Email configuration: configure the software to send emails
Management
Email Configuration
Email address
If a B Series Appliance is designated as a backup B Series Appliance or a traffic node, the email configuration for that B Series Appliance will be overwritten with the email configuration defined on the primary B Series Appliance.
From Address
Set the email address from which automatic messages from your B Series Appliance will be sent.
SMTP relay server
Configure your B Series Appliance to work with your SMTP relay server in order to send automatic email notifications of certain events.
SMTP Relay Server
Enter the hostname or IP address of your SMTP relay server.
SMTP Port
Set the SMTP port to contact this server on.
SMTP Encryption
If your SMTP server supports TLS encryption, choose TLS or STARTTLS. Otherwise, select None.
SMTP Authentication Type
To use a form of authentication with this server, select either Username and Password or OAuth2. Otherwise, select None.
Username and Password
Enter a username and password to configure this form of authentication.
OAuth2
For more information, please see the following:
Admin contact
Default Admin Contact Email Addresses
Enter one or more email addresses to which emails should be sent. Separate addresses with a space.
Send Daily Communication Notice
You can have the B Series Appliance send a daily notification to ensure that alert communication is working correctly.
In addition to the test email and daily communication notices that can be configured above, emails are sent for the following events:
- During any failover operation, the product version on the primary node does not match the product version on the backup node.
- During a failover status check, any of the following problems are detected.
- The current B Series Appliance is the primary node and a shared IP address is configured in /login, but its network interface is not enabled.
- A shared IP address is configured in /login but is not listed as an IP address in /appliance.
- The backup node could not contact the primary node, and it also could not contact any of the test IP addresses configured on the Management > Failover page.
- The backup node could not contact any of the test IP addresses configured on the Management > Failover page.
- The backup node's backup operations are disabled on the Management > Failover page.
- The backup node unexpectedly failed to perform a probe of itself, indicating that it is malfunctioning.
- The backup node failed to contact the primary node using the primary node's hostname.
- Automatic failover is disabled, and the backup node failed to probe the primary node.
- Automatic failover is enabled, and the backup node failed to probe the primary node. The backup node will automatically become the primary node if the primary node remains unresponsive.
- Automatic failover is enabled, and the backup node is automatically becoming the primary node because the primary node was down for too long.
- The primary node failed to perform a data sync with the backup node sometime in the past 24 hours.
Send a test email when the settings are saved
If you wish to receive an immediate test email to verify that your SMTP settings are accurately configured, check this option before clicking the Save button.
Configure OAuth2 for Entra ID
Before starting configuration on Entra ID, an Azure/Office 365 Administrator must enable Authenticated SMTP for each account on Exchange online. To do this, go to Office 365 Admin Portal (admin.microsoft.com) > Active Users > Mail > Manage Email apps and check Authenticated SMTP.
Configure Entra ID
- Log into your Azure console (portal.azure.com), navigate to Entra ID, and follow instructions there for registering a new application.
- The redirect URI is https://{URL OF YOUR APPLIANCE}/login/smtp-verification.
- Note the following, as they are required later:
- Application (client) ID
- Authorization endpoint
- Token endpoint
- Client secret
Provide credentials to the SMTP relay server
- Within the Privileged Remote Access admin interface, navigate to Management > Email Configuration.
- Under SMTP Authentication Type, select OAuth2, and enter the following information:
- Email: The email address for the SMTP relay.
- SMTP OAuth Provider ID: The application ID noted earlier.
- SMTP OAuth Client Secret: The client secret noted earlier.
- SMTP OAuth Scopes: Enter https://outlook.office.com/SMTP.Send offline_access.
- SMTP OAuth Authentication Endpoint: The authorization endpoint noted earlier.
- SMTP OAuth Token Endpoint: The token endpoint noted earlier.
- Click Save.
- Now you can verify and connect the provider account. Click Verify Oauth2 Provider.
Ensure you are logged into the provider portal as the email address for the SMTP relay, entered above, in the same browser session. You may need to log out of your personal or admin account.
