Two-Factor Authentication Setup for BeyondTrust Remote Support Using a Time-Based, One-Time Password (TOTP)
BeyondTrust offers you a higher level of security with two-factor authentication, using a time-based, one-time password (TOTP). Besides entering their username and password to log in to the administrative interface and the BeyondTrust representative console, users who have this option enabled can use an authenticator app of their choice to receive a one-time code that allows them to securely log in.
TOTP Requirements
Users must have access to a device capable of generating one-time passwords. This is most often done through a smartphone authenticator app. Users are free to choose a compatible option, unless otherwise directed by their administrator. Examples of compatible authenticators include:
- Google Authenticator (Android, iOS)
- Authy (Android, iOS, WIndows, Linux, Mac)
- YubioAth Desktop (Windows, Linux, Mac)
- GAuth Authenticator (Windows Phone)
- Authentication Codes (Windows 8, Windows 10)
- OATHTool (command line)
- 1Password (Android, iOS, Mac, Windows)
Time-Based Considerations
With TOTP, an authenticator app generates a new password approximately every 30 seconds. Because of this, both the authenticator service and the device must be roughly in sync. BeyondTrust allows the clock on the user's device to be one minute off either way of the B Series Appliance's clock. If a wider time gap is experienced, the B Series Appliance may fail to recognize the codes generated by the user's device.
Activate Two-Factor Authentication
Depending on your company's security settings, users may have the option to activate two-factor authentication on their own. Alternatively, activation may be pushed by the administrator, in which case users would be asked to do so when logging in. While the activation process described below is similar either way, the differences are also covered.
Before you begin, make sure to have a compatible authenticator app on your smartphone.
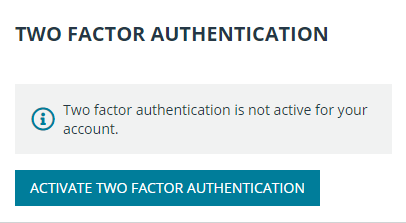
- Go to /login > My Account. Under Two Factor Authentication, click Activate Two Factor Authentication.
- The window changes to display the QR code and your next steps. If you have not already done so, download and install an authenticator app for your device.
- Follow your app's procedure to scan the code. Alternatively, you can type in the alphanumeric code that appears under the QR code. This can be useful if the QR code is not displaying properly or if your device is having issues capturing the image. Scanning the code is the preferred method.
- Once the app successfully captures the QR code, it generates a 6 digit token.
- Enter your password and the token, and then click Activate.
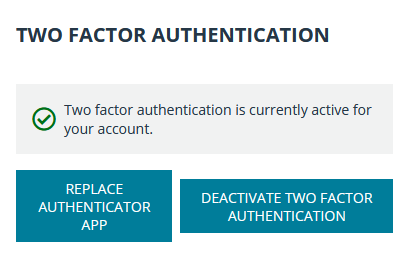
- Once the screen refreshes, it displays a confirmation that two-factor authentication is now enabled for your account. The next time you login to /login or the representative console, you are required to use two-factor authentication.
