Multifactor Authentication using an Identity Provider
Multifactor authentication (MFA) using an identity provider can be configured for messages in Endpoint Privilege Management. Identity providers supported by Endpoint Privilege Management include those using OpenID Connect (OIDC) and RADIUS protocols, and BeyondTrust should be setup as a Native or Desktop app within your Identity Provider configuration.
The RADIUS protocol is supported on Windows OS only.
In Endpoint Privilege Management, messages can be designed with a combination of authentication and authorization settings.
- Authentication: MFA with an identity provider, user credential, and smart card
- Authorization: Challenge / response authorization
Authentication and Authorization Groupings in Endpoint Privilege Management
Groupings support and/or logic:
- Groupings by authentication: Setting more than one way the end user can authenticate, which can include the typical authentication methods (user credential, designated user, and smart card) and MFA with an identity provider.
In the Message Designer, pair Step 1a - User Authentication with Step 1b - Multifactor Authentication. This can be and/or configuration.
- Groupings by authentication and authorization: Authentication methods paired with authorization always use or logic. Authorization applies an additional challenge / response layer to the end user accessing an application. The challenge / response provides an alternative to MFA authentication if that method is unavailable (for example, the browser is unavailable or the end user phone is not available).
Here are some grouping scenarios:
- MFA and Designated User or challenge / response: The end user must successfully respond to all authentication prompts to access an application. Challenge / response is optional.
- MFA or Designated User or challenge / response: The end user must successfully enter either MFA or Designated User credentials. Challenge / response is optional.
- MFA and User authentication or challenge / response: The end user must successfully respond to all authentication prompts to access an application. Challenge / response is optional. When this authentication is combined, the Step 1c - Authentication Grouping is automatically set to and logic.
- MFA or None as the Authentication Type or challenge / response: The end user must access the application through the identity provider or challenge / response method.
Workflow
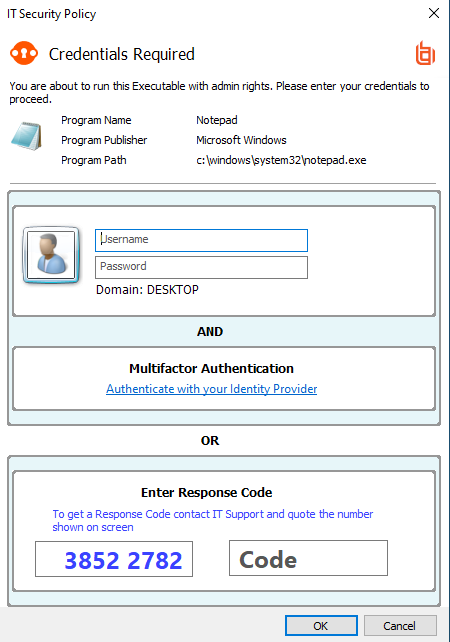
The workflow depends on the combination of settings configured on the Message Design page. In the following screen capture, the authentication methods are joined with and logic.
The end user must click the link which opens the default browser to the identity provider logon page. The end user must successfully authenticate with the identity provider, then return to the Confirm Elevation dialog box to enter the user credential.
Alternatively, the end user enters the response code to gain access.
Add an Identity Provider
You can configure the identity provider in the following places:
- Endpoint Privilege Management Settings node
- Messages node
Identity provider configuration is a global setting and applies to all Windows messages.
To add the identity provider:
- Expand the Windows node or OS X node.
- Right-click Messages > Set Idp Authentication.
- Click the relevant tab for the authentication protocol required by your Identity Provider (OIDC or RADIUS).
