Splunk App for Password Safe and PS Cloud
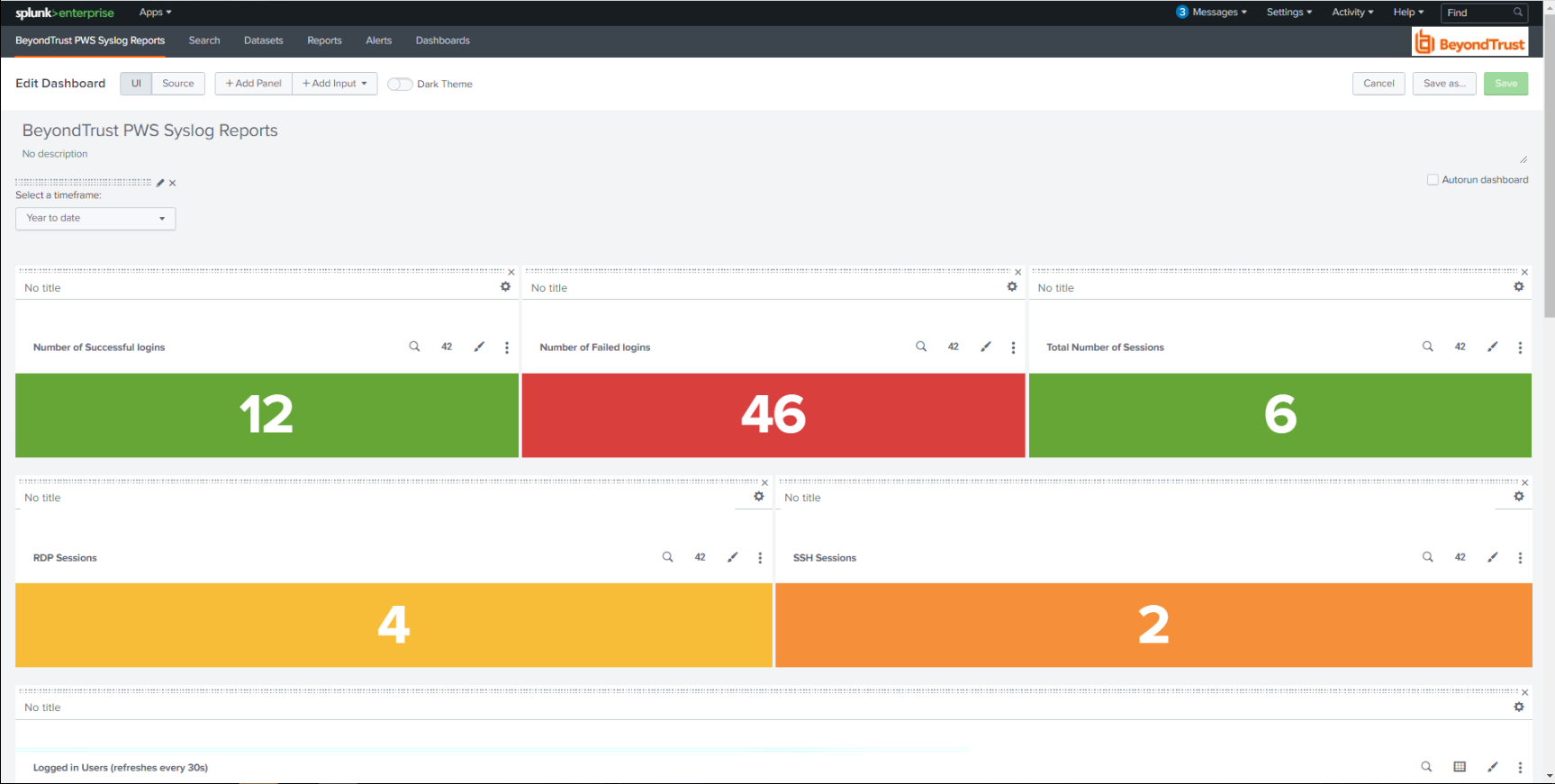
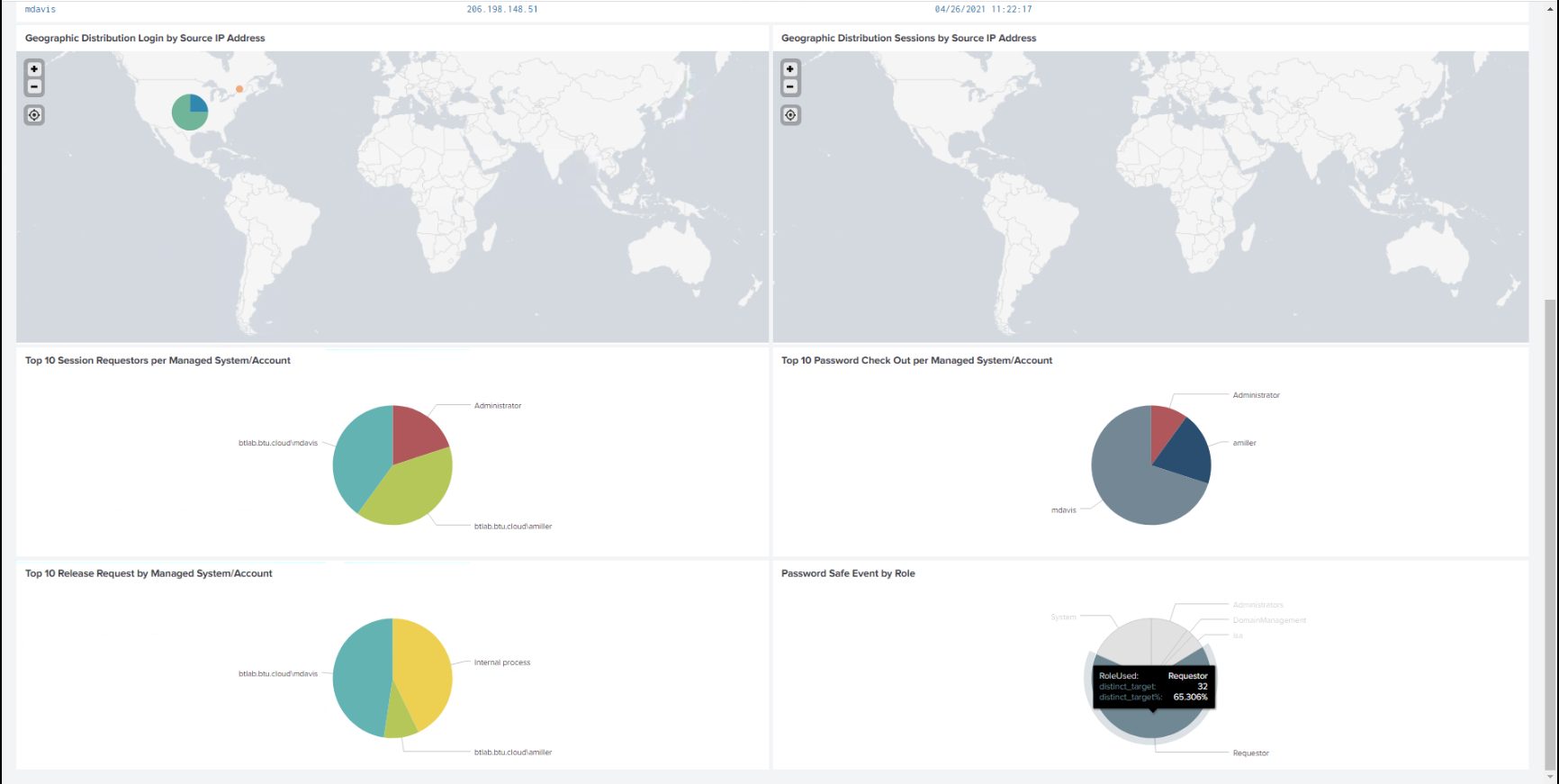
The Splunk App for BeyondTrust Password Safe allows customers to visualize and interpret the large number of events forwarded to Splunk by BeyondTrust. The app consists of a sample of relevant reports in various formats, grouped within a single Dashboard.
Using the Dashboard, customers can more rapidly benefit from the integration between Password Safe and Splunk by leveraging working reports that can be used as is or as templates for custom reports.
The BeyondTrust Password Safe Dashboard:
Prerequisites
Configure Password Safe to forward events to Splunk.
Configure the Splunk event forwarder connector
As a prerequisite, you must configure an HTTP EC data source in Splunk and note the API key for the configuration settings in the following procedure.
- In BeyondInsight, go to Configuration > General > Connectors.
- From the Connectors pane, click Create New Connector.
- Enter a name for the connector.
- Select Splunk Event Forwarder from the Connector Type list.
- Click the toggle to enable the Active (yes) option. Check Enable Event Forwarding.
- Enter the following details for the Splunk server:
- Host Name: (Required) The host name or IP address for your Splunk server.
- Port: (Required) The port used to communicate with your Splunk instance. The default is 8088.
- API Key: (Required) The Splunk API Key from your Splunk instance.
- Index: The name of the data repository on the Splunk server.
- Source Type: Data structure identifier for an event. The value is assigned to the event data collected.
- Source: Source value to assign to the event data. For example, set this key to the name of the application you are gathering events from.
- Host: The hostname of the client from which the data is forwarded.
- Expand Event Filters, and then select the events that you want to forward.
