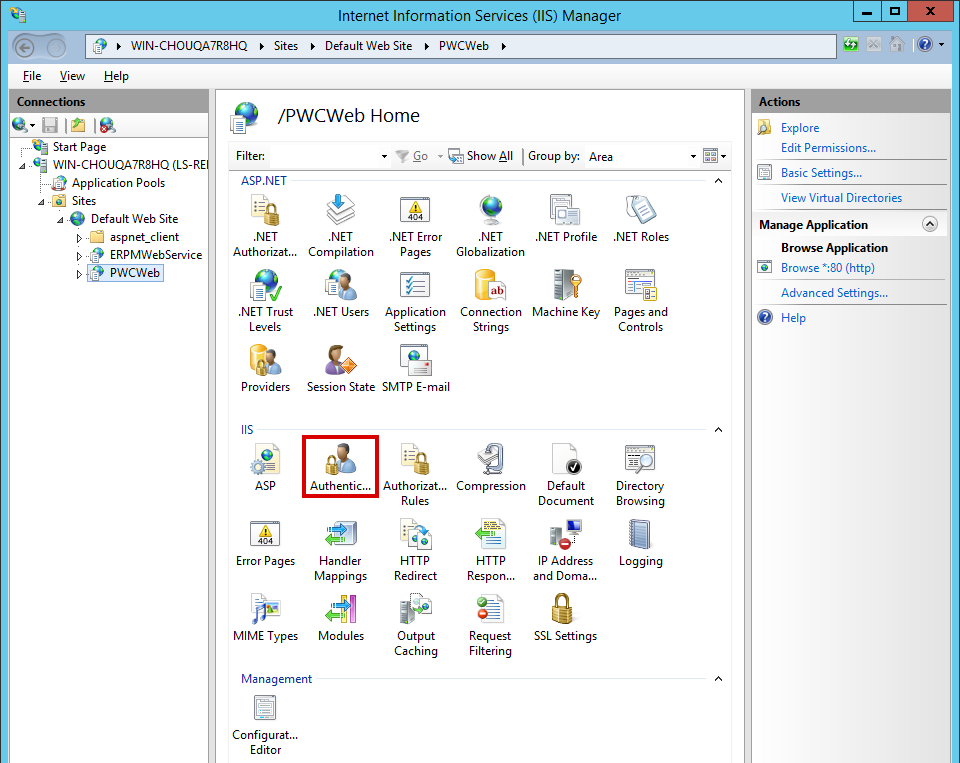
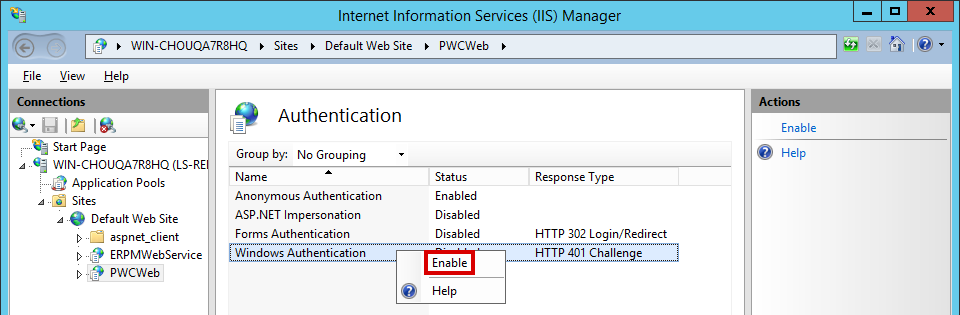
Enable Integrated Windows Authentication
When you're installing or upgrading to a virtual directory, the virtual directory inherits the settings of the parent web site. Thus, if the parent web site is not configured to use Integrated Windows Authentication (or is misconfigured by also enabling another form of authentication), then your virtual directory inherits those same undesired settings.
To require Integrated Windows Authentication on your virtual directory:
- On the host server, open Internet Information Services (IIS) Manager.
- Expand your server node, then Sites, and then your web site.
- Select your virtual directory. The default for the web app is PWCWeb, and the default for the web service is ERPMWebService.
- From the IIS section of the center pane, open Authentication.
- Right-click on Windows Authentication and select Enable.
- If any other forms of authentication are enabled, right-click on those methods and disable them.
Your browsers may require additional configuration, as described below.
Internet Explorer
For Internet Explorer to allow Integrated Windows Authentication, the URL must be seen as being part of the local intranet rather than the internet or a trusted network. Internet Explorer will automatically recognize a location as being in the intranet zone only if its location is entered with its short name rather than its fully qualified domain name (FQDN).
If you access the web app and web service using their short names, your Integrated Windows Authentication configuration should be complete, SSL certificates permitting. If you access the web app and web service using their FQDNs, Internet Explorer will not treat these as intranet-zone items, and Integrated Windows Authentication will fail.
To allow Integrated Windows Authentication when using FQDNs, each user must have the web app and web service FQDNs added to the intranet zone in Internet Explorer. You may use a group policy to push out the proper settings.
To add the FQDNs to a single user's intranet zone:
- Select Tools > Internet Options > Security.
- Select the Local intranet icon.
- Click Sites.
- Add your web app and web service FQDNs to the list.
Google Chrome
Recent versions of Chrome support Integrated Windows Authentication when run from a Windows host, without further configuration required.
For Chrome to support Integrated Windows Authentication in scenarios where cross-origin requests (CORS) must be used, you must launch Chrome with the following flags:
--disable-web-security --user-data-dir=SOMEDIRECTORY
Chrome will display a security warning. You can ignore this warning.
Mozilla Firefox
For Firefox to allow Integrated Windows Authentication, the operating system must be joined to a trusted domain, and the following configuration must be made to the browser's profile:
- For Kerberos authentication: network.negotiate-auth.trusted-uris
- If Kerberos ticket passing is required: network.negotiate-auth.delegation-uris
- If NTLM authentication is allowed: network.automatic-ntlm-auth.trusted-uris
For the Kerberos exchange, define the domain name. If your domain name were example.int, you would enter .example.int (notice the leading dot).
These settings may be lost between Firefox upgrades.
When the web app and web service are on separate machines and work with cross-origin requests (CORS), Firefox may not function properly when using Integrated Windows Authentication.