- Enter the identity provider details:
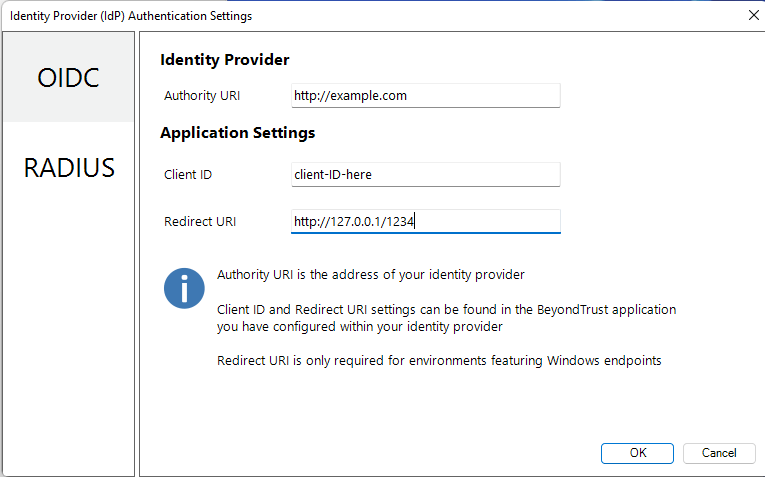
- OIDC Settings
- Authority URI: The address of your identity provider.
- Client ID: Must match the same value configured for your identity provider's BeyondTrust application.
- Redirect URI: Must match the same value configured for your identity provider's BeyondTrust application. The format is http://127.0.0.1:port_number, where port_number is an open port on your network. The port_number is only needed if required by your identity provider.
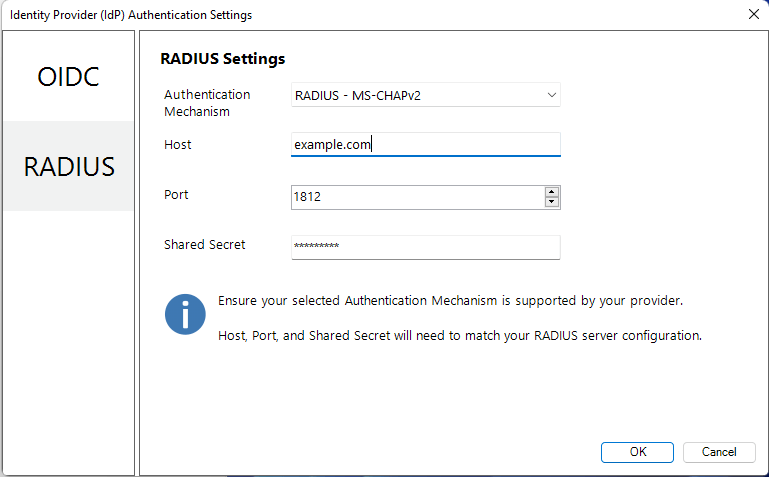
- RADIUS Settings
- Authentication Mechanism: The authentication type that is required by your RADIUS server. Supported authentication mechanisms are MS-CHAPV2 or PAP.
- Host: The hostname of your RADIUS server.
- Port: The port number for connecting to your RADIUS server.
- Shared Secret: The secret key required by your RADIUS server.
You can also configure the identity provider on the Message Design page.
For more information, see Message Design.
Add the Endpoint Privilege Management Application to Microsoft, Okta, or Ping Identity
The procedures in this section are specific to OIDC implementations.
Create an App Registration in Microsoft Entra ID
Login to your Azure portal https://portal.azure.com.
Microsoft can change functionality at any time. The screen captures in the following procedure were accurate at the time of writing.
- Navigate to your Microsoft Entra ID.
- Click App registrations.
- Select New registration.
- Enter a name for your app registration. Use a name related to Endpoint Privilege Management.
- Click Register.
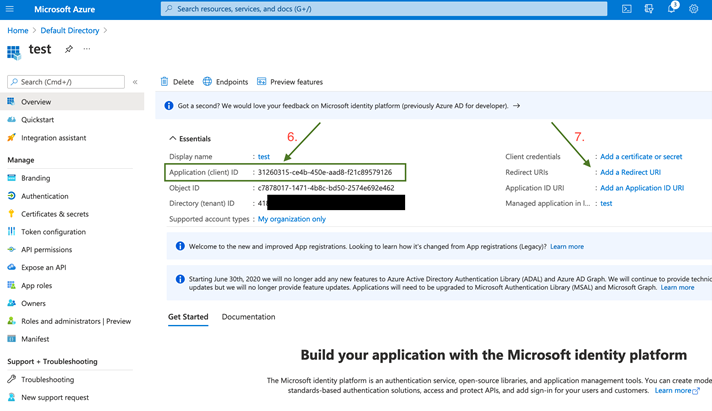
- Copy and note your Application (Client) ID for use in the Policy Editor later.