Configure OAuth2 for Google
Configure Google Cloud
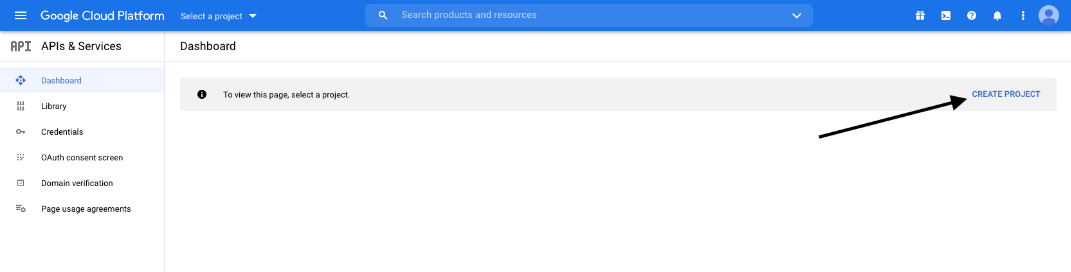
- Log in to your Google Cloud Platform console (Google Dev Console) (console.cloud.google.com). Use the correct Gmail account, as only the owner of the project is able to work with the project. If you do not already have a paid account, you might choose to purchase an account by clicking Activate in the top banner. BeyondTrust cannot provide assistance with purchasing an account. Click Learn More in the top banner for information regarding the limitations of free accounts.
- Click CREATE PROJECT. You can also use an existing project.
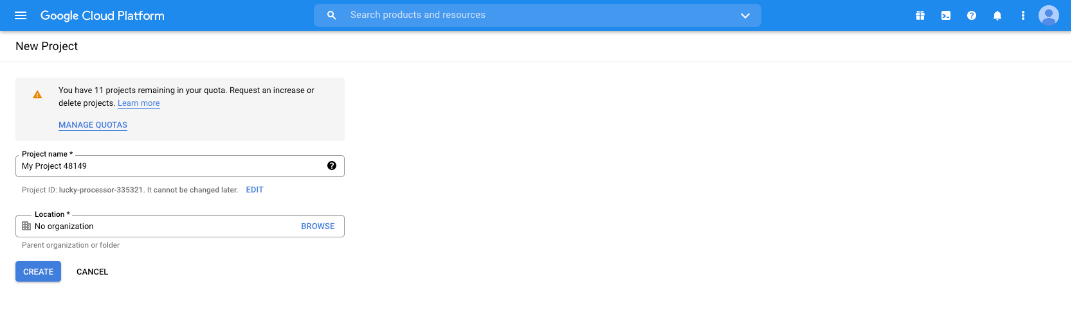
- Accept the default Project Name, or enter a new name.
- Accept the default Location, or select a folder from those available for your organization.
- Click CREATE.
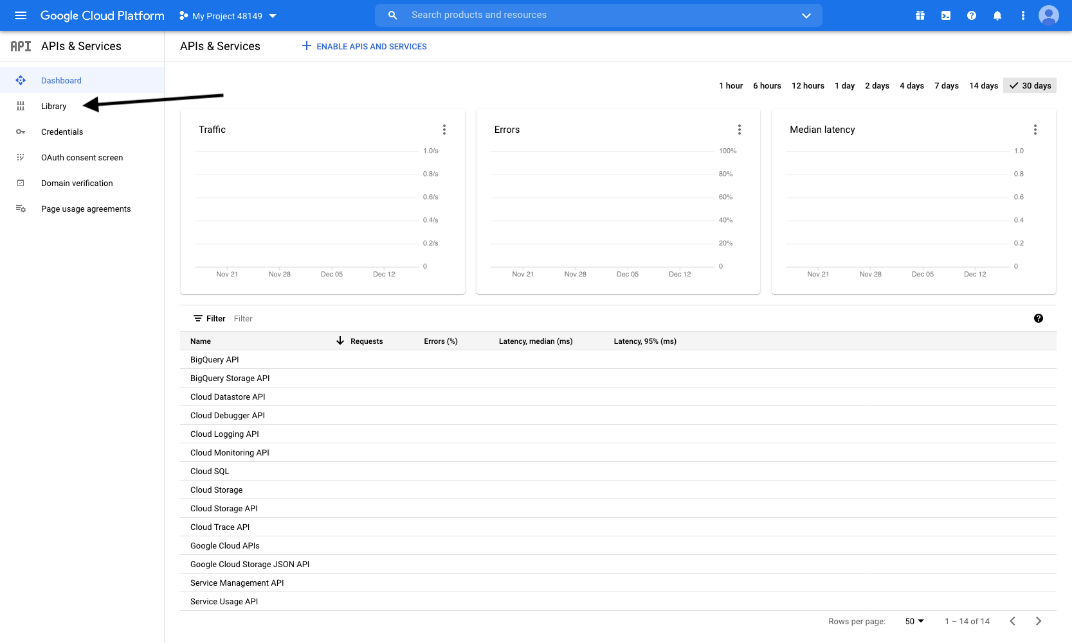
- The APIs and services page appears. Click Library in the left menu.
