Endpoint Privilege Management Reporting Installation Guide
This document explains how to install and configure BeyondTrust Endpoint Privilege Management Reporting, which enables organizations to monitor and report on activity from Windows and macOS desktops and servers.
There are several methods available for centralizing audit data. The most common is Windows Event Forwarding. Endpoint Privilege Management Reporting can use Windows Event Forwarding to centralize audit data to one or more Windows Event collector server hosts.
Once audit data are collected, one (or more) instances of the BeyondTrust Event Parser component load the data into the BeyondTrust Endpoint Privilege Management database on a Microsoft SQL Server instance. All audit event data is stored in one logical SQL Server instance.
Reports provide visibility to the audit data and are implemented as custom reports in Microsoft SQL Server Reporting Services 2014 or later.
Microsoft SQL Server Reporting Services is typically hosted independently from the audit events SQL Server database instance, except for small implementations and evaluation scenarios where it may share the audit database server host.
Reporting is also available on other BeyondTrust platforms:
- BeyondTrust Endpoint Privilege Management ePO Edition. Event centralization and report presentation are built on the ePO framework agent and ePO server, with audit data storage in Microsoft SQL Server as described in this guide.
- BeyondTrust BeyondInsight platform. Refer to BeyondInsight integration guides.
This guide is intended for reporting implementations with the Endpoint Privilege Management GPO platform.
For more information, see the following:
- Event Centralization Guide
- For instructions specific to the ePO Edition, the Endpoint Privilege Management ePO Administration Guide
- Integrate BeyondTrust Endpoint Privilege Management for Windows with BeyondInsight
- Integrate Endpoint Privilege Management for Mac and BeyondInsight at https://www.beyondtrust.com/docs/privilege-management/integration/pmm-beyondinsight/index.htm
Configuration Options
There are two options for deploying the solution:
Option 1: Use a single box solution, which is suitable for evaluating the product, or for SME installations.
Option 2: Use a scaled out deployment, which is recommended for larger production environments.
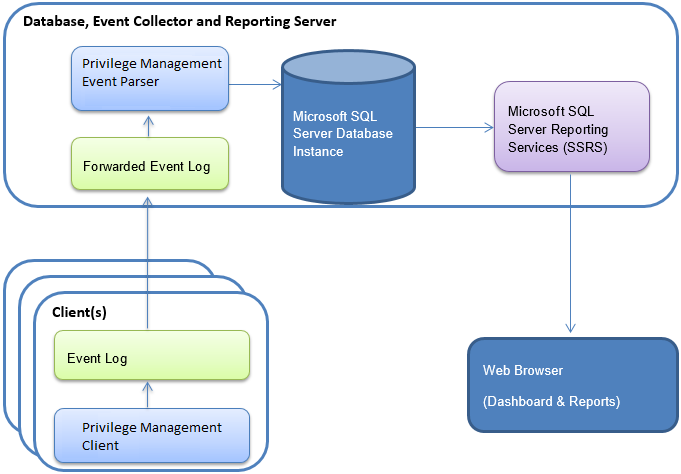
Option 1 - Single Box Solution
In this deployment scenario, one server provides all functions.
- The server must be running Windows Server 2016 or later.
- SQL Server 2014 or later must be installed on the server.
For an evaluation:
- A Windows Client, such as Windows 10, is supported.
- SQL Server Express is supported.
Select the Reporting Services feature in the feature selections page of the Microsoft SQL Server installer. To install Reporting Services, use Native Mode.
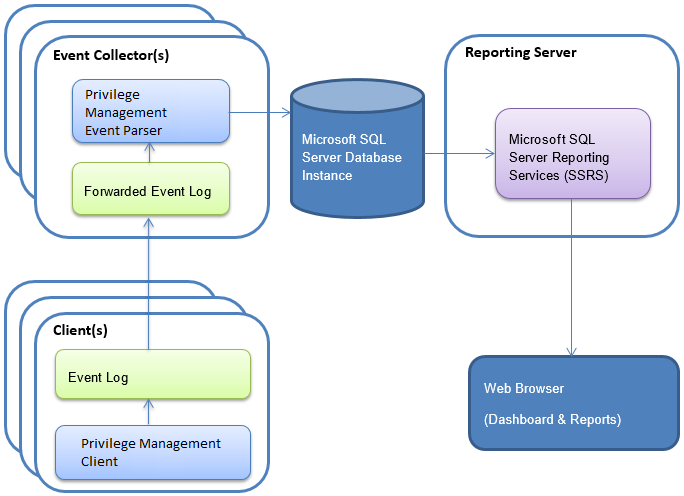
Option 2 - Enterprise Scaled Out Deployment
In this deployment scenario the Event Collectors, Database and Reporting Server are installed on dedicated servers.
SQL Server Database
The database is a repository for the data collected from the clients.
- The minimum version required is SQL Server 2014.
- Clustered databases are supported.
- When you install SQL Server, you must select a case insensitive collation. We recommend you select Latin1_General_CI_AS.
