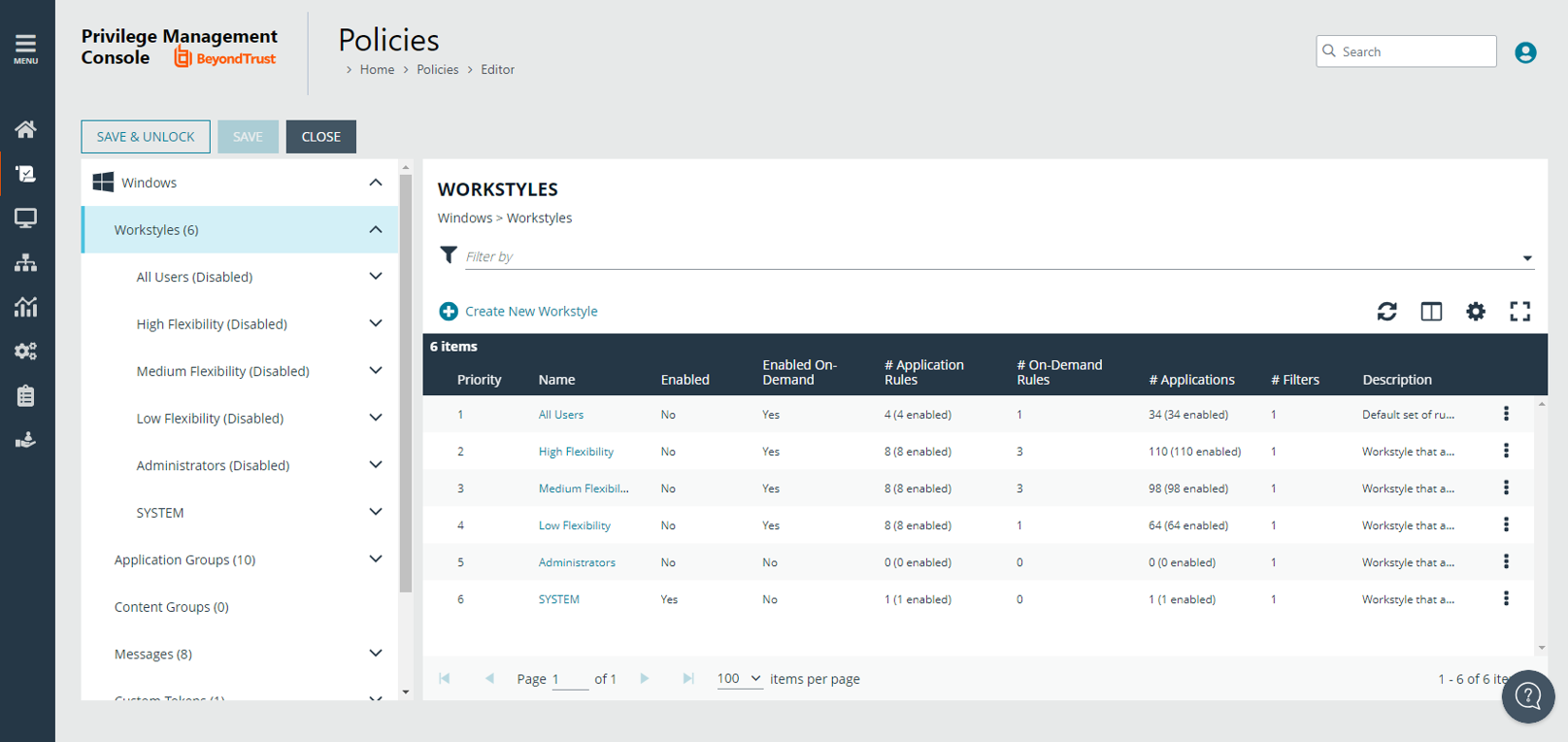
Workstyles
A Workstyle is a container for the rules that will be applied to the computers receiving the policy. If you are using a Windows or macOS Quickstart template, the Workstyles include predefined rule configurations.
If creating policy from a blank template, there is no predefined configuration.
- Add and change the properties for a rule
- Enable Trusted Application Protection (optional)
- Add monitoring and logging
- Change the ordering of Workstyle processing
- Enable the Workstyle
For more information about QuickStart templates, see Quickstart Templates.