Manage Endpoint Privilege Management for Networks Policies
Endpoint Privilege Management for Networks policy is managed from the Policy Management > Server Details > Endpoint Privilege Management for Networks section. From here, you can add, delete, or clone a policy, as well as configure the settings for Endpoint Privilege Management for Networks.
Endpoint Privilege Management for Networks management is divided into sub-sections, which allow you to edit settings according to your specific parameters.
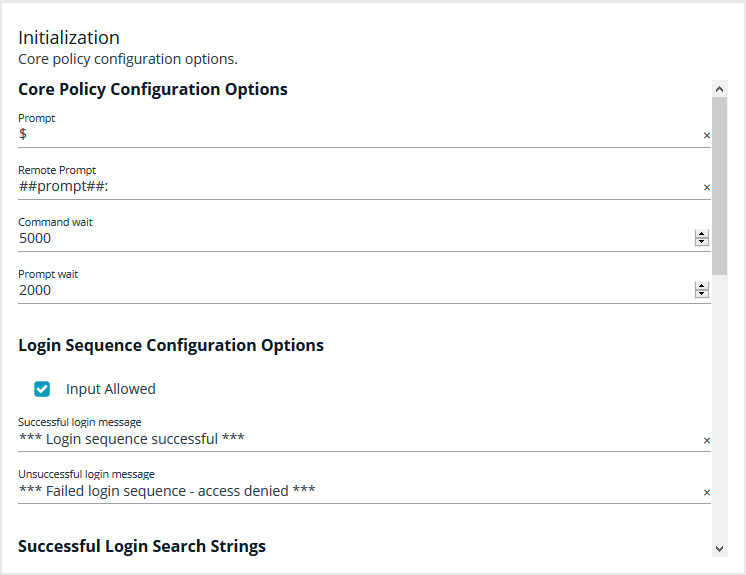
Initialization
Configure core policy options, including sections for login sequence and policy-wide defaults.
The following configuration options are available:
- Core Policy Configuration Options: Enter a name for the policy, a symbol for the prompt you want to display, and a remote prompt. The remote prompt is what the system waits to see before letting the user type. Enter the time (in seconds) for the command and prompt wait.
- Login Sequence Configuration Options: Select whether input is allowed or not, and then type in a message to display when the login sequence is successful or unsuccessful.
- Successful Login Search Strings: This is what the device outputs when a login is successful. For example, the search string output can be set to last login. In this scenario, when you log in to your machine, the last login message is displayed to indicate you have successfully authenticated.
- Password Matching Search Strings: These are values to look for, should the user be prompted to enter a password. The policy will read the output from the remote system, such as a router, and if the output matches one of these configured values, this means the system is asking for authentication.
- Prerun Commands: These are run before the policy is executed. For example, if the policy sets the value of prompt to Prompt, then you know you are ready for input when you receive the prompt message.
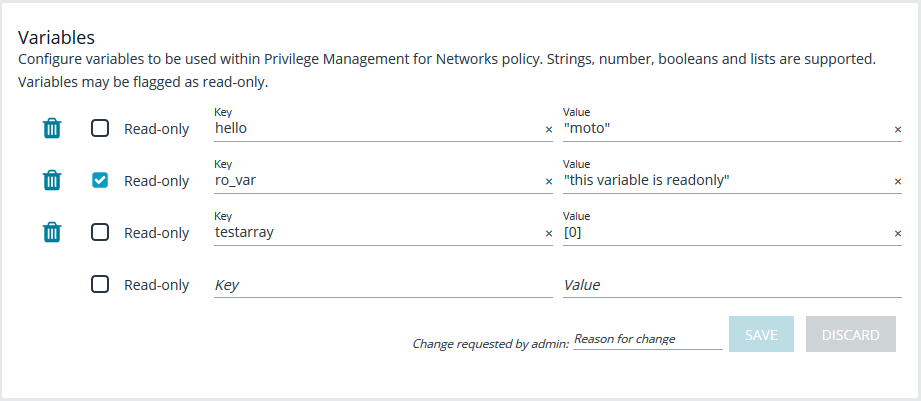
Variables
Variables must be defined within a policy. This section is used to configure variables, set defaults, and mark variables as read-only. Strings, numbers, booleans, and lists are supported. Variables may be flagged as read-only. When finished, click Save.
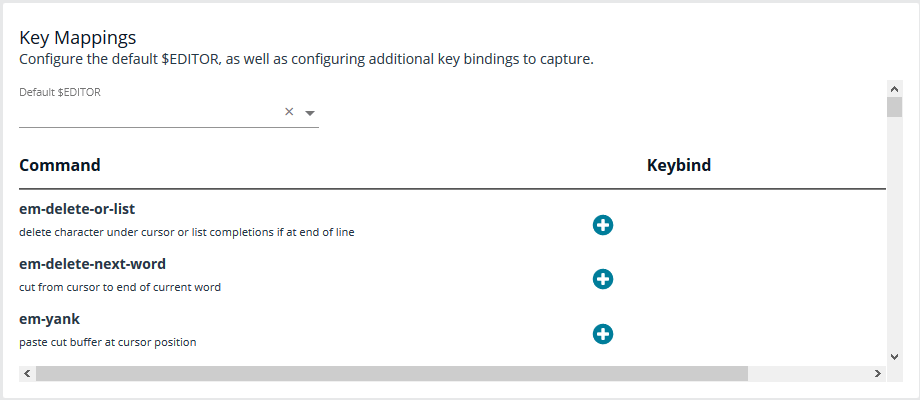
Key Mappings
This section enables configuration of keyboard input. To set a key mapping, use the Default $Editor dropdown to choose the policy’s default editor type (vi or emacs), and then click the + option next to the keyboard action. A message displays, indicating the system is waiting for input. While BIUL is listening for keystrokes, input the key or key combination you want to set. Key bindings can be cleared by selecting the X next to the binding. When finished, click Save.
