Configure OpenID connect
EPM supports OpenID Connect authentication. You can change your authentication provider from the default AzureB2B to OpenID Connect, or update your OpenID Connect settings, without having to contact Support.
You must first set up an EPM instance in your OpenID Connect provider. Steps are provided in the section below.
Configure an authentication provider
When you start from the default configuration, use this procedure to set up the configuration.
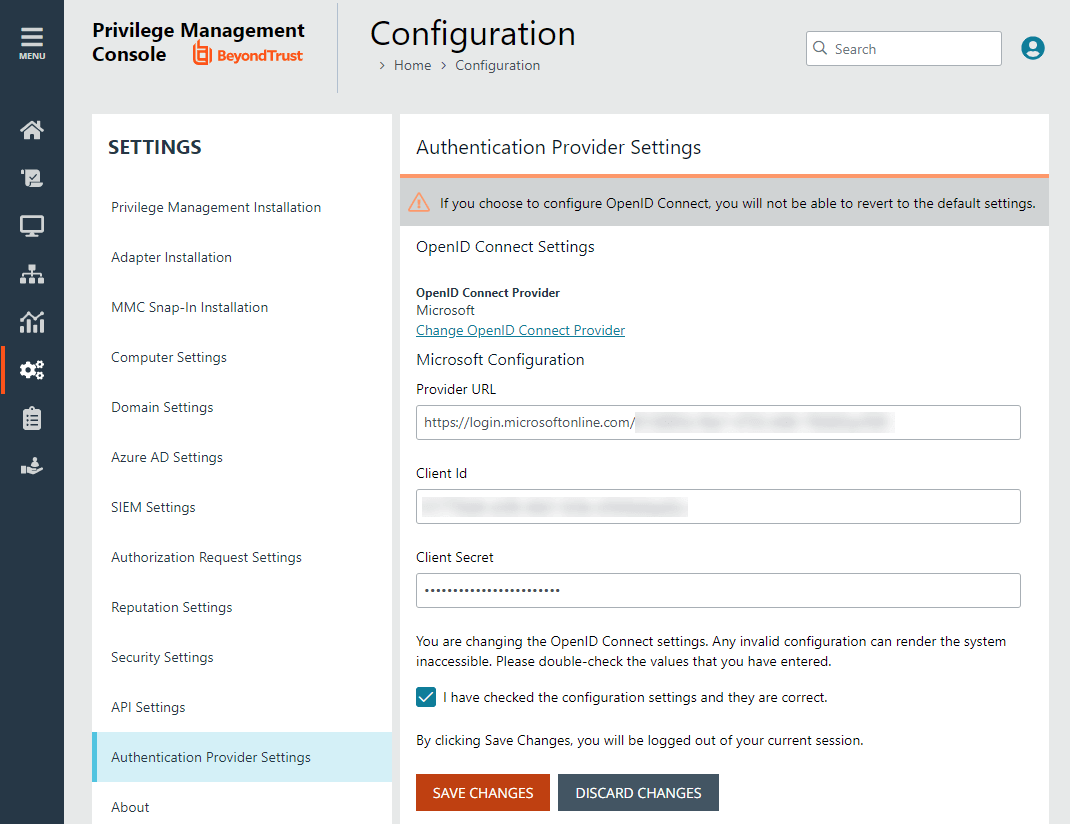
If you choose to configure OpenID Connect, you cannot revert to the default settings.
To set up an OpenID Connect provider:
- Select the Configuration menu, and then click Authentication Provider Settings.
- Click Enable OpenID Configuration. After you have completed and saved the OpenID configuration, this switch no longer appears on this page.
- Enter information for the following:
- Provider URL: Domain for the authentication. Currently supports Microsoft, Okta, Google, and Ping Identity.
- Client ID: The client ID.
- Client Secret: Secret key.
- Check the box. We recommend reviewing the settings you configured. You can potentially lock yourself out of the system if the settings are incorrect. The Save Changes button is only available after you check the box.
- Click Save Changes.
If you log on before the timer expires, the newly added authentication provider settings are retained.
EPM OpenID Connect workflow for new customers
Here is the workflow to get up and running with EPM using OpenID Connect authentication.
- You will receive an email from BeyondTrust after the request is processed.
- In the email, click the link to open the BeyondTrust OpenID Setup page.
- Enter the OpenID Connect information: domain, client ID, and client secret. Click Save Setup. The OpenID credentials are saved.
- The Endpoint Privilege Management login page opens. Click Log In.
- EPM opens to the Home page.
Add EPM to OpenID Connect provider
EPM supports Microsoft Entra ID, Okta OpenID, Google Identity, and Ping Identity Connect providers. The following sections provide a high-level overview on adding the EPM instance to your respective authentication provider. For complete instructions, refer to the provider's documentation.
The migration to OIDC will work when the email address sent from Okta or Entra ID matches for existing users. If email addresses are different or the domain name is not on the list of allowed domains in EPM, then the authentications will fail.
Add EPM instance to Google Identity
For step-by-step instructions on configuring Google Identity as your OpenID Connect provider, visit OpenID Connect.
After that configuration is complete, go to Configure an authentication provider.