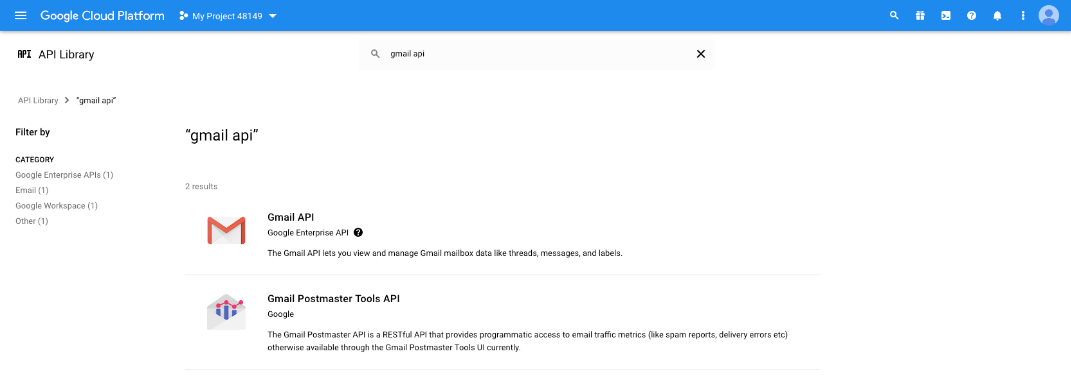
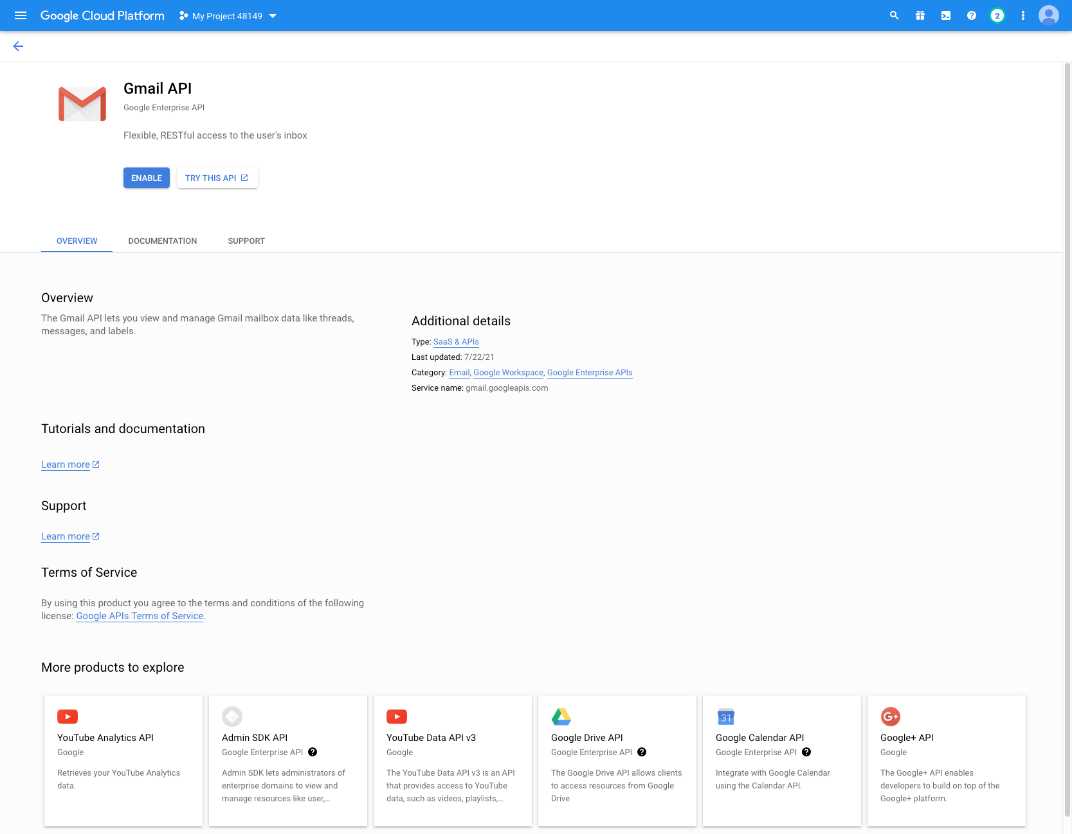
- Search or browse for the Gmail API in the library, and click it.
