Application Groups
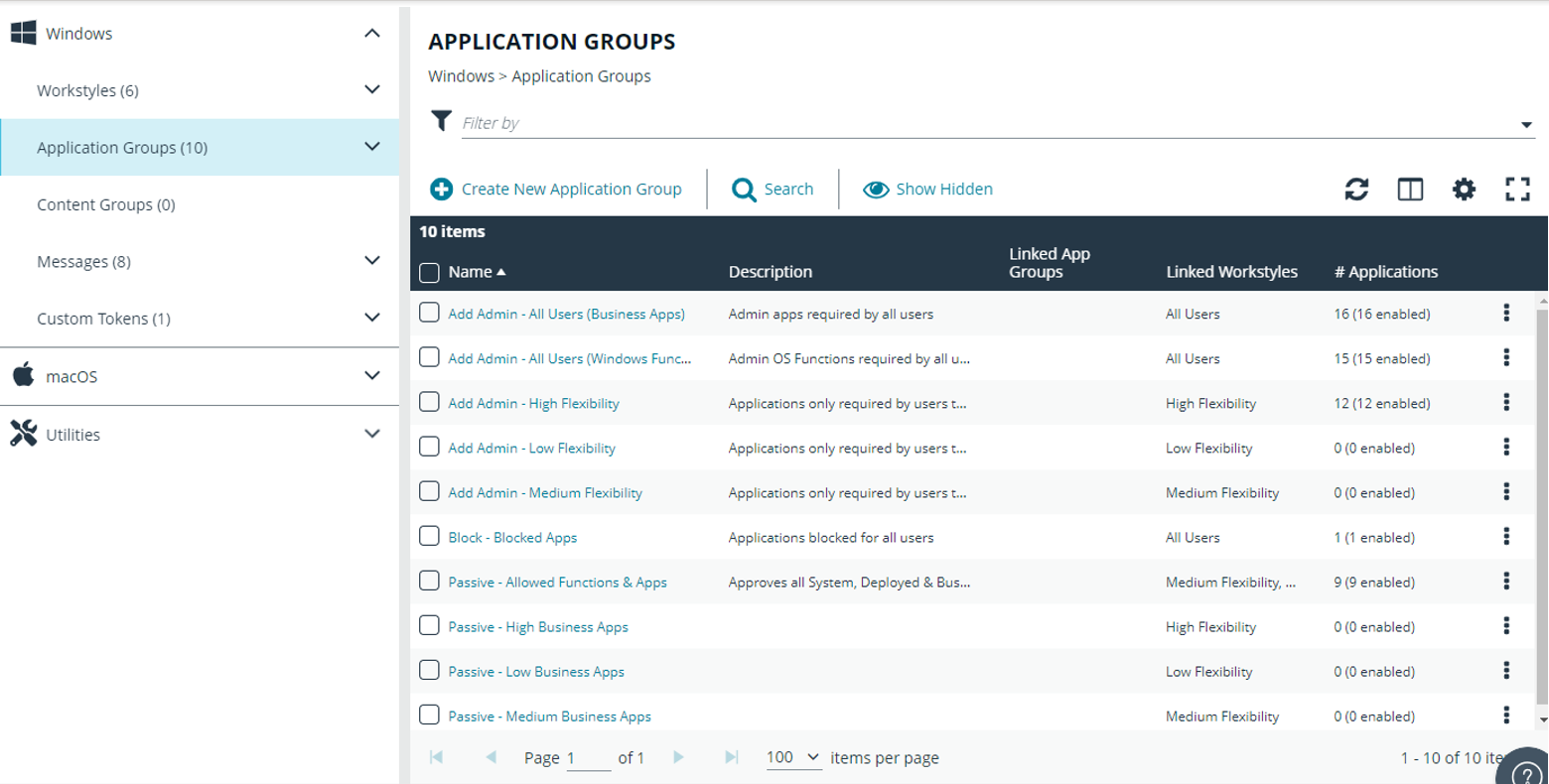
Application Groups are used to define logical groupings of applications.
Application Groups are assigned to Workstyles, so you must define Application Groups for all the applications you want to assign to a Workstyle.
Overview
When working with Application Groups, you can:
- Create, edit, and delete application groups.
- Change the name or description of the group.
- Delete an application group when it is no longer required.
- Copy an application group, and then edit the properties of the newly created group.
- Copy application definitions from one group to another and from one policy to another.
- View hidden application groups.
