Install BeyondInsight Event Server
The event collector role collects events and serves policy for BeyondTrust integrations. Event Server is FIPS 140-2 compliant and supports TLS versions up to TLS 1.2.
You can deploy additional event collectors to scale BeyondInsight to accommodate regional deployments in larger environments. However, it is not a typical installation scenario. It is recommended that BeyondTrust's Professional Services advise you on whether this installation scenario is suited to your BeyondInsight deployment.
For more information about BeyondTrust Professional Services, please see https://www.beyondtrust.com/services/all-services.
Installation overview
Use the following instructions to deploy BeyondInsight and the event collectors. The following install files and port requirements must be in place:
- BeyondInsight
- Event Server and patches. Confirm the latest version with BeyondTrust. A license is required.
- Port 21690 must be listening for TCP traffic. The port is used to receive SSL encrypted events from agents.
All files can be downloaded from the client portal.
The license key for all event collectors must match the license key for the main BeyondInsight installation.
Below is a high level overview of the installation steps.
- Run the Event Server installer and set up the connection to the database.
- Set up the crypto keys.
For more information, please see Export and import crypto keys for Event Server configuration.
- Export the crypto key from the primary BeyondInsight server.
- Import the key to all Event Server machines.
- Set up the certificates.
For more information, please see Export and import certificates for Event Server configuration.
- Export the three certificates with private keys from primary BeyondInsight server.
- Import the certificates to all event collector machines.
- Configure scanners to point to the Central Policy and send events to the Event Server.
- If using Windows authentication, the Event Server machine name must be added to a local group created on the SQL Server host.
For more information, please see the BeyondInsight Install Guide.
Run the installer
- Run the Event Server installer.
- Click Next on the Welcome page.
- Click the check box to accept the licensing terms.
- Select the location for the installation.
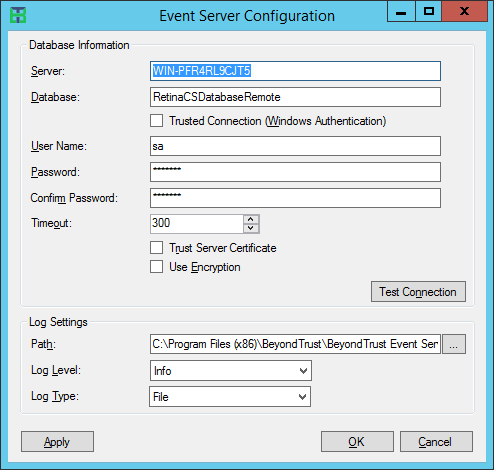
- Configure the connection to the database.
- Enter the IP address of the server hosting SQL Server.
- Enter the name of the database and include the credentials.
- Select the Trust Server Certificate check box.
- Select the Use Encryption check box.
If the connection to the database is lost, all events are stored in an encrypted local database. There are no limits on the number of events that can be stored.
- Click Test Connection to ensure the Event Server machine can successfully contact the database machine.
- Set the log settings, including location for the log file, level of logging, and log type.
- Click Apply.
Update the events client
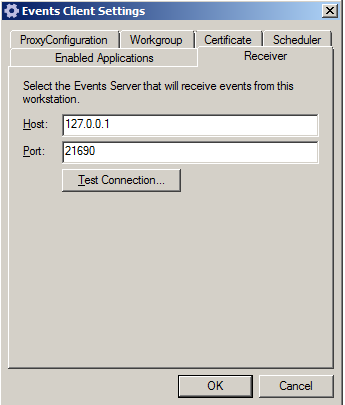
You must update the IP address for the client to establish a connection to the Event Server.
- Start the Events Client.
- Click the Receiver tab.
- Click OK.
Windows authentication
If you use Windows authentication for the Event Server, you must create a local group on the SQL Server host. This group requires db_owner access to the BeyondInsight database and is assigned the REM3Admins role.
You must add each Event Server machine name to this local group. For example, DomainName\EventServerMachineName$.
For more information, please see the BeyondInsight Install Guide.