Endpoint Privilege Management security
Public. For Information Purposes Only.
The purpose of this document is to illustrate to technically-oriented professionals how BeyondTrust can bolster the security of their organization while simultaneously improving efficiency and end-user support.
BeyondTrust overview
BeyondTrust helps organizations maintain a secure and compliant environment, leading to increased success and improved user experience. BeyondTrust provides a series of solutions to help organizations meet their security and compliance needs, while reducing operational burdens and enabling a more productive workforce.
EPM overview
The EPM is an invaluable asset for organizations looking to centralize their endpoint privilege management. With this platform, they are able to control all of their computers from one convenient location, ensuring all computers are up-to-date and secure.
Technical challenge and least privilege
To determine the effectiveness of endpoint privilege management solutions in the fight against cyber attacks, one must first consider the underlying security principle of least privilege. By having local administrator rights, a user has the privileges to perform most, if not all, functions within an operating system on a computer. These privileges can range from installing software and hardware drivers, changing system settings, installing system updates, creating user accounts, and changing their passwords. While having these privileges makes life easier for IT Support, the organization is at a much higher risk of breach.
The least-privilege approach is a common method of managing privileged user accounts, by assigning users and programs only the minimum amount of permission necessary to complete specific tasks. This approach was developed over 40 years ago and is still the fundamental security measure for organizations wanting to reduce the number of malicious attacks. Least privilege works best when combined with the concept of allowlisting, which is when an index of approved software applications are specified to be present and active on a computer system.
The integration of least privilege and allowlisting is the basis of endpoint privilege management. Over the years, methods for achieving least privilege have evolved. Now, organizations can easily and quickly use SaaS-based solutions to deploy least privilege.
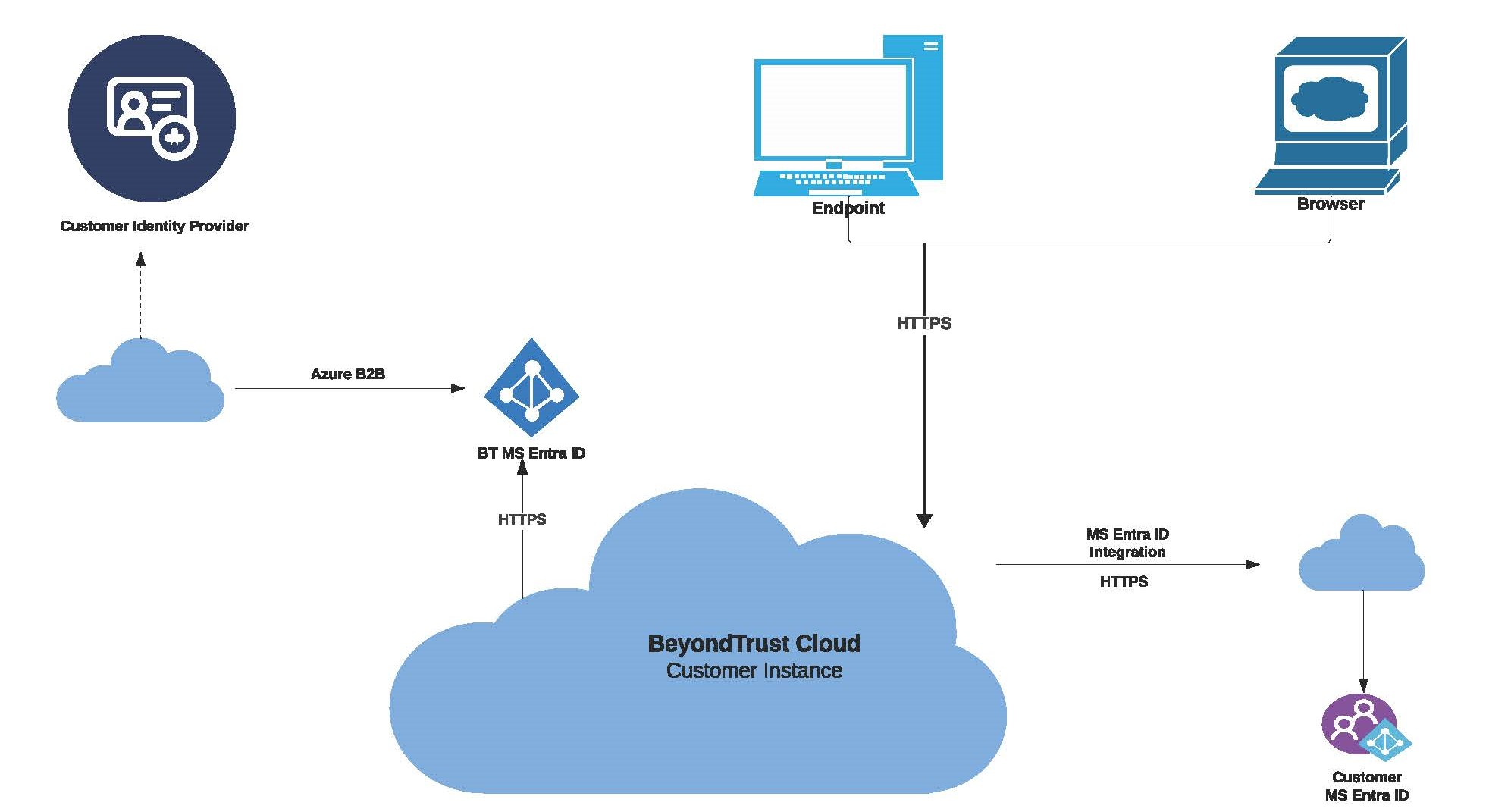
EPM architecture
Infrastructure
EPM leverages Azure Cloud Services (IaaS and PaaS) to host all its services within Microsoft Azure data centers.
The diagram provides a high-level overview of the Endpoint Privilege Management architecture hosted within Microsoft Azure data centers.
EPM configuration and secret information are securely stored in the Azure Key Vault and Azure storage account. Each customer environment has its own dedicated container within the storage account, with public access strictly blocked and only secure transfer allowed for REST API operations. Data encryption is enabled in the storage account, making use of Microsoft-managed keys, while Managed Identity is used to access the contents of the storage account. All secrets in the Azure Key Vault remain encrypted for enhanced security.
Infrastructure and physical security
Information about Azure infrastructure, physical security, and other important details can be found at Microsoft Azure Infrastructure Security. All client deployments are separate from each other, meaning that no client can access another client's infrastructure and services. Clients do not have access to the infrastructure, however, BeyondTrust's Support Team and Cloud Ops can do so if they require it for troubleshooting and production support purposes.
For more information, see Azure infrastructure security .