- Use the search feature to find an application.
Create an Application Group
There are predefined application groups available that are already populated with applications and linked to workstyles. You can, however, create application groups and customize the application and associated properties.
- On the Policy Editor page, expand Windows or macOS.
- Click Application Groups.
- Click Create New Application Group.
- Add a name and description. Click Create Application Group.
- The Application Group is now displayed in the navigation pane and the grid. You are now ready to add applications to the group.
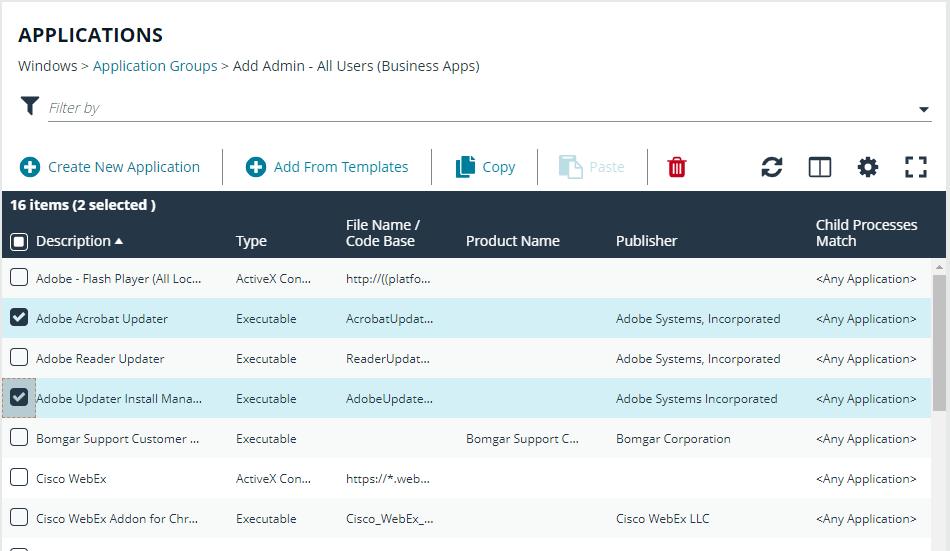
Add an Application to an Application Group
There are three ways to add an application to a group:
- Application definitions: Create an application using the application definitions and properties.
- Reports: Add an application on-the-fly from the Reports page using the collected analytics.
- Application templates: Provides a way to pick from a list of known applications.
Copy Application Definitions
For ease-of-use, copy one or more application definitions to save time when setting up an application group. Copy to another application group in the same policy or another policy.
If the Paste button is not available, check the XML is a valid application definition. Copy the XML to a text editor to confirm.
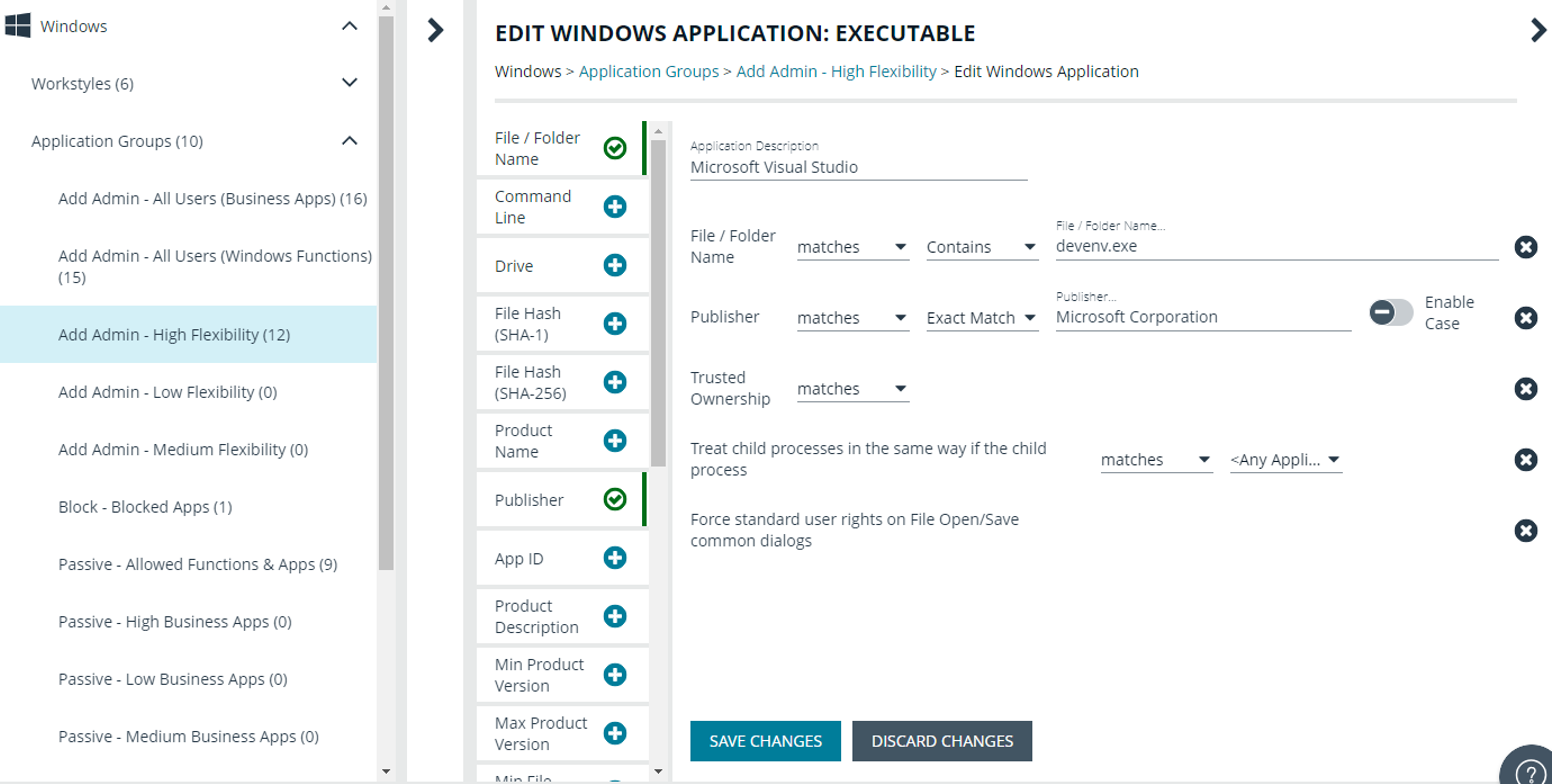
Add an Application Using App Definitions
