Log Into Remote Systems Using Credential Injection from the Access Console
When accessing a Windows-based Jump Item via the access console, you can use credentials from a credential store to log into the endpoint or to run applications as an admin.
Before using credential injection, make sure that you have a credential store or password vault available to connect to BeyondTrust Privileged Remote Access.
Credential injection is not available for Mac or Linux Jump Clients.
This feature is not supported for ARM-based Windows systems.
Install and Configure the Endpoint Credential Manager
Before you can begin accessing Jump Items using credential injection, you must download, install, and configure the BeyondTrust Endpoint Credential Manager (ECM). The BeyondTrust ECM allows you to quickly configure your connection to a credential store, such as a password vault.
The ECM must be installed on your system to enable the BeyondTrust ECM Service and to use credential injection in BeyondTrust Privileged Remote Access.
System Requirements
- Windows Vista or newer, 64-bit only
- .NET 4.5 or newer
- To begin, download the BeyondTrust Endpoint Credential Manager (ECM) from BeyondTrust Support.
- Start the BeyondTrust Endpoint Credential Manager Setup Wizard.
- Agree to the EULA terms and conditions. Mark the checkbox if you agree, and then click Install.
If you need to modify the ECM installation path, click the Options button to customize the installation location.
You are not allowed to proceed with the installation unless you agree to the EULA.
- Click Next on the Welcome screen.
- Choose a location for the credential manager, and then click Next.
- On the next screen, you can begin the installation or review any previous step.
- Click Install when you are ready to begin.
- The installation takes a few moments. On the screen, click Finish.
To ensure optimal up-time, administrators can install up to three ECMs on different Windows machines to communicate with the same credential store. A list of the ECMs connected to the appliance site can be found at /login > Status > Information > ECM Clients.
When ECMs are connected in a high availability configuration, the BeyondTrust Appliance B Seriesroutes requests to the ECM in the ECM Group that has been connected to the appliance the longest.
If you get a Windows plugin error during installation, locate and unblock BeyondTrustVaultRestPlugin.dll.
Configure a Connection to Your Credential Store
Using the ECM Configurator, set up a connection to your credential store.
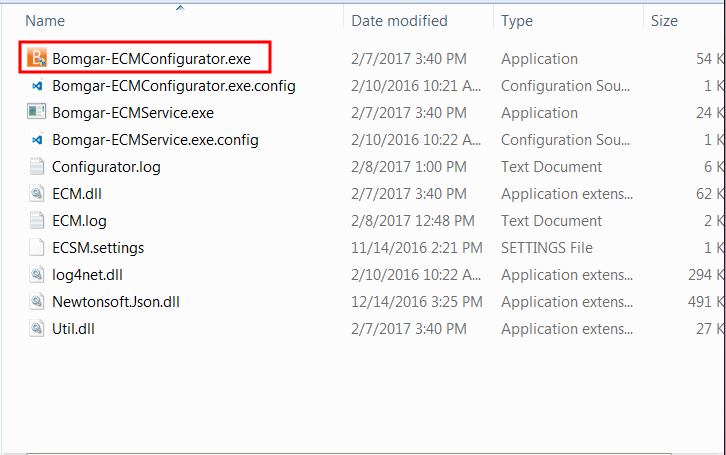
- Locate the BeyondTrust ECM Configurator you just installed using the Windows Search entry field or by viewing your Start menu programs list.
- Run the program to begin establishing a connection.
- When the ECM Configurator opens, complete the fields. All fields are required.
| Field Label | Value |
|---|---|
| Client ID | The ID for your credential store. |
| Client Secret | The secret key for your credential store. |
| Site | The URL for your credential store instance. |
| Port | The server port through which the ECM connects to your site. |
| Plugin | Click the Choose Plugin... button to locate the plugin. |
- When you click the Choose Plugin... button, the ECM location folder opens.
- Paste your plugin files into the folder.
- Open the plugin file to begin loading.
If you are connecting to a password vault, more configuration at the plugin level may be needed. Plugin requirements vary based on the credential store that is being connected.
To apply new settings in the configuration, restart the ECM service.
Use Credential Injection to Access Remote Systems
After the credential store has been configured and a connection established, the access console can begin using credentials in the credential store to log into remote systems.
