Set Up Shadow Accounts
Shadow accounts allow users to connect to a system with a specific application and choose which account to connect with. The normal paradigm requires users to go the Managed Passwords section and find the target system and local account for the application. While this works for many scenarios, it is not very flexible, and it does not address the need to be able to connect domain or directory accounts to other systems or applications.
With a shadow account, users can go to the system or application in the Systems View of the web application and launch an application. A list of applications is presented, and users can determine which account, local or central (domain or directory), to connect with.
To use shadow accounts, the View Systems and Allow Remote Sessions global delegation permissions must be assigned. Once permissions are granted, additional configuration to map shadow accounts must be performed.
Even when users have All Access privileges, shadow accounts are first mapped and associated with application permissions. To use shadow accounts, a per-application rule must be established for the target user. Follow the steps below to add a new shadow account mapping.
- Open the management console.
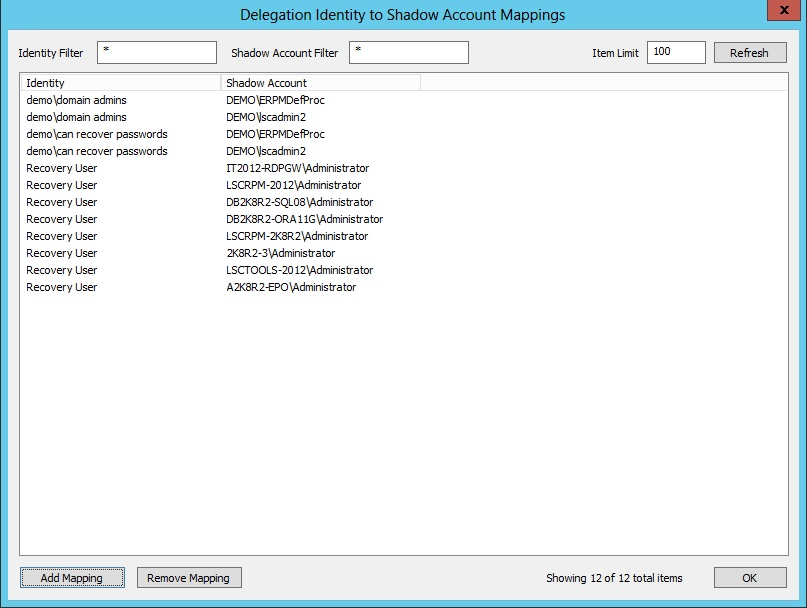
- Go to Delegation > Web Application Identity to Shadow Account Mappings.
- Click Add Mapping.
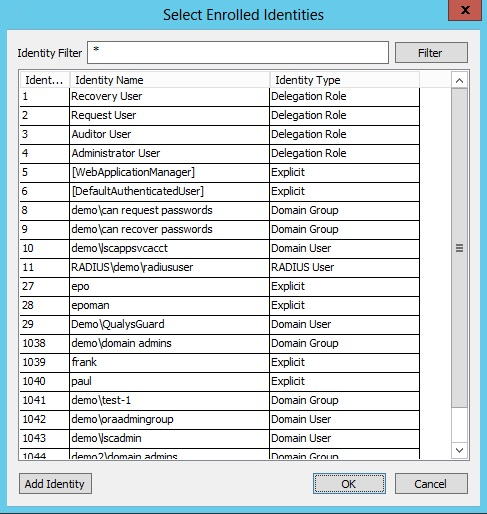
- Select the target identity from the list of available identities. Click OK.
- Select from the available managed and stored identities and click OK. The new mappings are now visible in the list of available mappings.
- Click OK.
