Rotate Privileged Credentials Using BeyondTrust Vault for PRA
Frequently rotating or changing privileged credentials is considered a security best practice. Credentials stored in BeyondTrust Vault can be set to automatically rotate after each use, and can be manually rotated at any time.
The algorithm Vault uses to generate passwords is based on National Institute of Standards and Technology (NIST) framework.
Three actions trigger the automatic rotation of domain credentials:
- Manually checking in a credential from the /login interface.
- Leaving an access session where credential injection has been used.
- Scheduled password rotation is enabled and the password has reached its maximum age.
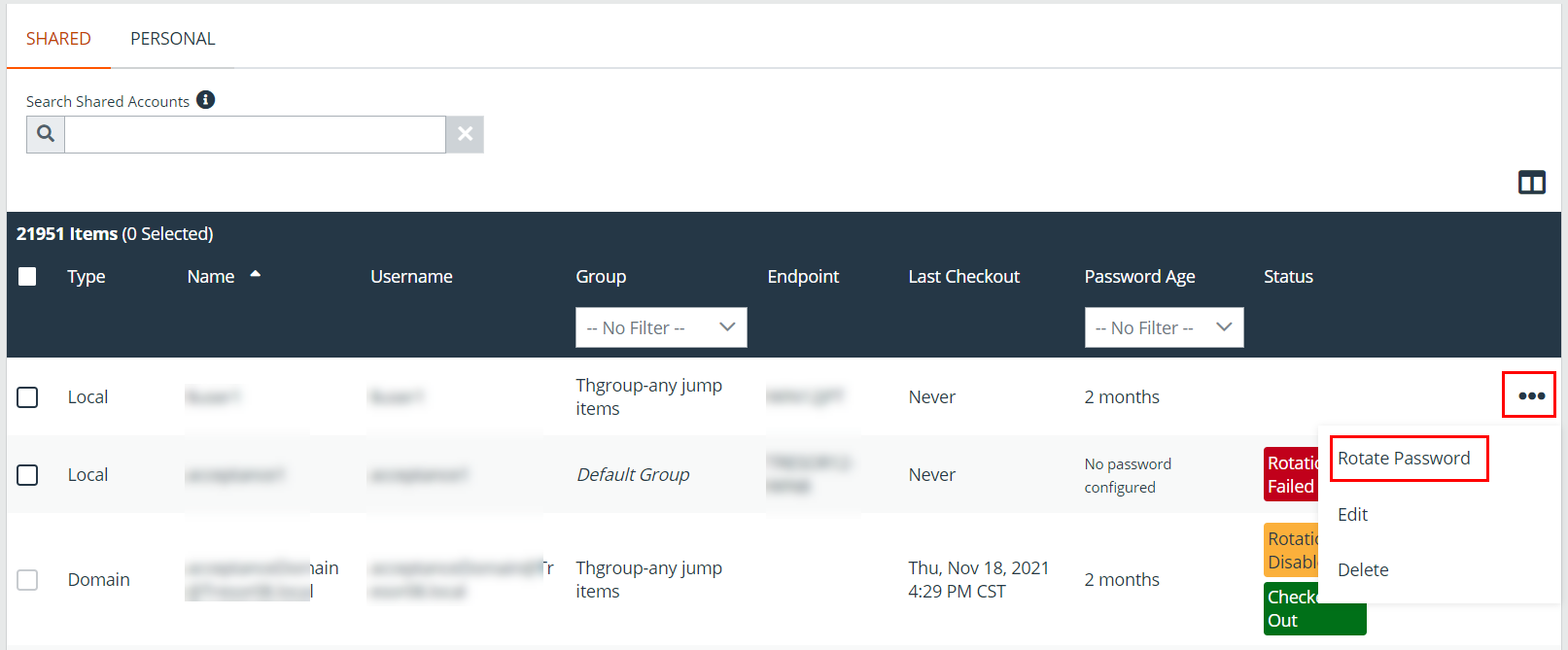
Rotate Domain and Local Credentials Manually
- From the /login interface, navigate to Vault > Accounts.
- Click the ellipsis button for the account password you wish to rotate.
- Select Rotate Password.
Once rotation is complete, the Password Age information updates with a time stamp of a few seconds.
Configure Automatic and Scheduled Rotation of Vault Credentials
To configure passwords for Vault accounts to automatically rotate after each use, enable the Automatically Rotate Credentials after Check In Rules option in the account policy being used for the account.
You can schedule password changes for Vault accounts by enabling the Scheduled Password Rotation Rules option in the account policy being used for the account.
- Service accounts running in a failover cluster environment cannot be rotated. The error "Failover Cluster detected. Unable to change the run-as password for the service <service_name>" appears when a rotation attempt is made and Rotation Failed is indicated in the Status column for the service.
- Services using a Microsoft Graph account as the Run As account cannot be rotated.
- Services that have dependent services cannot be rotated, due to the risk of services within the service chain not restarting successfully.
You can define the password length for passwords generated during rotation for Windows and Entra ID Domain Services domain and local accounts from the Vault > Options page in /login.
- Account policies, please see Add and Manage Vault Account Policies.
- Rotating credentials for protected users, please see Configure User Permissions to Rotate Protected Credentials.