- The Gmail API appears on its own page. Click ENABLE.
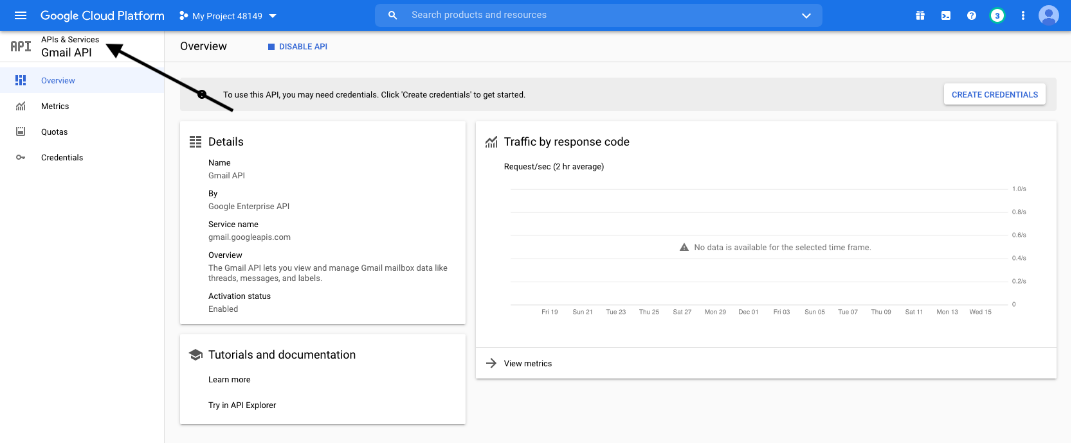
- The Gmail API Overview page appears. Click APIs & services in the upper left.
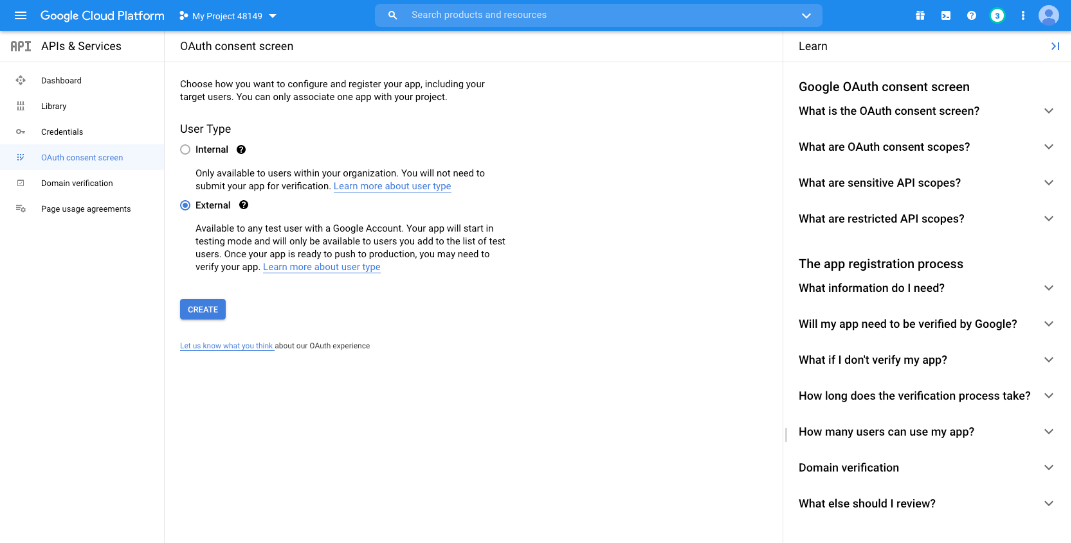
- The APIs and services page appears again. Click OAuth consent screen in the left menu.
- Select the User Type. Internal allows only users from within the organization, but requires a Google Workspace account.
- Click CREATE.