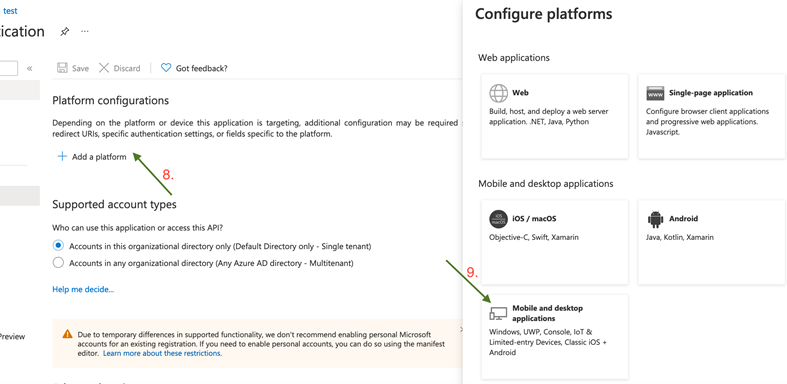
- Click Add a Redirect URI.
- Click Add a platform.
- Select Mobile and Desktop Applications.
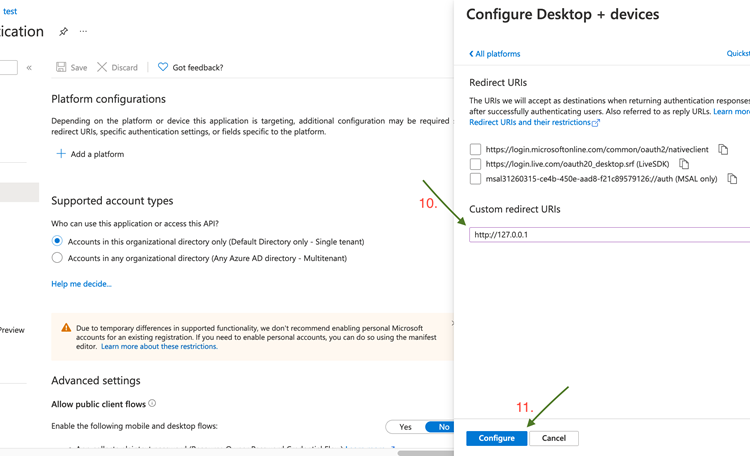
- Add a Custom Redirect URIs and set the value to:
http://127.0.0.1
- Click Configure.
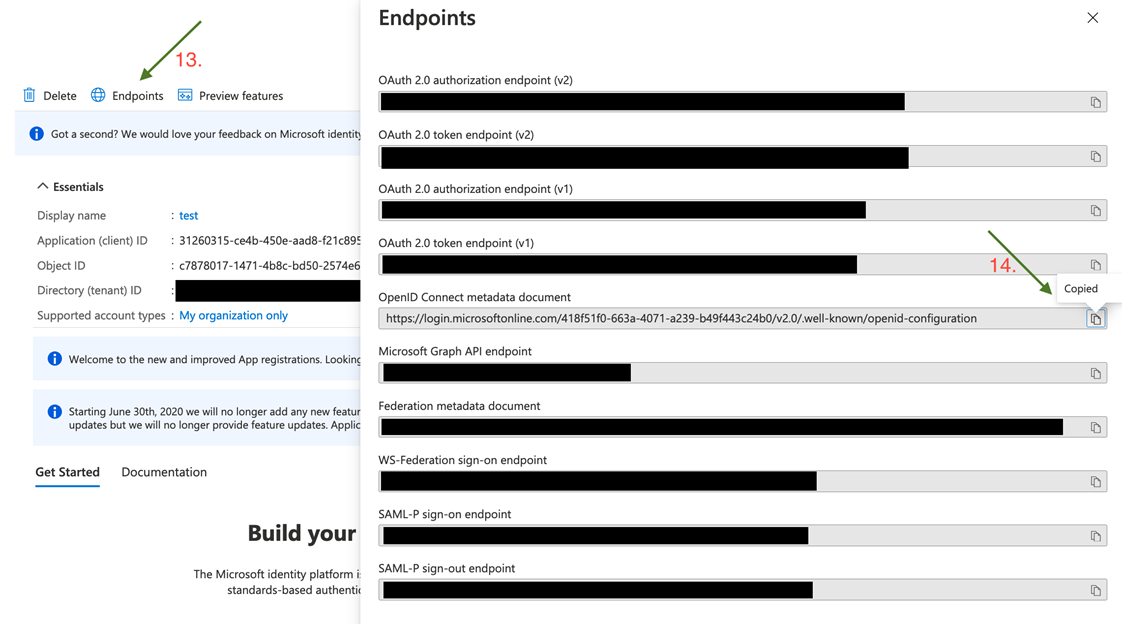
- Go back to your newly created app registration.
