Use the Splunkbase App for BeyondInsight Endpoint Privilege Management
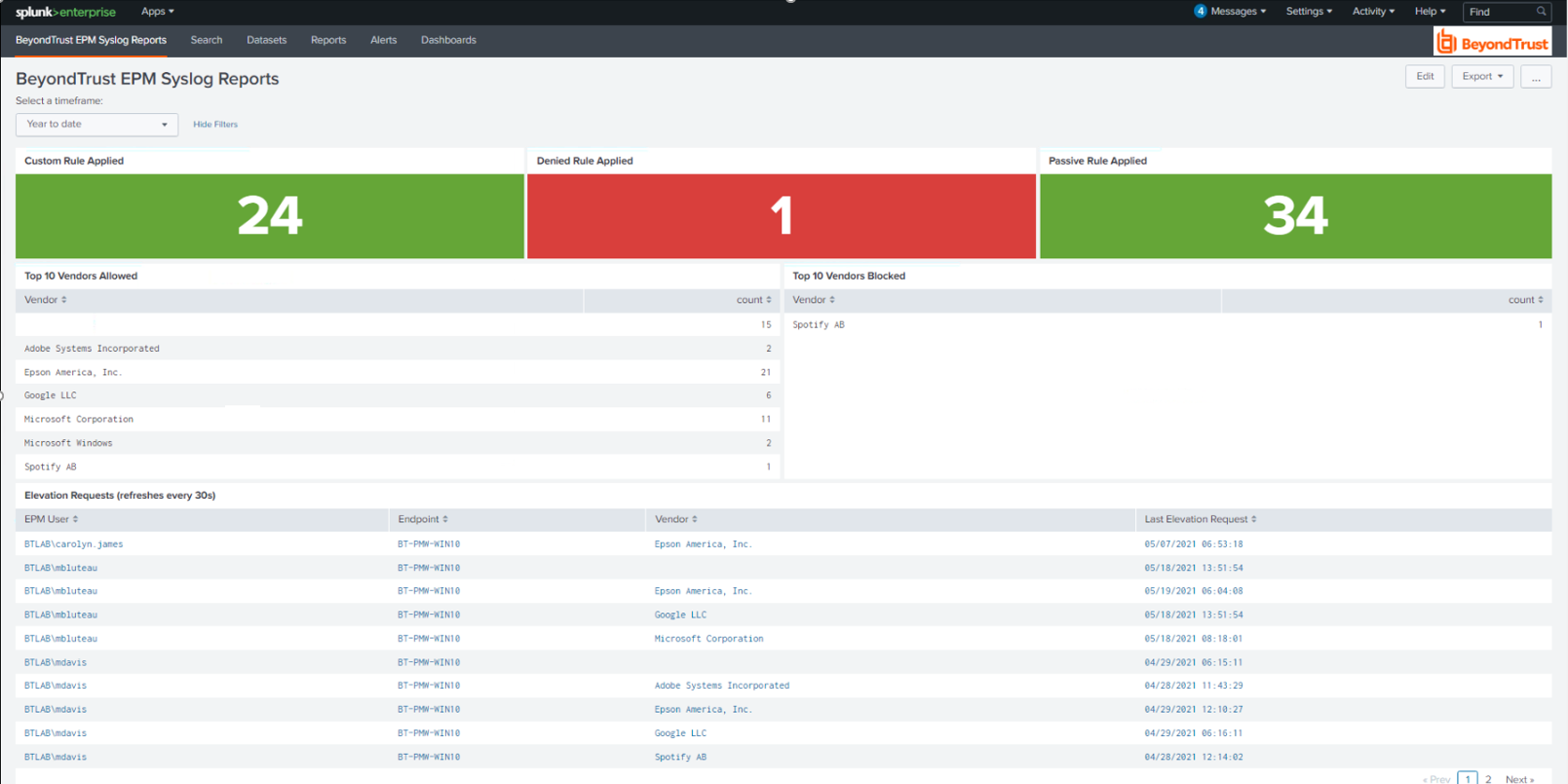
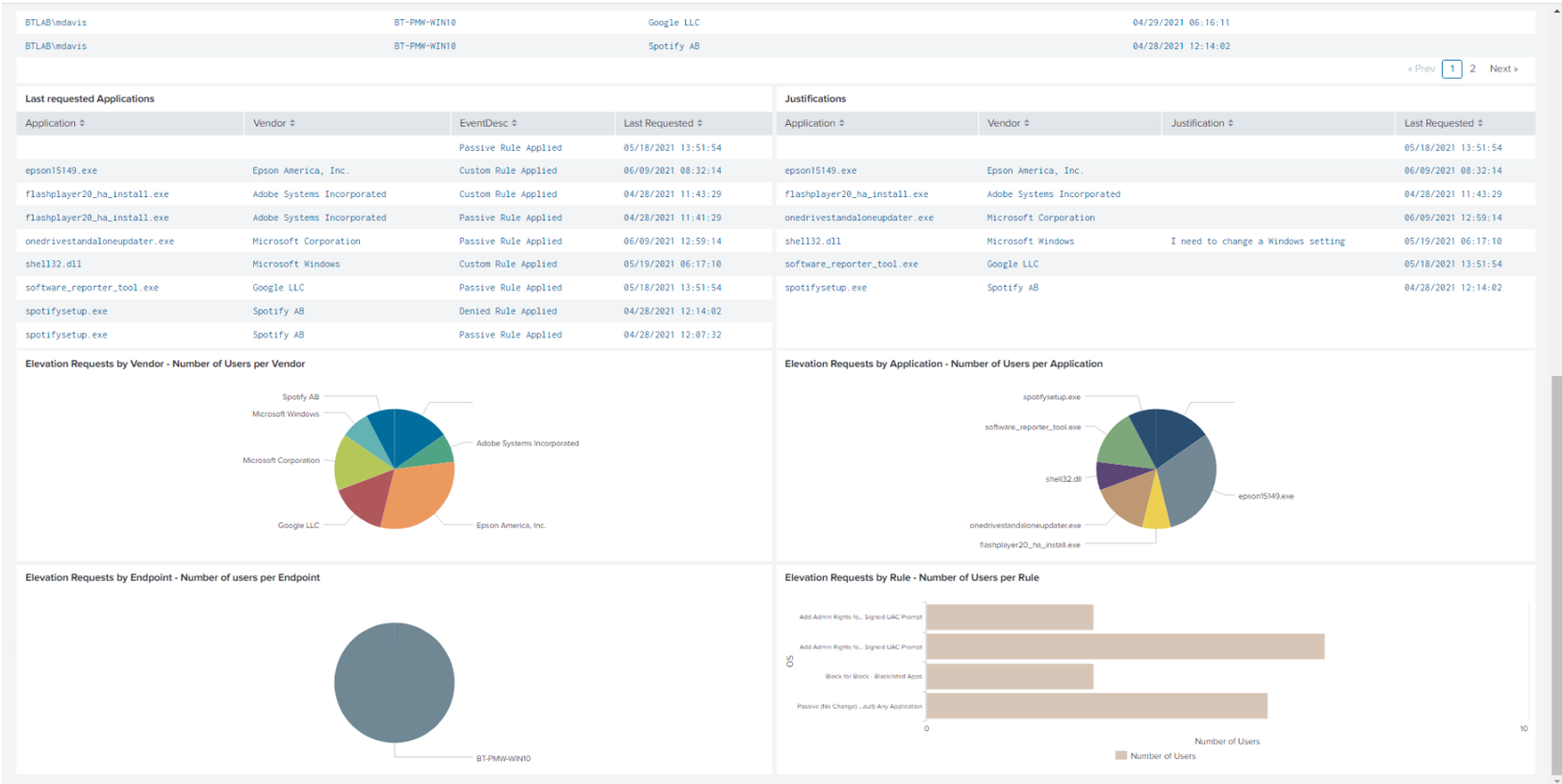
The Splunk app for BeyondTrust Endpoint Privilege Management allows customers to visualize and interpret the large number of events forwarded to Splunk by BeyondTrust. The Splunk app consists of a sample of relevant reports in various formats, grouped within a single dashboard.
The dashboard allows you to more rapidly benefit from the integration between Endpoint Privilege Management and Splunk by leveraging working reports that can be used as-is or as templates for custom reports.
Prerequisites
Configure BeyondInsight to forward Endpoint Privilege Management events to Splunk by following the BeyondInsight documentation.
You can configure a dedicated BeyondInsight connector that filters only Endpoint Privilege Management events.