- Log into the access console.
- Jump to a remote system with a Jump Item installed as an elevated service on a Windows machine.
- Click the Play button to begin screen sharing with the remote system. If the remote system is at the Windows login screen, the Inject Credentials button is highlighted.
- Click the Inject Credentials button. A pop-up credential selection dialog appears, listing the credentials available from the ECM.
- Select the appropriate credentials to use from the ECM. The system retrieves the credentials from the ECM and injects them into the Windows login screen.
- The representative is logged into the remote system.
Choose from Favorite Credentials for Injection
After you have used a set of credentials to log into an endpoint, the system stores your preferred credentials for the endpoint and the context in which they were used (to log in, to perform a special action, to elevate, or to push) in the B Series Appliance database. The next time you use a credential to access the same endpoint, the credential injection menu makes a recommendation for which credentials to use. The credentials are displayed at the top of the credentials list, under Recommended Accounts, followed by any remaining credentials. If no credential history exists for an endpoint, the B Series Appliance displays all possible credentials, grouped by accounts that are associated with the Jump Item and not associated with the Jump Item. Jump Item associations for accounts and account groups are configured in /login.
The credential list recommends no more than five credentials.
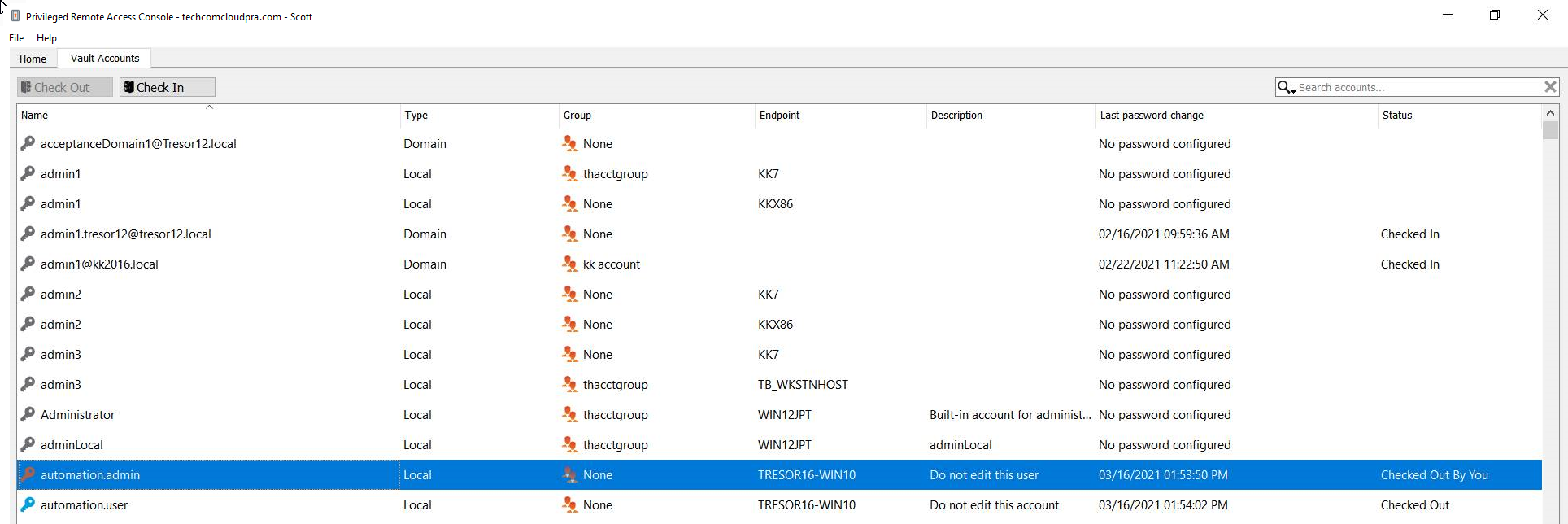
Check Out and Check In Vault Credentials
You can easily access the Privileged Remote Access Vault directly from the access console. This allows you to check out and check in credentials when needed, either during a session or on your local machine.
Select the Vault Accounts tab to see a list of available credentials and associated information.