- EPM installations require Azure SQL Server which is also supported.
- Windows Integrated Authentication must be used for Event Parser connections.
- SSRS connections can use either Windows Integrated Authentication or SQL Server Authentication.
- TCP/IP connections must be enabled on the SQL Server to allow the Event Collector service to submit events.
- Microsoft SQL Server CE is not supported.
The database is created during the installation of the Endpoint Privilege Management Reporting database component. By default, the database is named BeyondTrustReporting. The installation provides the option to provide a custom database name.
Support for SQL Always On Availability Group
The Endpoint Privilege Management Reporting database is updated to allow it to run within a SQL Always On availability group. This update prevents the CopyFromStaging scheduled job from running on the secondary replica in the availability group, so that it only ever runs on the primary replica.
To add the database to an Always On availability group, the SQL recovery model for the database needs to be set to Full.
When using Full recovery model, ensure that best practice is followed for backing up the Endpoint Privilege Management Reporting database transaction log to prevent disk space from filling up. The regular execution of the CopyFromStaging job can cause the transaction log to quickly fill up disk space if the transaction log is not regularly being backed up.
Install the Endpoint Privilege Management Reporting database on the primary replica server, then add to the availability group, where it is then replicated to the secondary replica. There is no need to install the Endpoint Privilege Management Reporting database directly on the secondary replica server.
Additionally, when using the Endpoint Privilege Management Reporting database in an Always On availability group, use the SQL Agent job (PGInsertData) to run the CopyFromStaging stored procedure, not the Service Broker job. The Service Broker has been found to be unreliable starting up again after failover. The Service Broker is currently the default job when installing the Endpoint Privilege Management Reporting database.
To switch to the SQL Agent job go through the following steps after installing the Endpoint Privilege Management Reporting database:
- Execute the Create_ER_Database_Agent.sql script (located in the SQL folder of the PrivilegeManagementReporting zip file) against the Endpoint Privilege Management Reporting database on the primary replica. This will remove the Service Broker job and create the SQL Agent job on the primary node.
- Configure read-only access to the secondary replica of the Always On availability group by setting Readable secondary to Yes. This is required for step 3. See the following link for details: https://docs.microsoft.com/en-us/sql/database-engine/availability-groups/windows/configure-read-only-access-on-an-availability-replica-sql-server
- Execute the Create_ER_Database_Agent.sql script against the Endpoint Privilege Management Reporting database on the secondary replica.
Provided the Create_ER_Database_Agent.sql script is run on the primary replica first, it won’t attempt to make any changes to the database on the secondary replica. The removal of the Service Broker job will have been replicated across from the primary to the secondary replica, so this part of the script won’t run.
Running this script only creates the SQL agent job on the secondary replica. This job will run on the secondary but will not execute the CopyFromStaging stored procedure unless failover occurs, and this becomes the primary replica.
- You can now remove read-only access to the secondary replica (set Readable secondary to No).
When configuring BeyondTrust Reporting to point to the Endpoint Privilege Management Reporting database in the Always On availability group, you must use the availability group listener address instead of the primary replica server address. The listener forwards any calls to the primary replica.
To use BeyondTrust Reporting in an Always On availability group, you must use the Microsoft JDBC driver for the SQL connection. The default jTDS driver will not work with Always On.
Event Collector (Server)
The Endpoint Privilege Management Event Parser is a service that detects and submits new Endpoint Privilege Management events to the database. Typically, the Event Parser is installed on a dedicated Windows Event Collector Server, and by default scans the ForwardedEvents Log for new events.
The Event Parser service can be configured to scan the Application Event Log if required, by editing the following Registry value:
HKEY_LOCAL_MACHINE\Software\Avecto\Privilege Guard Event Parser\ REG_SZ "EventLog"
The Event Collector host should be built on Windows Server 2016 or later.
Ideally, the server is dedicated to this role.
You may configure multiple Event Collector servers that feed into a single database.
The Event Parser services are the only components which establish direct connections to the events database. This keeps the number of concurrent connections to a minimum.
Report Server
- SQL Server Reporting Services (SSRS) 2014 or later is required.
- The server must be dedicated to this role.
- The events database and SSRS can be hosted on the same SQL Server instance.
- We recommend that the SSRS instance be separate from the database instance to prevent performance issues on the database.
The SSRS reports are installed and preconfigured during the installation of the Endpoint Privilege Management Reporting Pack component. By default, the SSRS instance is named ReportServer. You can provide a custom name during the SQL Server installation.
Client Configuration
Windows Event Forwarding is the technology used to gather events from the clients running Endpoint Privilege Management Reporting.
- Event forwarding must be configured for all computers running the Endpoint Privilege Management Reporting Client that need to forward events.
- The minimum OS level required on each client is Windows 10.
- Events can be forwarded to any of the supported Windows Server OS versions (Windows Server 2016 or later).
- Each client requires Windows Remote Management (WRM) 1.1 or later installed.
For more information for installation and configuration details on Windows Event Forwarding, see the Event Centralization Guide.