When adding an application, you can configure the following properties:
- Application Definitions: The application definitions are the properties of an application that are used to detect the application in your environment. When the application matches on the configured criteria the rule triggers.
- Advanced Options: When adding the application, advanced settings on child processes and standard user rights enforcement can be configured.
When adding file or folder paths, you can use environment variables as part of the entry. Using environment variables is optional.
The procedure for adding an application is generally the same for every application. The matching criteria varies depending on the application.
To add an application:
- In the navigation pane, select the Application Group.
- Click Create New Application, and then select the application type.
- Enter a description in the Application Description box. Any value can be added here up to a maximum limit of 1024 characters. The description is not used in rule matching.
- From the list of application definitions, configure the matching criteria.
- (Optional) Configure the Advanced Options:
- Allow child processes will match this application definition
- Force standard user rights on File Open/Save common dialogs
- Click OK.
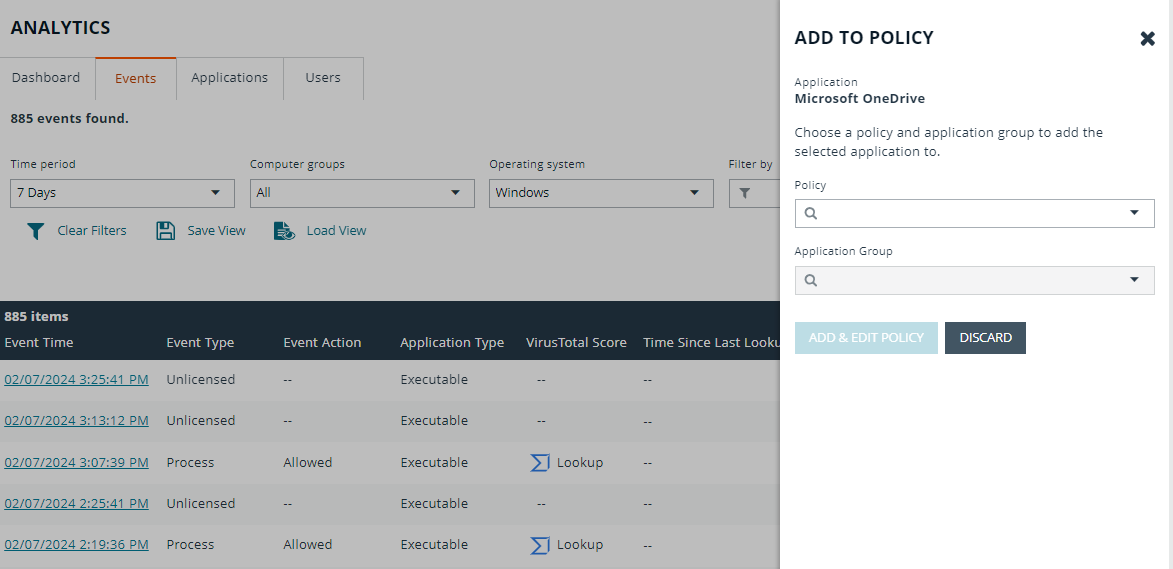
Add an Application From Reports
You can add an application to a policy based on events generated from a particular application type.