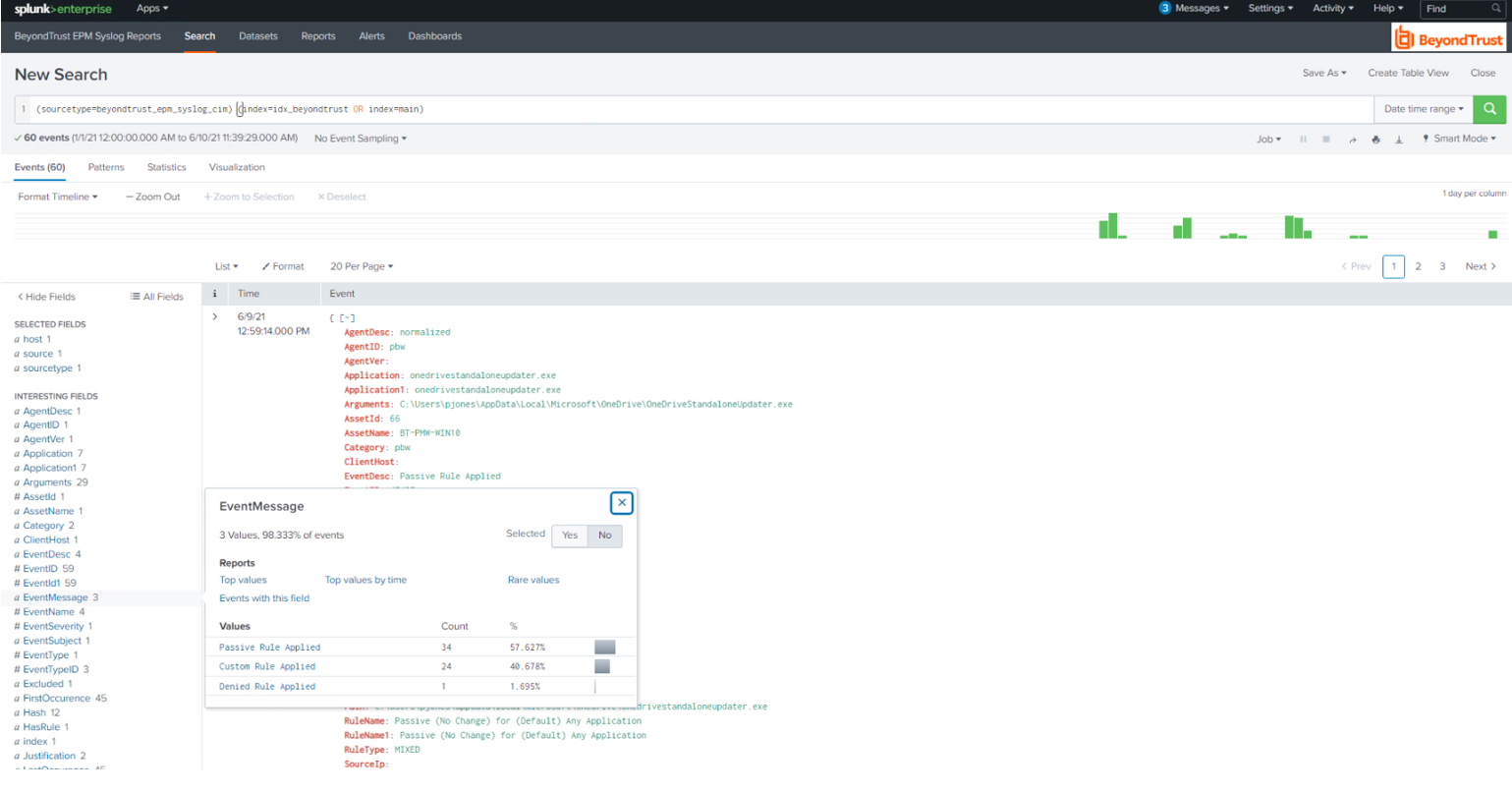
Validate that events from Endpoint Privilege Management through BeyondInsight are received by data inputs by Splunk. Adjustments might be required to align with expected values from Reports for source, sourcetype, and index.
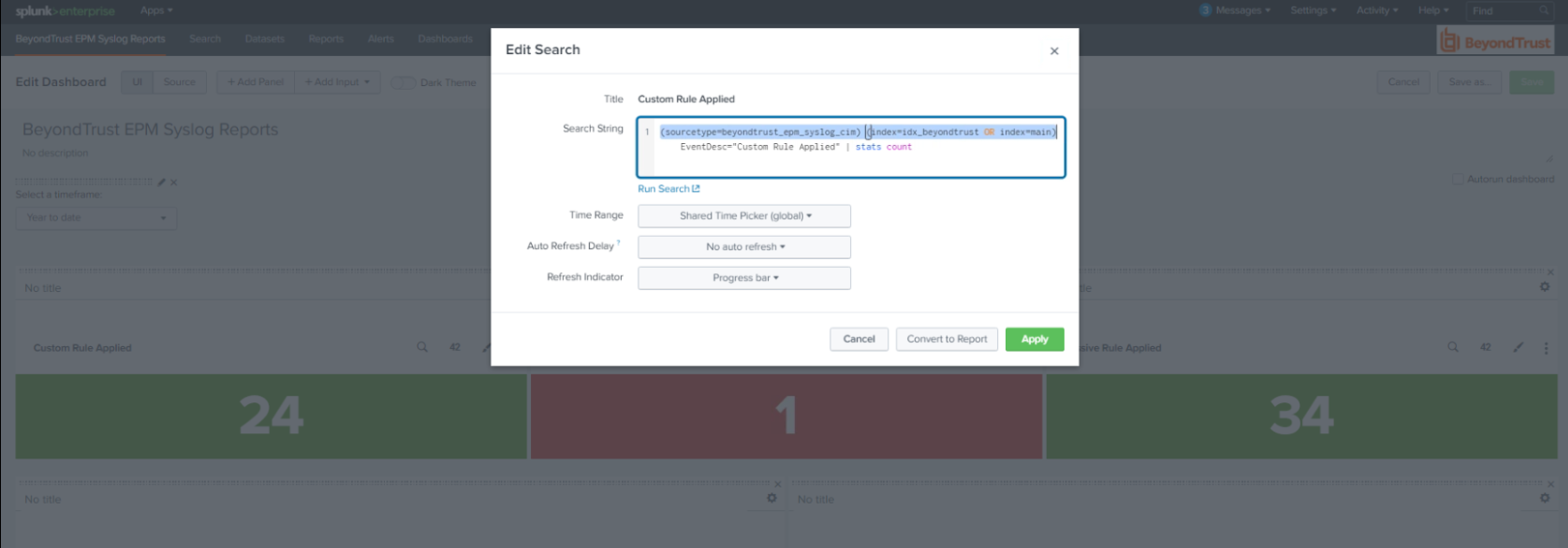
Each report in the dashboard filters data like this:
source=epm AND sourcetype=beyondtrust AND index=idx_beyondtrust
In Splunk, you can create a dedicated data input for Endpoint Privilege Management and assign desired values for the above attributes.