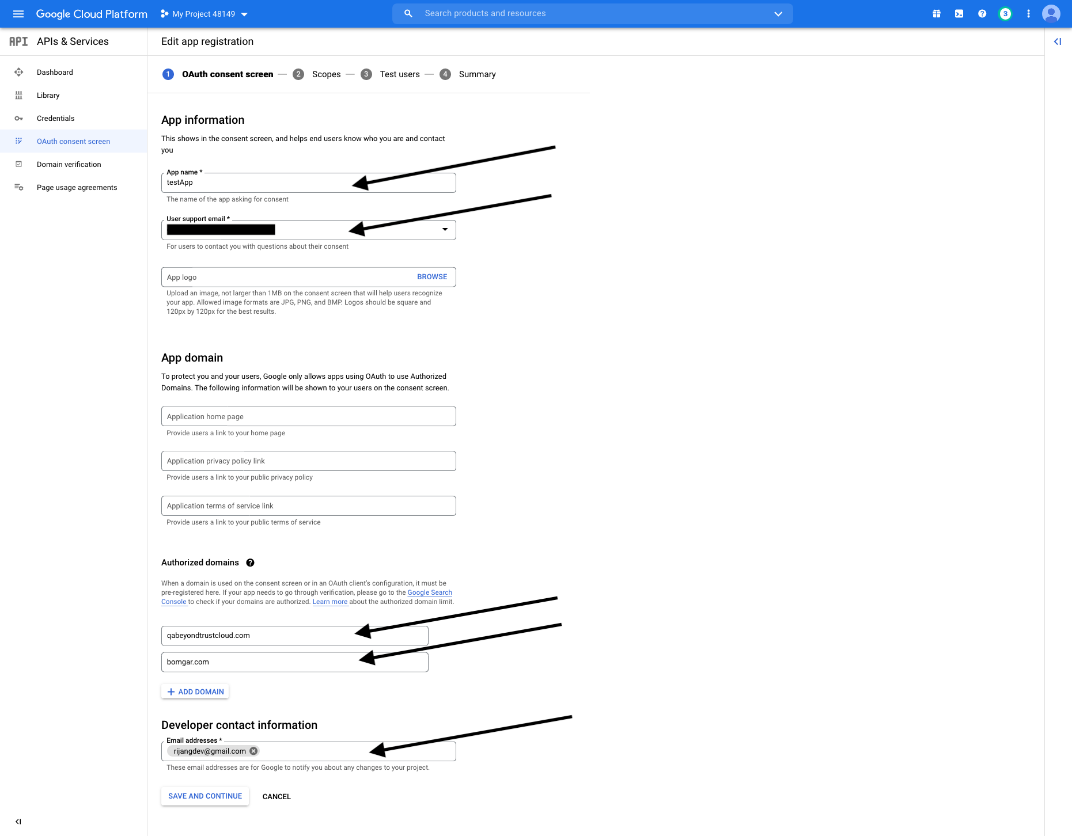
- Enter the App name.
- Enter a User support email address. This may default to the address you are using to create the project.
- Enter a logo for the app, if desired. The App domain section is also optional.
- Add the Authorized domains. For BeyondTrust test appliances, these are:
- qabeyondtrustcloud.com
- bomgar.com
- Enter the Developer contact information. This is the email address you are using to create the project.
- Click SAVE AND CONTINUE.
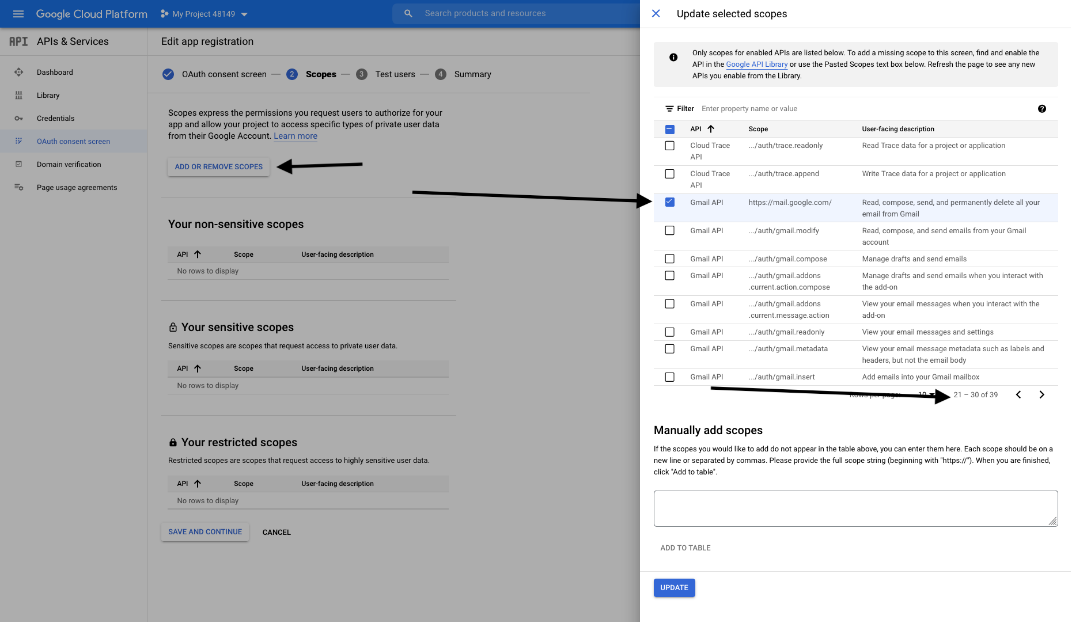
- Under the Scopes tab, click ADD OR REMOVE SCOPES. This opens the Update selected scopes window.
