Delegate Permissions for Disconnected Account Access
To retrieve passwords for or to elevate to disconnected systems, you must create lists of delegated users. You can delegate permissions through the web app or the management console. You can grant permissions either before or after you enroll disconnected systems.
Permissions are granted on a per-list basis rather than a per-machine basis.
For more information on enrolling systems, please see Enroll Endpoints in a Disconnected Account List.
All-access users can automatically retrieve any password. Other users to require access to disconnected passwords must be granted permission. Delegated users can see only the lists to which they have been granted access. Lists must already exist before permissions may be granted.
Delegating access to systems under disconnected account management (DAM) is separate from the normal delegation model. DAM delegation must be performed in the web app or management console by a user with the All Access permission.
While DAM delegation does not fall under global delegation rules and permissions, a DAM-delegated identity still requires standard login permissions to the web app and must, therefore, be in the global delegation list.
Grant Permissions through the Web App
- Log into the web app with an all-access user account.
- Go to Passwords > Disconnected Accounts.
- Click the List Permissions button next to the list you want to manage.
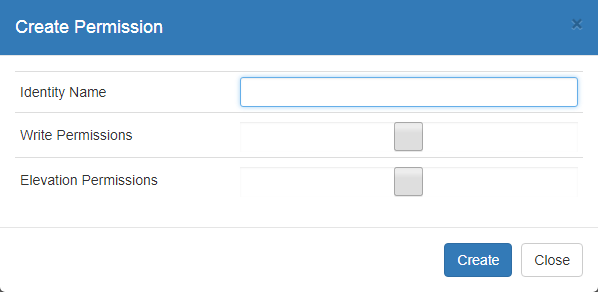
- If this is your first identity for this list, a dialog automatically appears. Otherwise, click the Create New List button (+) near the top left.
- Enter an Identity Name to add to this list.
To prevent slow web performance, you cannot look up names. Instead, you must manually enter the identity exactly as it appears in the web application Settings > Delegation list. For example, domain/admin, jsmith, or Administrator User.
- Check Write Permissions if this identity should be allowed to modify settings associated with this list. If you leave this unchecked, this identity can only see this list's enrolled systems and their passwords. Write permissions include:
- Creating and changing password policies for the list
- Viewing endpoint machine and password information for the list
- Deleting endpoint machines from the list
- Viewing log information for the list and all associated machines
- Changing delegations on the list
- Check Elevation Permissions if this identity should be allowed to elevate user accounts on managed systems. Remember that checking this option allows the identity to elevate to all systems in the list.
- Click Create.
- After you've added an identity, you will see it in the delegation list. Click Edit Policy to modify its settings or Delete Policy to remove this identity's permissions to this list.
Grant Permissions through the Management Console
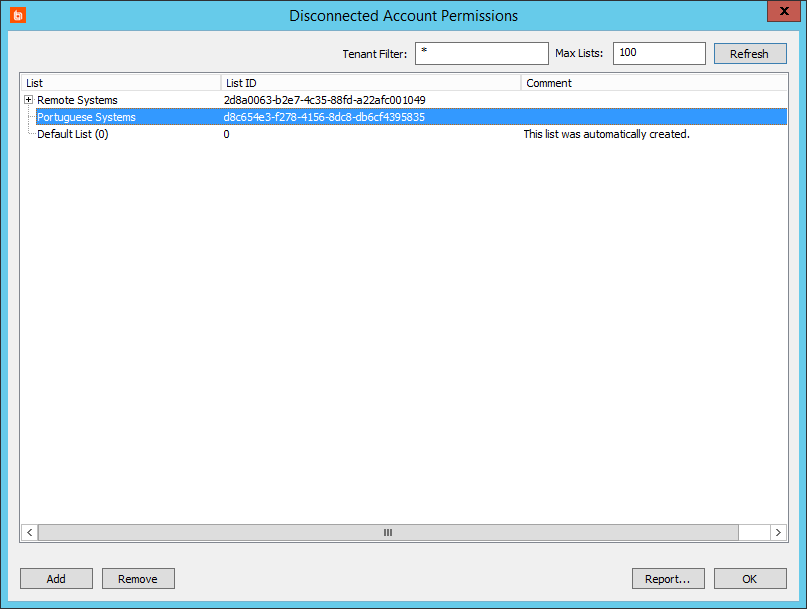
- In the management console, select Delegation > Web Application Disconnected Account Permissions.
- Select a list to add a delegation to, then click Add.
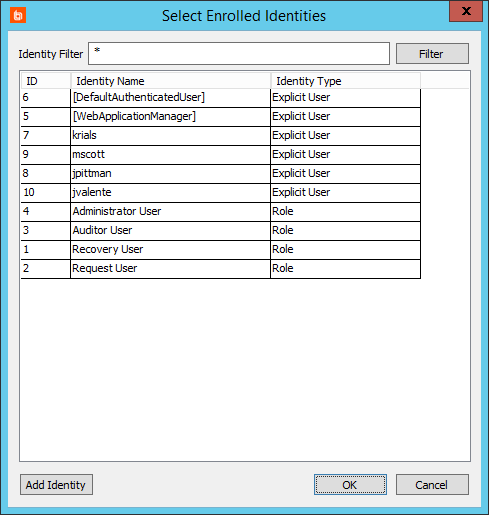
- From the Select Enrolled Identities dialog, choose one or more identities which should be allowed to access this list.
To add a new identity, click the Add Identity button, and complete the Add Delegation Identity information.
For more information about adding identities, please see the Privileged Identity Admin Guide (PDF).