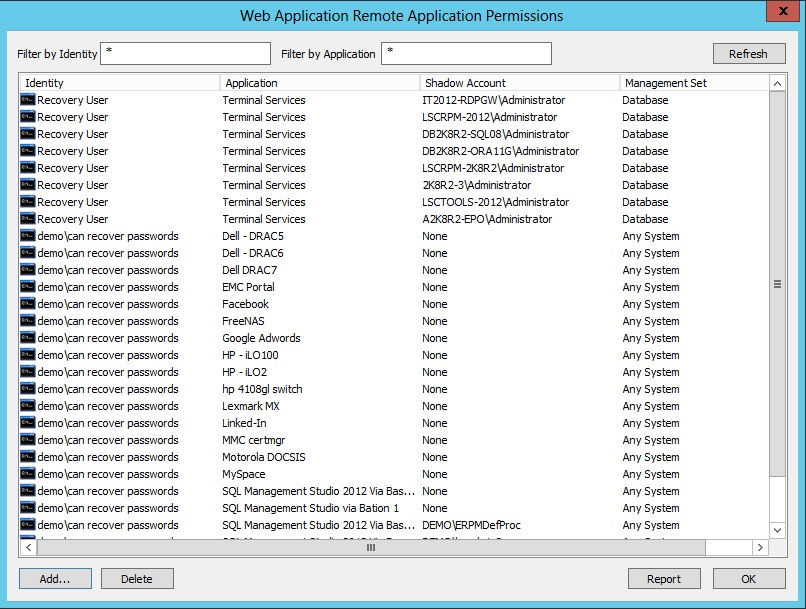
- Go to Delegation > Web Application Remote Application Permissions and click Add.
- Select the identity and click OK.
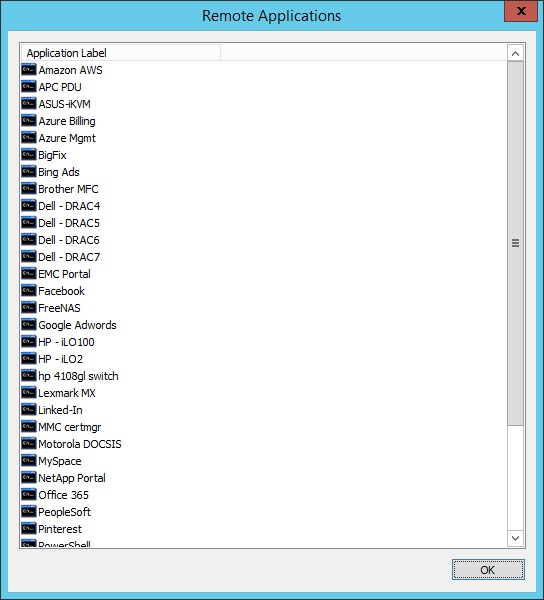
- A list of remote applications is presented. Select the target application to make available. Click OK.
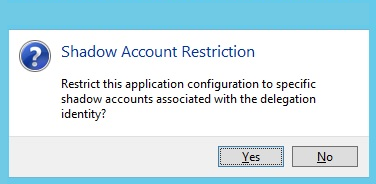
- A Shadow Account Restriction prompt appears. Click Yes to assign one or more shadow accounts the user can use when launching the specified application.
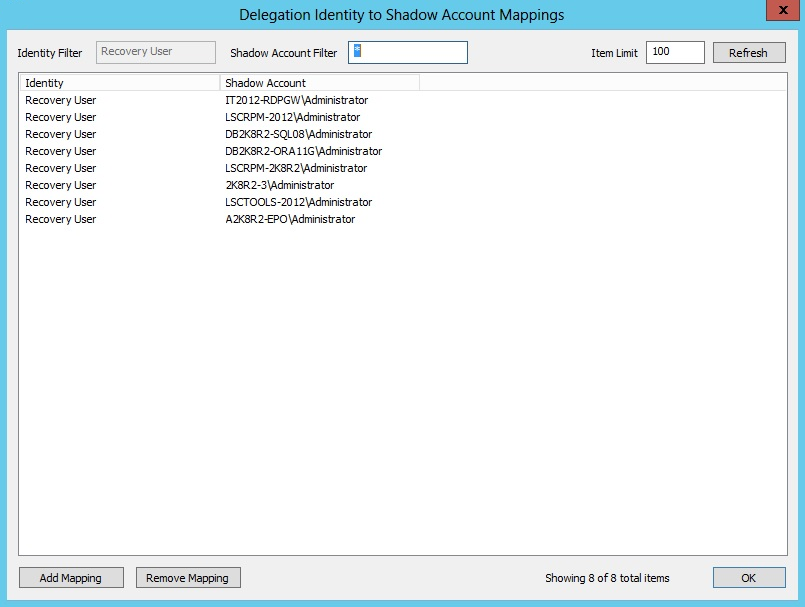
- Based on the selected user, a list of available corresponding mappings is presented. Select the mapping configured for the target user and selected applications. Click OK.