- Locate and check the scope https://mail.google.com/ for the Gmail API.
The API does not appear if it has not been enabled.
- Click UPDATE. The Update selected scopes window closes.
- Click SAVE AND CONTINUE.
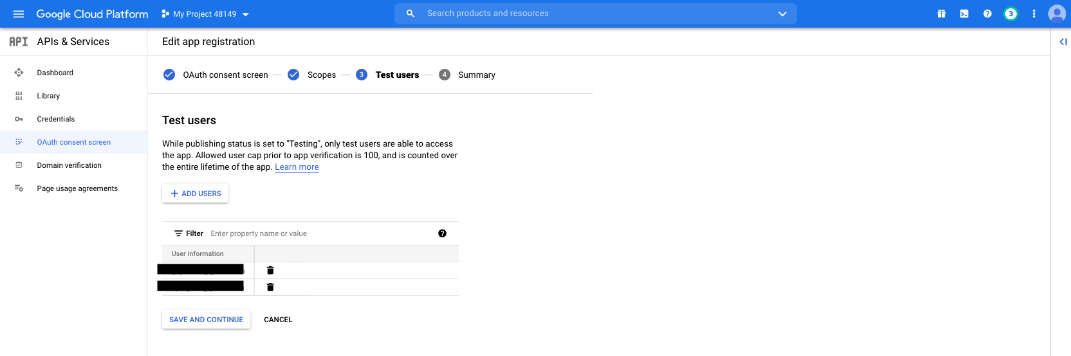
- Under the Test users tab, click ADD USERS. This opens the Add Users window. Add the users that have access to the application and click ADD. Note the limits on test user access and related restrictions.
- Click SAVE AND CONTINUE.
- Review the Summary, and make any necessary changes or corrections.
- Click BACK TO DASHBOARD.
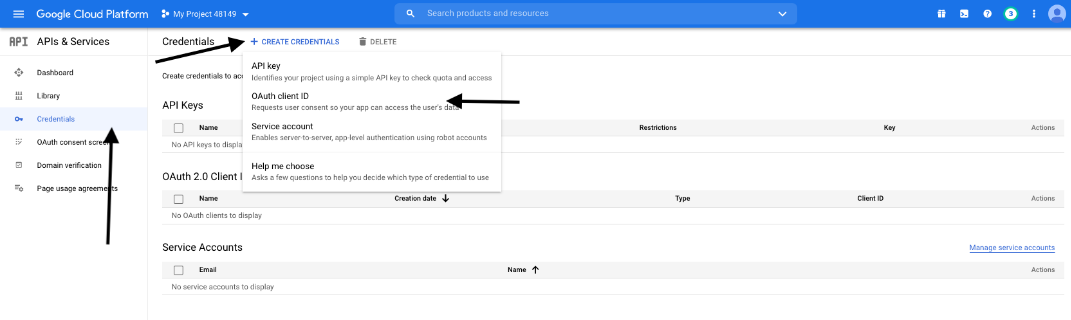
- Click Credentials in the left menu.
- Click CREATE CREDENTIALS in the top banner and select OAuth client ID.