- Click Test Connector to send a test event message.
- Click Create Connector.
Validate events
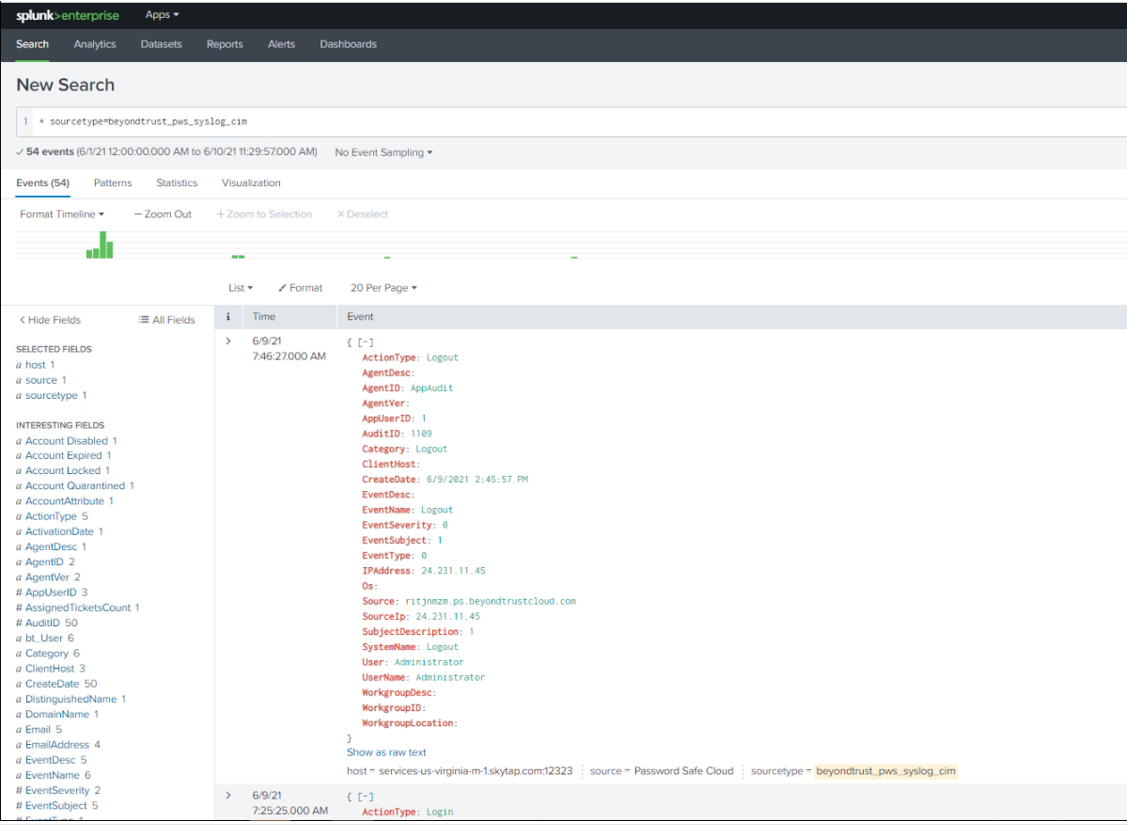
Validate events from Password Safe and/or Password Safe Cloud are received via Data Inputs by Splunk. Adjustments might be required to align with expected values from Reports for source, sourcetype, and index.
Each report in the Dashboard filters data like this:
(source=password_safe OR sourcetype=beyondtrust) index=idx_beyondtrust
You can create a reserved Data Input for Password Safe in Splunk and assign desired values for the above attributes.
- Confirm all prerequisites are in place by searching for Password Safe events.