- Click Endpoints. The endpoints display on the right.
- Copy the value from the OpenID Connect metadata documentbox. Only this part of the URL is required: https://login.microsoftonline.com/87549b3f-a6ba-4ca4-9d99-ff2944ac4234/v2.0
The configuration is now complete. The following values are required to configure the IdP in the Endpoint Privilege Management Policy Editor for both Windows and macOS.
- Authority URI: The value copied in step 14.
- Client ID: Application (Client) ID from step 6.
- Redirect URI: Custom redirect URIs set in step 10.
Enforce MFA For Every Logon Attempt
In Entra ID, you might want users to always go through the multi-factor authentication process every time they try to access an application in a rule (if multi-factor authentication is configured in the message).
Add Endpoint Privilege Management to Okta
- Start your Okta instance.
- Click Create App Integration.
- In the Create a new app integration section, select OIDC - OpenID Connect.
- Select Native Application as the application type.
- Select Authorization code for the Grant type.
- Add the sign-in and sign-out URIs.
- Sign-in redirect URI: https://{dns}-services.pm.beyondtrustcloud.com/oauth/signin-oidc
- Sign-out redirect URI: https://{dns}-services.pm.beyondtrustcloud.com/oauth/signout-callback-oidc
- Select the controlled access applicable to your organization, and then click Save.
After you add EPM to Okta, you can get the information you need to set up the OpenID Connect authentication.
- Go to the application instance for Endpoint Privilege Management.
- Select General Settings, and then click Edit.
- For the EPM OpenID Connect Setup Wizard, you need to copy the following information from the Edit page:
- Domain: Prefix the protocol HTTPS://
- Client ID
- Client Secret
Confirm the domain name configured in Okta. This domain name might be different than the domain configured for your email address. For example, while the domain managed in Okta might be domain.com, the email address might be user@email.com. Both pieces of information are required.
- You can now visit the set-up URL and enter the domain, client ID, and client secret information.
Add Endpoint Privilege Management for Mac to Ping Identity
We currently support PingOne, the SaaS service from Ping Identity.
- Start your Ping Identity instance.
- In the menu, click Connections, and then click Applications.
- At the right of the Applications title, click the plus sign (+) to add an application.
- Enter a name for the application (required), and then add a short description (optional).
- Select OIDC Web App and click Save.
- Click the Configuration tab.
- To edit the configuration, click the pencil/edit icon.
- Under Redirect URLs, click + Add, and then add the sign-in and sign-out URLs. If you are modifying an existing instance, you might need to open the General section dropdown first.
- Sign-in redirect URL: https://{dns}-services.pm.beyondtrustcloud.com/oauth/signin-oidc
- Sign-out redirect URL: https://{dns}-services.pm.beyondtrustcloud.com/oauth/signout-callback-oidc
- Under Token Endpoint Authentication Method, select Client Secret Post, and then click Save.
- Click the Resources tab.
- To edit the resource, click the pencil/edit icon.
- In the Scopes list, click the + next to profile openID to add it to the Allowed Scopes. You can also filter the list of options by OpenID to access this option.
- Click Save.
- To close the panel, at the top right of the Edit panel, click the X.
- At the right of the new application entry, toggle the switch to on to give access to users.
- Click the Configuration tab again. For the EPM OpenID Connect set-up wizard, you need to copy the following information from the Configuration page.
The Ping identify provider (IdP) configuration is now complete. The following values are required to configure the IdP in the Endpoint Privilege Management Policy Editor for both Windows and macOS.
- Issuer: Prefix the protocol HTTPS://
- Client ID
- Client secret