Privileged Remote Access (On-Premises) Security
The purpose of this document is to help you, a technically-oriented professional, understand the security-related value BeyondTrust brings to your organization. BeyondTrust can help your organization stay secure and compliant, while improving the efficiency and success of your organization with a better user experience.
BeyondTrust Overview
BeyondTrust connects and protects people and technology with leading secure access solutions that strengthen security while increasing productivity. Privileged Remote Access lets you control access to critical systems without hindering the work privileged users need to perform. You can define how users connect, monitor sessions in real time, and record every session for a detailed audit trail.
BeyondTrust Privileged Remote Access can connect to external user directories, such as LDAP, for secure user management, and natively integrates with leading systems management and identity management solutions. An API is provided for use with automation tools and external applications.
Remote access through BeyondTrust is compatible with multiple operating systems, including Windows, Mac, various Linux distributions, and mobile operating systems. Supported system types include laptops, desktops, servers, kiosks, point-of-sale systems, smartphones, and network devices.
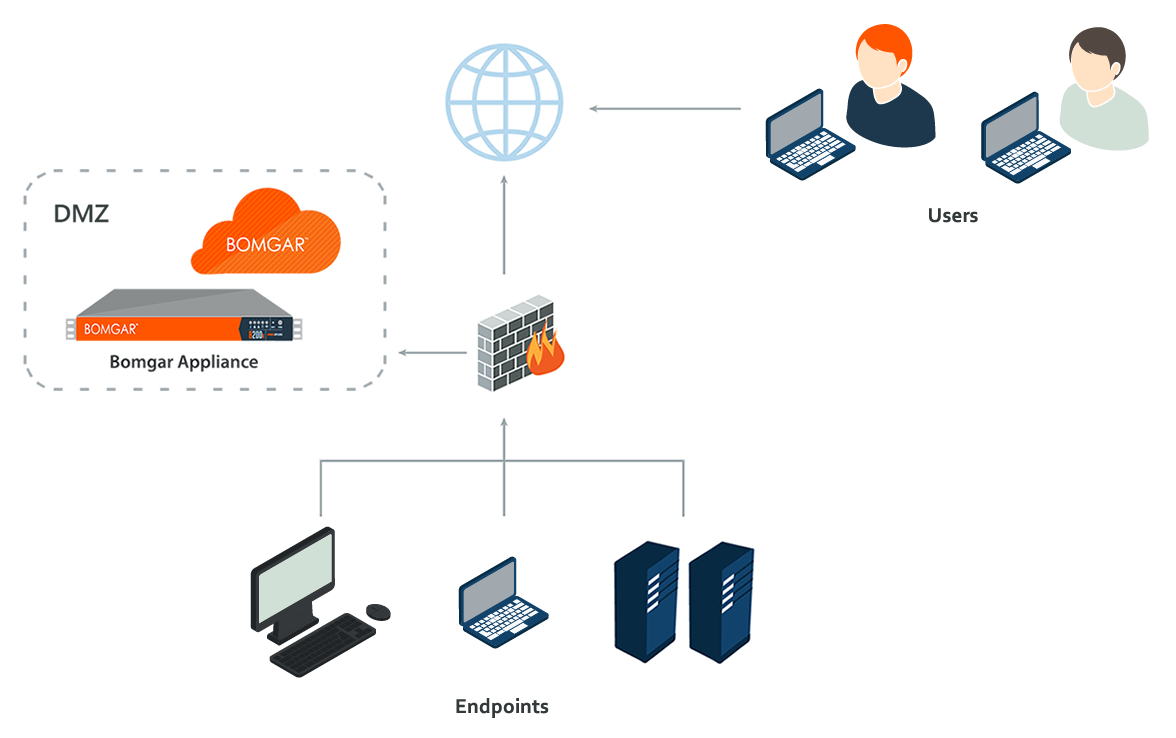
Architecture of Privileged Remote Access On-Premises
To make secure access possible, the BeyondTrust architecture places the B Series Appliance as the focal point of all communications. The B Series Appliance provides an interface using Hypertext Transfer Protocol (HTTP) for unauthenticated services, Secure HTTP (HTTPS) for authenticated services, and direct client connections accepted over a proprietary, BeyondTrust-defined protocol
The B Series Appliance is comprised of two main components. The first, called Base, is made up of the firmware that provides system-level configuration of a B Series Appliance. Settings such as IP addresses and security certificate configurations are all configured via the Base firmware, which is accessed via the /appliance web interface.
The software used for site-level configuration, accessed via the /login web interface, makes up the second functional component. The user configuration and session options take place behind the /login page, and you can download the BeyondTrust access console, endpoint client, Jump Clients, Jumpoints, and security provider connection agents from there. Sessions always occur through the B Series Appliance, and since the connections are outbound from the clients to the B Series Appliance using well known ports, the application can communicate without local firewall changes.
Validation
To ensure the security and value of our product, BeyondTrust incorporates vulnerability scanning in our software testing process. We track the results of vulnerability scans performed prior to a software release and prioritize resolution based on severity and criticality of any issues uncovered. In the event a critical or high-risk vulnerability surfaces after a software release, a subsequent maintenance release addresses the vulnerability. Updated maintenance versions are distributed to our customers via the update manager interface within the Privileged Remote Access (PRA) administrative interface. When necessary, BeyondTrust Support contacts customers directly, describing special procedures to follow to obtain an updated maintenance version.
In addition to internal scanning procedures, BeyondTrust contracts with third-parties for a source code level review as well as penetration testing. The source code review conducted essentially provides validation from a third party that coding best practices are followed and that proper controls are in place to protect against known vulnerabilities. A penetration test is conducted to confirm the findings.