Configure the Server for Disconnected Account Management
On the server where you'll set up disconnected account management (DAM), make sure you have the Privileged Identity management console and the web service installed. These components hold the protected secret data for endpoints and distribute the shared secrets. You can manage the disconnected password recovery portal through the web interface or web service.
The DAM web service is installed as part of the web service installation. For more information, please see Install the Web Service.
After you've installed the DAM web service, you can access the DAM web service on its host at:
https://serverName/ERPMWebService/OfflineUpdateWebService.svc
You must enable the web service host for anonymous authentication. If the web service is configured for integrated authentication or certificate authentication, the DAM feature will not work. If needed, you can make a copy of the web service files in a new directory and publish it in IIS with anonymous authentication. Be sure to configure the correct web service web.config file for anonymous authentication.
To enable disconnected account management, open the Privileged Identity management console and follow these steps:
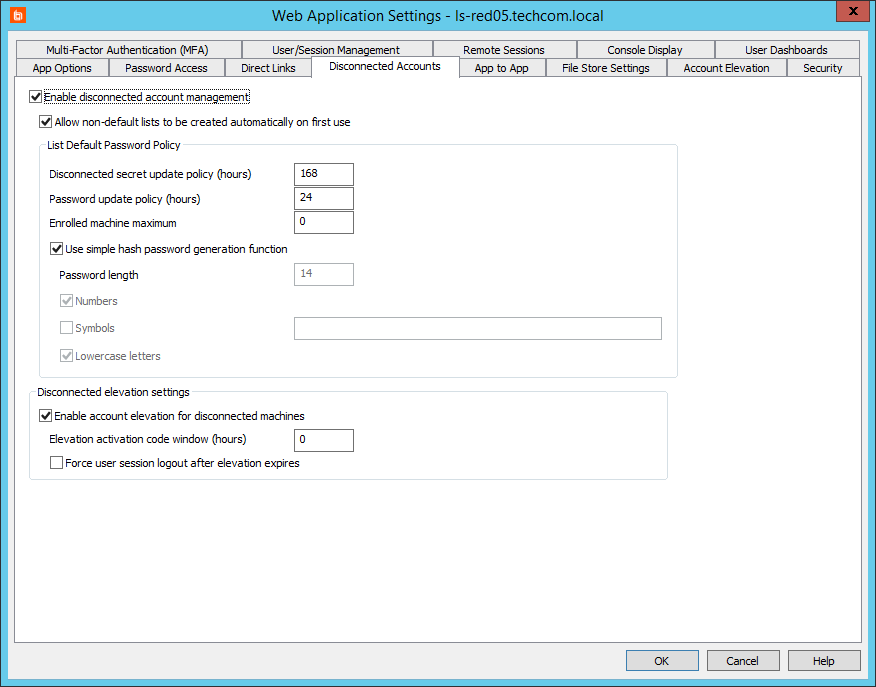
- Select Manage Web App from the left action pane.
- Select the web application instance where you want to enable DAM, and click Edit.
- Click Yes to overwrite the current settings.
- Select the Disconnected Accounts tab.
- Check Enable disconnected account management.
- Allow non-default lists to be created automatically on first use: If you select this option, then if a new endpoint attempts to enroll with a list ID that does not yet exist, a new list is automatically created with the endpoint added as a member.
List Default Password Policy
- Disconnected secret update policy: Set how often a new secret should be generated on the server. The next time the managed system connects to the web service, if the secrets are mismatched, the managed system receives the latest secret.
- Password update policy: Set how often a new derived password should be generated.
- Enrolled machine maximum: Set the number of machines that can derive passwords from one secret. It is a best practice to divide systems into smaller management sets when dealing with large networks.
- Use simple hash password generation function: If you select this option, then a password derived from the client secret will be a 14-character, random string of uppercase letters, lowercase letters, and numbers.
If you do not select this option, then set the following options for passwords derived from the client secret:
- Password length: Set how many characters to include in the password. The maximum is 127 characters.
- Numbers: Set if the password can contain numbers.
- Symbols: Set if the password can contain special characters. You can leave the text field blank to allow all possible symbols, or you can define an allowed list of symbols.
Some databases accept only the special characters hash (#), underscore (_), and dollar sign ($)
- Lowercase letters: Set if the password can contain lowercase letters.
Disconnected Elevation Settings
- Enable account elevation for disconnected machines: If you select this option, you can elevate a user account to a predefined group on an offline, managed machine. The managed machine does not have to join the network to allow the user to be elevated.
- Elevation activation code window: Set how long an elevation code should last.
This code window is not related to how long an elevation lasts. The elevation window is set at the endpoint client. As long as the elevation begins while the code is valid, the elevation can continue past the code expiration.
- Force user session logout after elevation expires: After an account has been de-elevated, you can force the end user to be logged off the managed system.
- Once you've finished configuring these settings, click OK.
This configuration is the global default. To access the global policy settings in the web app, select Settings > Site Settings, and then scroll down to the Disconnected Account Management section.
In the web app, you can modify this configuration per list. Doing so overrides the defaults and applies the new settings to the specific list and all machines under that list. You may also modify the configuration per endpoint system.
All settings are stored on the server and updated to the managed node when the node connects to the web service.