Create and Use Shell Jump Shortcuts
With Shell Jump, quickly connect to an SSH-enabled or Telnet-enabled network device to use the command line feature on that remote system. For example, run a standardized script across multiple systems to install a needed patch, or troubleshoot a network issue.
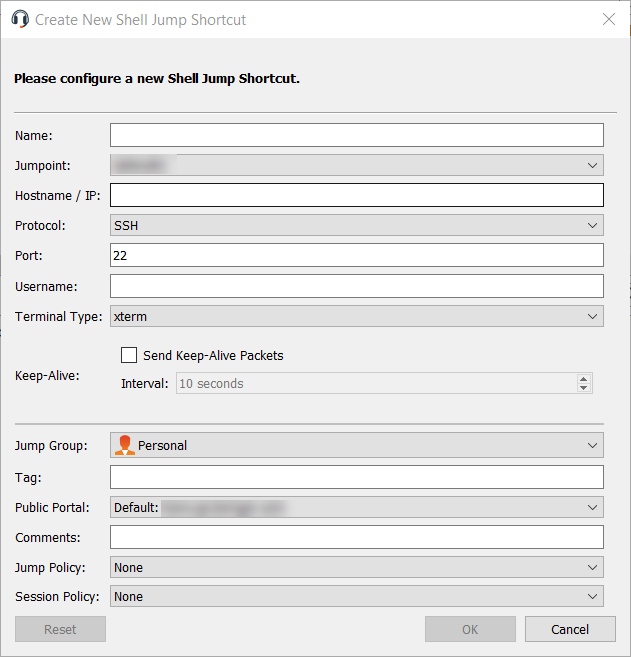
Create a Shell Jump Shortcut
To create a Shell Jump shortcut, click the Create button in the Jump interface. From the dropdown, select Shell Jump. Shell Jump shortcuts appear in the Jump interface along with Jump Clients and other types of Jump Item shortcuts.
Shell Jump shortcuts are enabled only if their Jumpoint is configured for open or limited Shell Jump access.
Organize and manage existing Jump Items by selecting one or more Jump Items and clicking Properties.
To view the properties of multiple Jump Items, the items selected must be all the same type (e.g., all Jump Clients, all Remote Jumps, etc.). To review properties of other types of Jump Items, please see the appropriate section in this guide.
Enter a Name for the Jump Item. This name identifies the item in the session tabs. This string has a maximum of 128 characters.
From the Jumpoint dropdown, select the network that hosts the computer you wish to access. The representative console remembers your Jumpoint choice the next time you create this type of Jump Item. Enter the Hostname / IP of system you wish to access.
Choose the Protocol to use, either SSH or Telnet.
Port automatically switches to the default port for the selected protocol but can be modified to fit your network settings.
Enter the Username to sign in as.
Select the Terminal Type, either xterm or VT100.
You can also select to Send Keep-Alive Packets to keep idle sessions from ending. Enter the number of seconds to wait between each packet send.
Move Jump Items from one Jump Group to another using the Jump Group dropdown. The ability to move Jump Items to or from different Jump Groups depends upon your account permissions.
Further organize Jump Items by entering the name of a new or existing Tag. Even though the selected Jump Items are grouped together under the tag, they are still listed under the Jump Group in which each is pinned. To move a Jump Item back into its top-level Jump Group, leave this field blank.
Select the Public Portal through which this Jump Item should connect. If a session policy is assigned to this public portal, that policy may affect the permissions allowed in sessions started through this Jump Item. The ability to set the public portal depends on your account permissions.
Jump Items include a Comments field for a name or description, which makes sorting, searching, and identifying Jump Items faster and easier.
To set when users are allowed to access this Jump Item, choose a Jump Policy. These policies are configured by your administrator in the /login interface.
Choose a Session Policy to assign to this Jump Item. The session policy assigned to this Jump Item has the highest priority when setting session permissions. The ability to set a session policy depends on your account permissions.
Use a Shell Jump Shortcut
To use a Jump shortcut to start a session, select the shortcut from the Jump interface and click the Jump button.
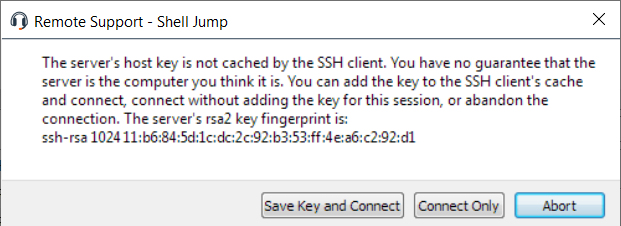
If attempting to Shell Jump to an SSH device without a cached host key, you receive an alert that the server's host key is not cached and that there is no guarantee that the server is the computer you think it is.
If you choose Save Key and Connect, then the key is cached on the Jumpoint's host system so that future attempts to Shell Jump to this system do not result in this prompt. Connect Only starts the session without caching the key, and Abort ends the Shell Jump session.
If you Shell Jump to an SSH device with keyboard interactive MFA enabled, there is a secondary prompt for input.
When you Shell Jump to a remote device, a command shell session immediately starts with that device. If you Shell Jump to a provisioned SSH device with an unencrypted key or with an encrypted key whose password has been cached, you are not prompted for a password. Otherwise, you are required to enter a password. You can then send commands to the remote system.