Activate and Require Two-Factor Authentication
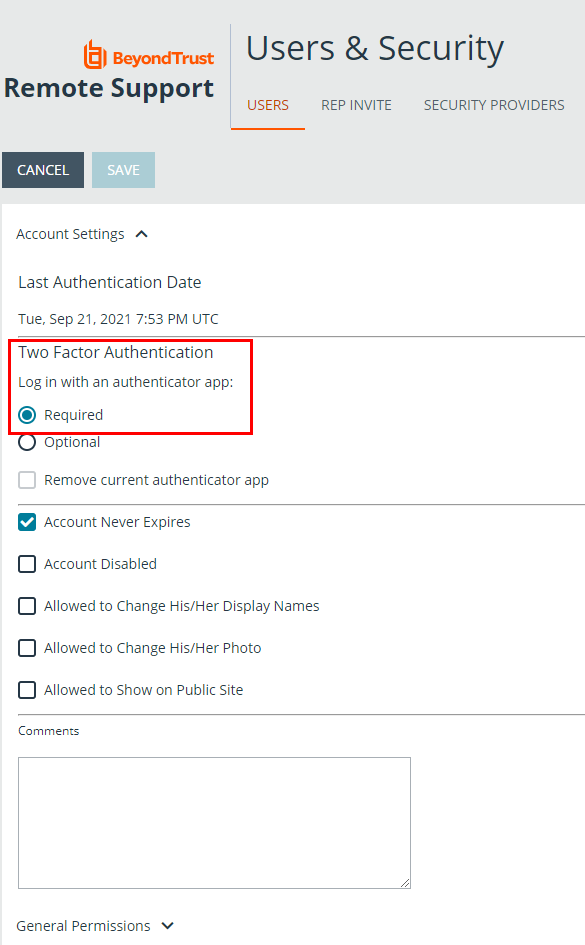
Administrators can require that users enable two-factor authentication on their accounts. To do this, go to Users & Security > Users, select a user to edit and under Account Settings > Two Factor Authentication, and check the Required button.
The next time this user tries to login to either the administrative interface or the representative console, a screen displays requiring the activation of two-factor authentication. The setup process is the same as outlined in the previous section.
Require Two-Factor Authentication in Group Policies
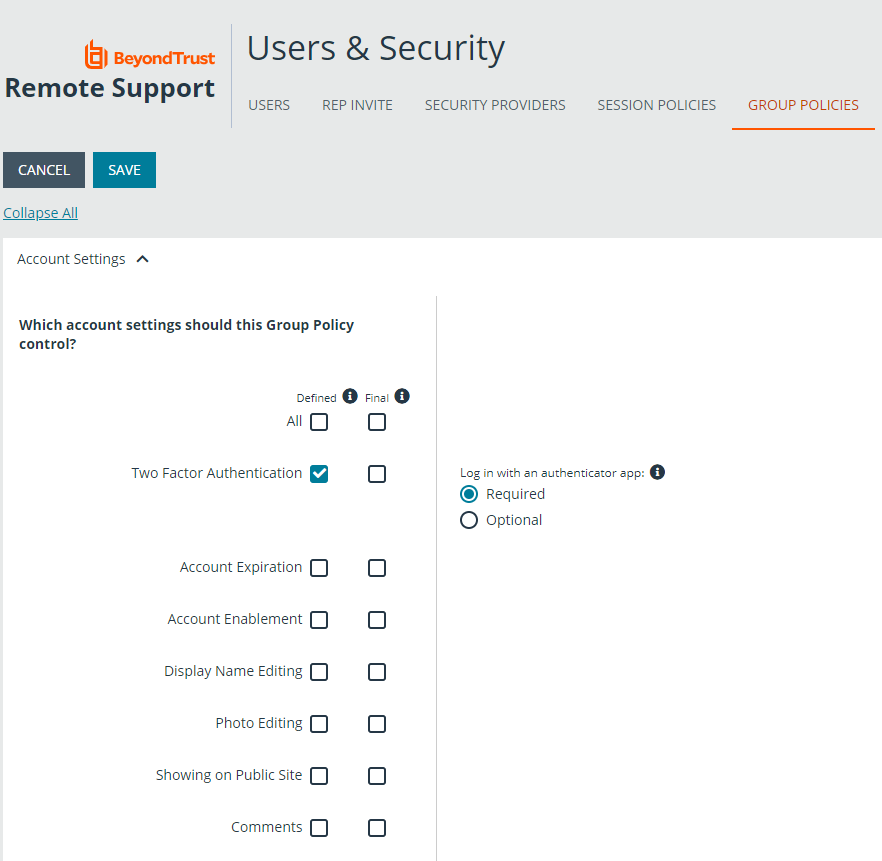
Two-factor authentication can also be defined when creating or editing group policies. Go to Users & Policies > Group Policies > Account Settings > Two Factor Authentication and select Required or Optional, depending on how you want to enforce its use.
Like other account settings in group policies, the administrator can decide if two-factor authentication is defined for a specific policy, and if it can be overridden.