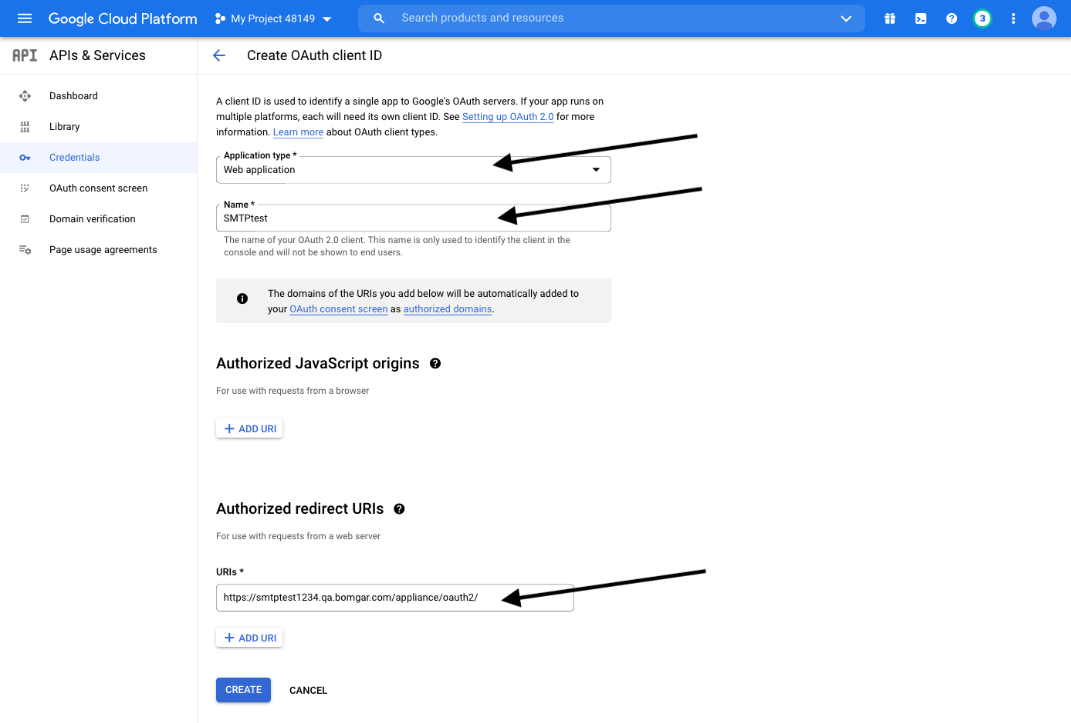
- On the create credentials page, select Web application for the Application type. Additional fields appear when this is selected.
- Enter a name for the application.
- Scroll down to Authorised redirect URIs and click ADD URI.
- Enter the Authorization Redirect URI in the form of https://{URL OF YOUR APPLIANCE}/login/smtp-verification.
- Click CREATE.
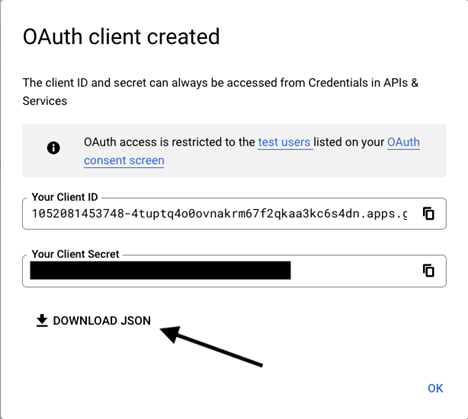
- A window confirms creation of the OAuth client, and shows the Client ID and Client Secret. Click to download a JSON file. The file contains information that is needed in the next steps.
- Click OK to return to the APIs and services page.
Provide credentials to the SMTP relay server
- Within the Privileged Remote Access admin interface, navigate to Management > Email Configuration.
- Under SMTP Authentication Type, select OAuth2, and enter the following information:
- Email: The email address for the SMTP relay.
- SMTP OAuth Provider ID: The client_id from the JSON file generated during the Google configuration.
- SMTP OAuth Client Secret: The client_secret from the JSON file generated during the Google configuration.
- SMTP OAuth Scopes: Enter https://mail.google.com/.
- SMTP OAuth Authentication Endpoint: The auth_uri from the JSON file generated during the Google configuration.
- SMTP OAuth Token Endpoint: The token_uri from the JSON file generated during the Google configuration.
- Click Save.
- Now you can verify and connect the provider account. Click Verify Oauth2 Provider.
Ensure you are logged into the provider portal as the email address for the SMTP relay, entered above, in the same browser session. You may need to log out of your personal or admin account.