In Splunk, search for Endpoint Privilege Management events to confirm all prerequisites are in place, as shown in the image below.
For more information, see Configure Splunk Event Forwarder
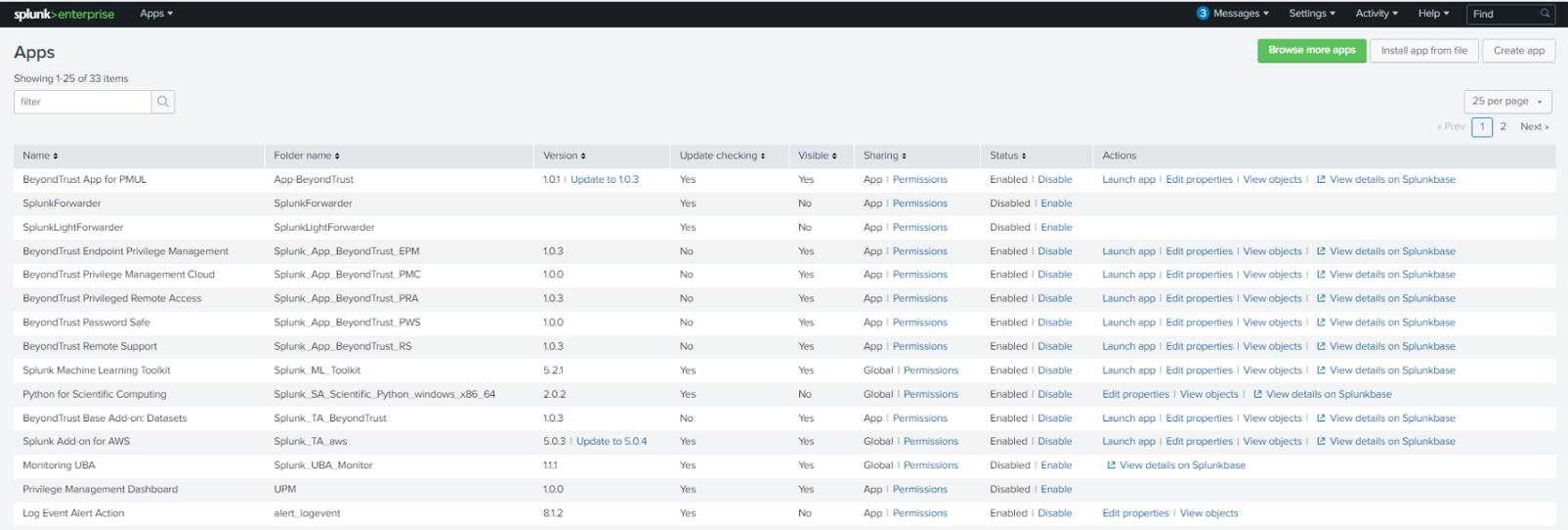
Import the App
Import the app either from Splunkbase or a file. Notifications are received when updates are available (version 1.0 and later).
Click Apps > Manage Apps to browse Splunkbase and search for the Endpoint Privilege Management app.
The following image shows collected events on the dashboard.
Troubleshoot
If reports don’t show any data, this might mean there is a mismatch with source or sourcetype and index. If data inputs or the event forwarder cannot be configured for the values expected by the reports and associated queries, an alternative is to edit each report query to resolve mismatches. Each report query can also be tested with the Splunk Search app.