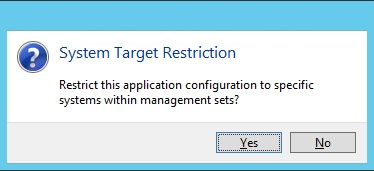
- A System Target Restriction prompt appears. If you want to restrict the applications and or shadow account mappings to a specific list of systems, click Yes. Otherwise, click No.
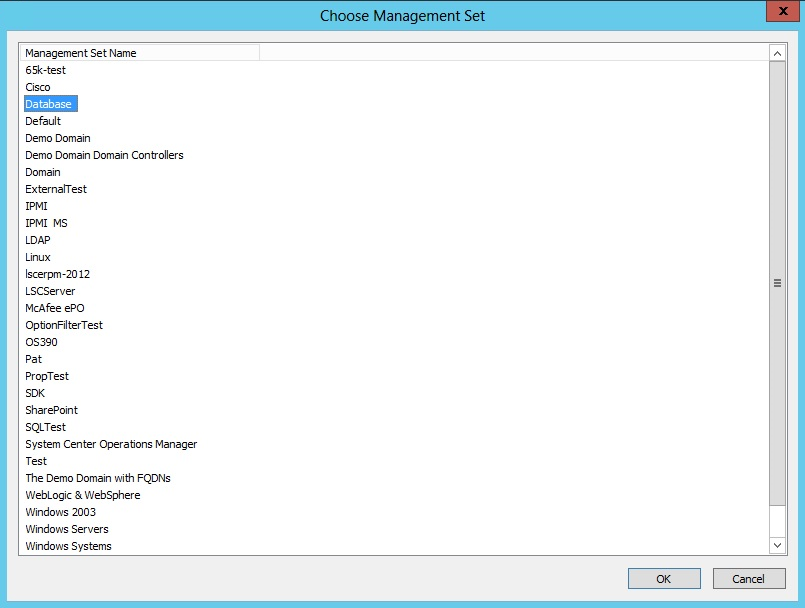
- If you click Yes, a list of management sets is presented.
- Select the desired management set and click OK.
- The new mapping is presented in the Web Application Remote Application Permissions dialog. You can delete any mappings you want to excluse. Reports can be generated from this page.
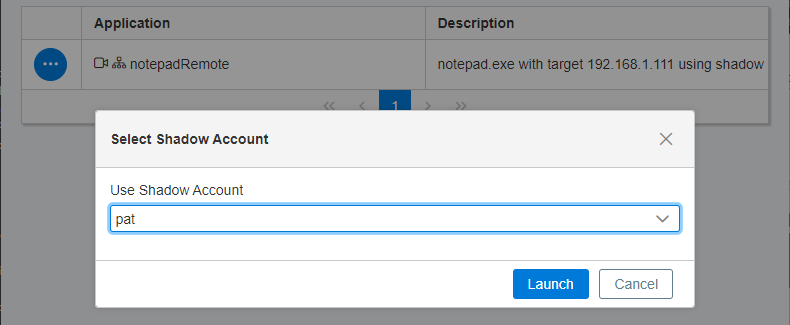
- To use the mappings, log in to the web application and locate the system that has the application you wish to launch. Click the ellipsis button for the application, and then select Launch.
If the Launch option is not available, the user does not have the Allow Remote Sessions permission, or a Shadow Account Mapping is not present.
- Select the shadow account, and then click Launch.
For 7.1.0 and later releases, shadow account information is presented as command line input arguments and can be used with replacement arguments in the same way that stored credentials passed to client applications could be configured in earlier versions.
In releases earlier than 7.1.0, shadow account credentials were used to run the client applications, but the account and password information was not provided to the client application as command line input arguments.
The implication of this change is that the shadow account is exposed to the client application’s context if the client application’s configuration specifies the shadow account credential as a command line input argument. Previously, shadow account credentials could not be exposed to the client application’s context because the client application was launched with the credential, but the credential was not available to the application.