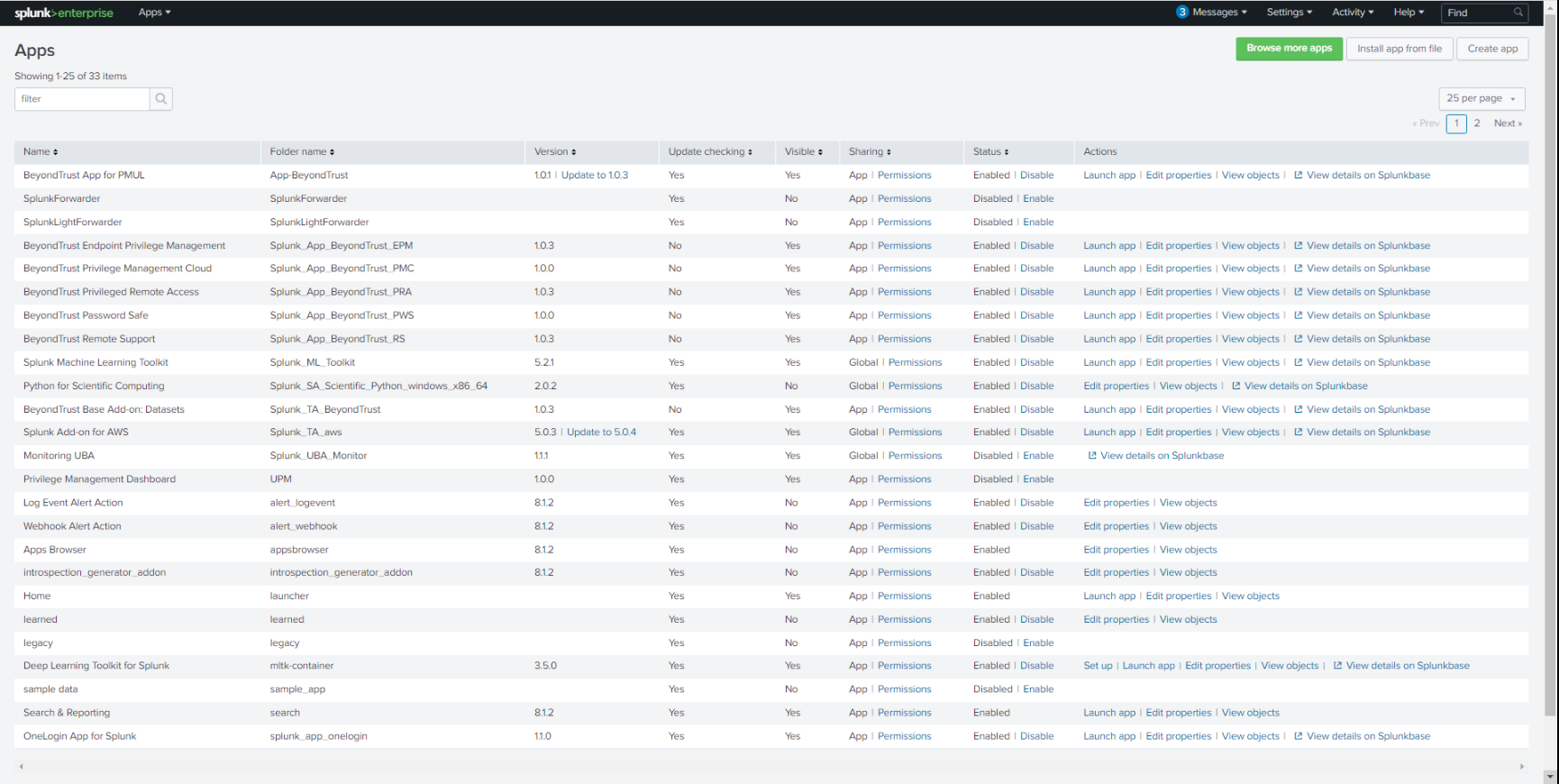
- Import the app either from Splunkbase or file. Notifications will be received when updates beyond version 1.0 are available.
- Click Apps > Manage Apps to browse Splunkbase and search for the Password Safe App.
- Access the Password Safe App Dashboard.
Troubleshooting
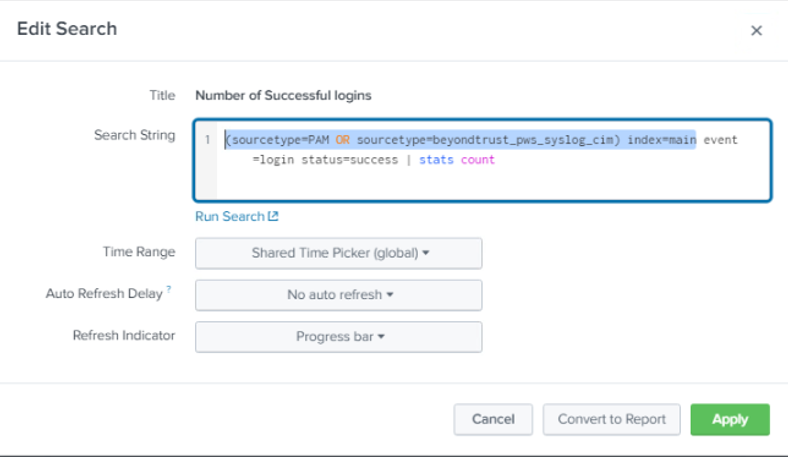
If reports don’t show any data, there might be a mismatch with source or sourcetype, and index. If Data Inputs or the event forwarder (Password Safe) cannot be configured for the values expected by the reports and associated queries, an alternative is to edit each report query to resolve mismatches. Each report query can also be tested with Splunk Search App.
The screen capture shows an example of a modified query for a report.