Active Directory settings
Configure Active Directory (AD) connectors to discover AD groups in your estate. The Policy Editor queries the Active Directory to populate the group information when adding account filters or designated users.
There are two connector types:
- Microsoft Entra ID: Searches for Entra ID groups.
- Local AD: Searches for groups in the local Active Directory environment.
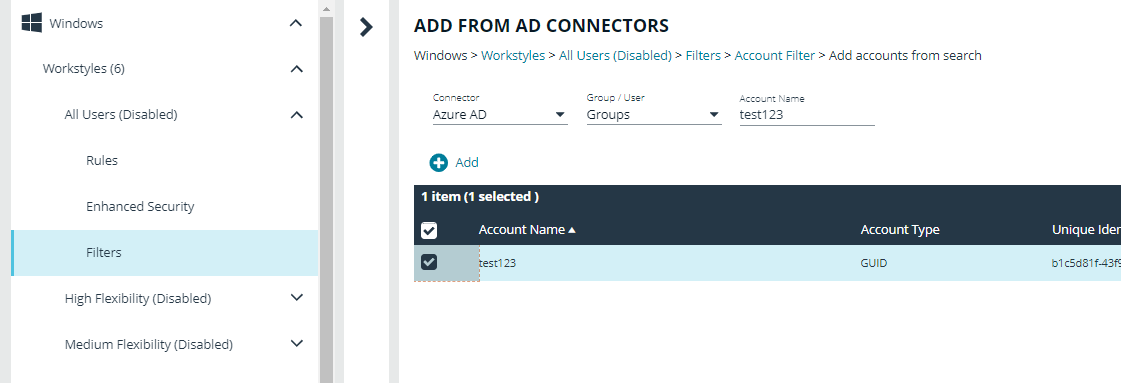
After the connectors are set up, the Policy Editor can discover and read information from the Active Directory source. The screen capture shows an example when adding an account filter for a workstyle.
A standard user requires delegated access to this page. For more information, see About user roles and resources.