes with a subdomain of the BeyondTrust cloud DNS address, such as yoursite.beyondtrustcloud.com. If customers prefer to use their company web address with their own SSL certificate, they can use a Canonical Name (CNAME) record to point the default site address to the preferred address.
Since this site accesses the /login interface, a simple yet descriptive name is the best practice. For example, a company named Smithson might use access.smithson.com for their CNAME record.
Review Sample Firewall Rules for Cloud Deployments
Below are example firewall rules for use with Privileged Remote Access Cloud, including port numbers, descriptions, and required rules.
| Firewall Rules | |
|---|---|
| Internal Network to the PRA Cloud Instance | |
| TCP Port 443 (required)* | Used for all session traffic. |
| PRA Cloud Instance to the Internal Network | |
| TCP Port 25, 465, or 587 (optional) | Allows the B Series Appliance to send admin mail alerts. The port is set in SMTP configuration. |
| TCP Port 443 (optional) | B Series Appliance to web services for outbound events. |
For information on setting Syslog over TLS, please see Appliance Administration: Set Syslog over TLS. UDP/514 and/or TCP/514 for Syslog server on internal network is optional.