Supported event types include:
- Process
- Process with File
- COM Class
- Service
- ActiveX
- Challenge Response Failed
You can select more than one event in the list to add to the same policy. The matching criteria for all selected and compatible events are added to the policy and application group selected.
To add events to a policy:
- In the console, select Analytics from the menu.
- Click Events.
- Select one or more events in the list and click the Add to Policy icon. A message displays if you try to add unsupported event types when selecting more than one event.
- On the Add Applications to Policy page, select a policy and an application group.
- Click Add and Edit. Alternatively, click Add and Close here which adds the application to the Application Group and redirects you back to the report.
- The policy opens to the Application Groups > Applications page where you can edit the application settings. If you are adding one application, then you are directed to the application matching criteria page as shown.
Add an Application From a Template
Application templates provide a way to pick from a list of known applications. A standard set of templates is provided that covers basic administrative tasks for all supported operating systems, common ActiveX controls, and software updaters.
- On the Policy Editor page, navigate to the policy to update.
- Go to Application Groups > Applications, and then click Add From Templates.
- Select an application template from the list, and then click Add. You can select more than one template at a time.
Disable an Application
You can temporarily pause the processing of an application rule against an application in an application group. Use this feature if you are rolling out or testing new rules. Disable the application while you investigate and fix any problems.
Environment Variables
You can use the following environment variables in file path and command line application definitions.
To use the variables, enter the variable, including the % characters, into a file path or command line. EPM expands the environment variable prior to attempting a file path or command line match.
System Variables
- %ALLUSERSPROFILE%
- %COMMONPROGRAMFILES(x86)%
- %COMMONPROGRAMFILES%
- %PROGRAMDATA%
- %PROGRAMFILES(x86)%
- %PROGRAMFILES%
- %SYSTEMROOT%
- %SYSTEMDRIVE%
User Variables
- %APPDATA%
- %USERPROFILE%
- %HOMEPATH%
- %HOMESHARE%
- %LOCALAPPDATA%
- %LOGONSERVER%
Advanced Options
Allow child processes will match this application definition
If selected, then any child processes that are launched from this application (or its children) will also match this rule. The rules are still processed in order, so it is still possible for a child process to match a higher precedence rule (or Workstyle) first. Therefore, this option will prevent a child process from matching a lower precedence rule.
If an application is launched by an on-demand rule and this option is selected, then the children are processed against the on-demand rules, and not the Application Rules. If this option is not selected, then the children will be processed against the Application Rules in the normal way. You can further refine this option by restricting the child processes to a specific Application Group. The default is to match <Any Application>, which will match any child process.
If you want to exclude specific processes from matching this rule, then click …match… to toggle the rule to …does not match….
Child processes are evaluated in the context that the parent executed. For example, if the parent executed through on-demand shell elevation, then EPM will first attempt to match On-Demand Application Rules for any children of the executed application.
Force standard user rights on File Open/Save common dialogs
If the application allows a user to open or save files using the common Windows open or save dialog box, then selecting this option ensures the user does not have admin privileges within these dialog boxes. These dialog boxes have Explorer-like features, and allow a user to rename, delete, or overwrite files. If an application is running with elevated rights and this option is disabled, the open/save dialog boxes will allow a user to replace protected system files.
Where present, this option is selected by default to ensure EPM forces these dialog boxes to run with the user’s standard rights, to prevent the user from tampering with protected system files.
When enabled, this option also prevents processes launched from within these dialog boxes from inheriting the rights of an elevated application.