The BeyondTrust Appliance B Series in the Network Environment
The architecture of the BeyondTrust application environment relies on the B Series Appliance as a centralized routing point for all communications between application components. All BeyondTrust sessions between users and remote systems occur through the server components that run on the B Series Appliance. To protect the security of the data in transit, BeyondTrust uses 256-bit Advanced Encryption Standard (AES) SSL to encrypt all application communications.
BeyondTrust's architecture offers customers the ability to choose how and where the B Series Appliance is deployed. Additionally, customers may configure the security features such that the BeyondTrust deployment complies with applicable corporate policies or regulations. Security features include role-based access control and secure password requirements.
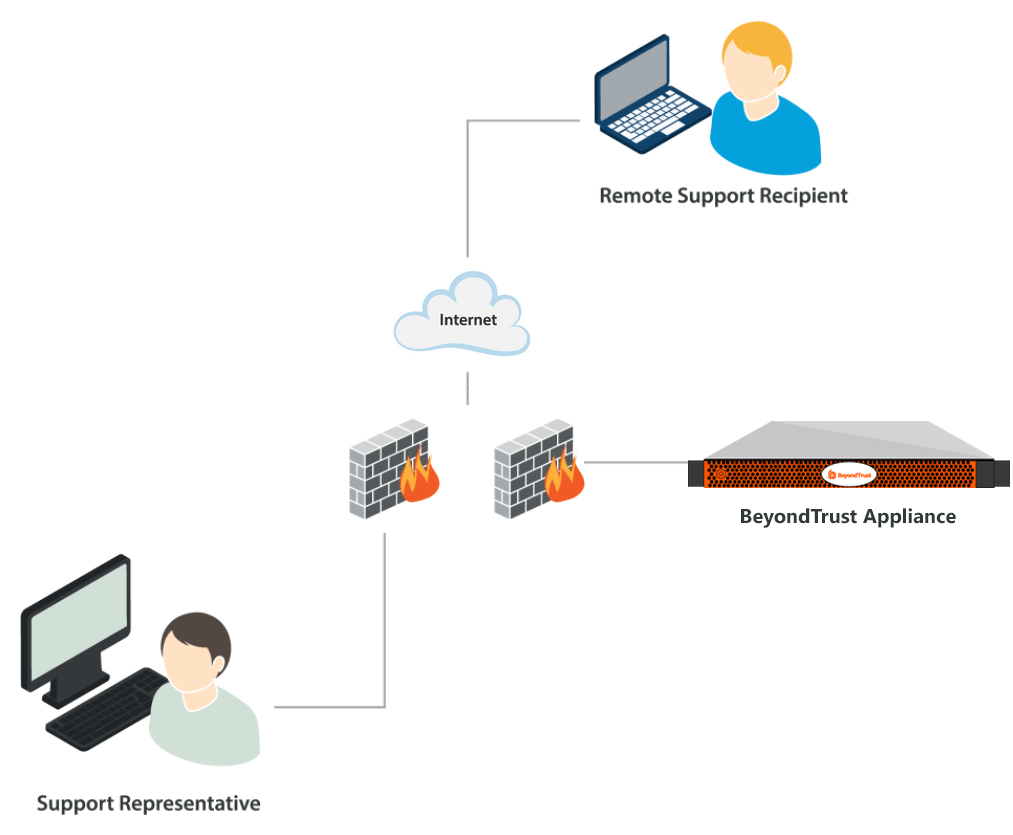
BeyondTrust enables remote control by creating a remote outbound connection from the endpoint system to the B Series Appliance through firewalls. For BeyondTrust to provide remote control securely, the B Series Appliance is designed to use the most common network infrastructure or architecture that supports internet-accessible applications – a demilitarized zone (DMZ) with firewall protection.
The BeyondTrust Appliance B Series is designed and tested to ensure it works properly and securely in internet environments. While the B Series Appliance can be deployed internal or external to your organization, to achieve optimal security, BeyondTrust recommends that you place the B Series Appliance inside the DMZ, as illustrated. This diagram shows the recommended configuration for one B Series Appliance.
By locating the B Series Appliance in the DMZ, the B Series Appliance is within the secure buffer zone. Since all BeyondTrust sessions are initiated via outbound connections from the client to the B Series Appliance, it is possible to remotely control computers using BeyondTrust through the firewalls.