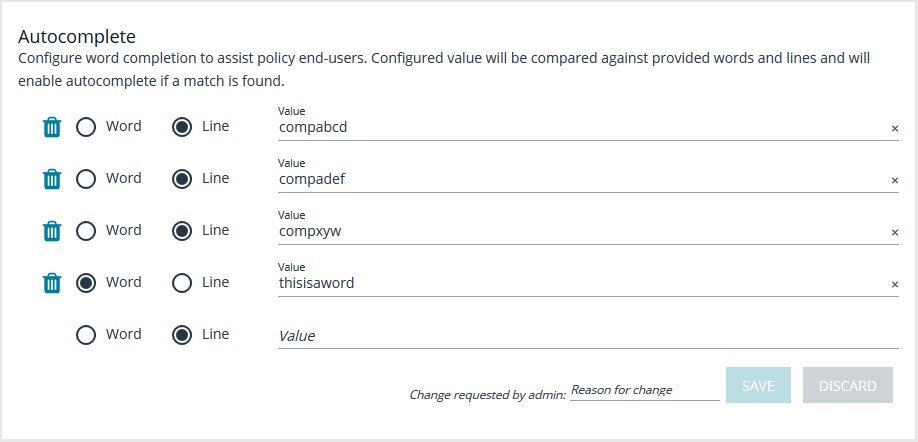
Autocomplete
In this section, you can configure word completion to assist policy end users. The configured value is compared against provided words and lines and enables autocomplete if a match is found. The user can then use the autocomplete key (Tab) to accept the matching value. When finished, click Save.
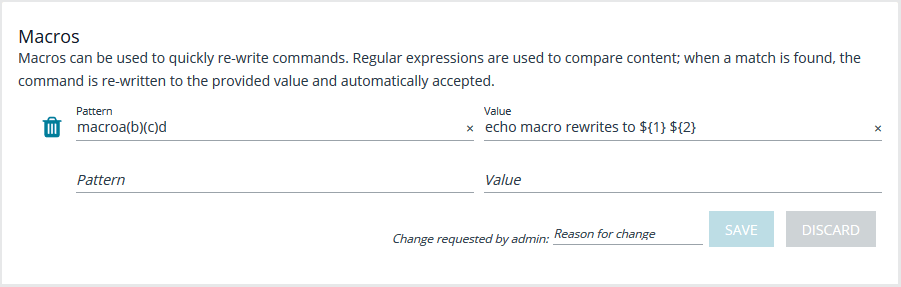
Macros
Macros can be used to quickly rewrite commands. Regular expressions are used to compare content. When a match is found, the command is re-written to the provided value and is automatically accepted. When finished, click Save.
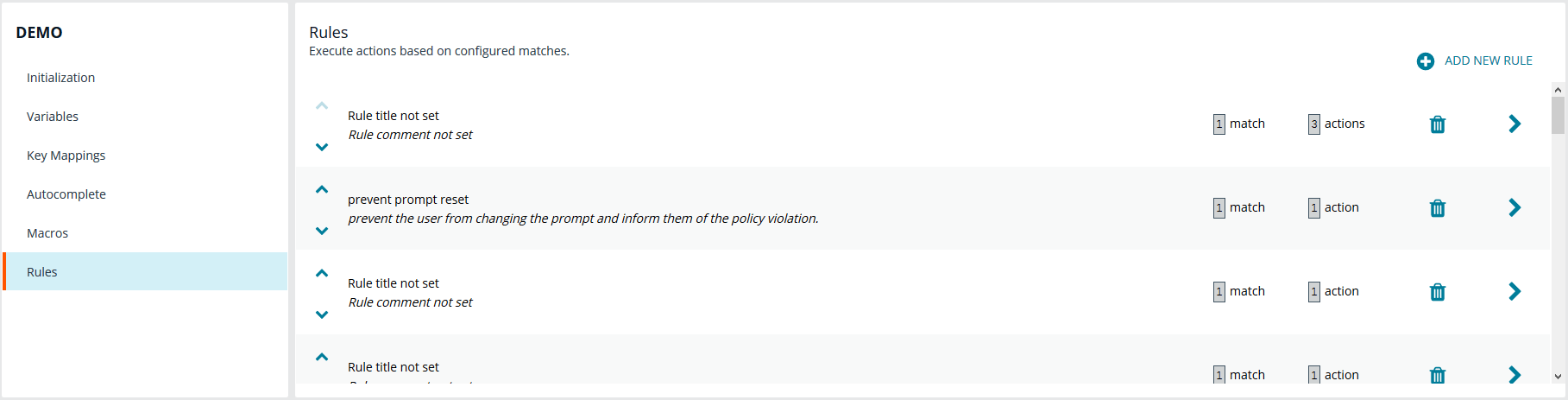
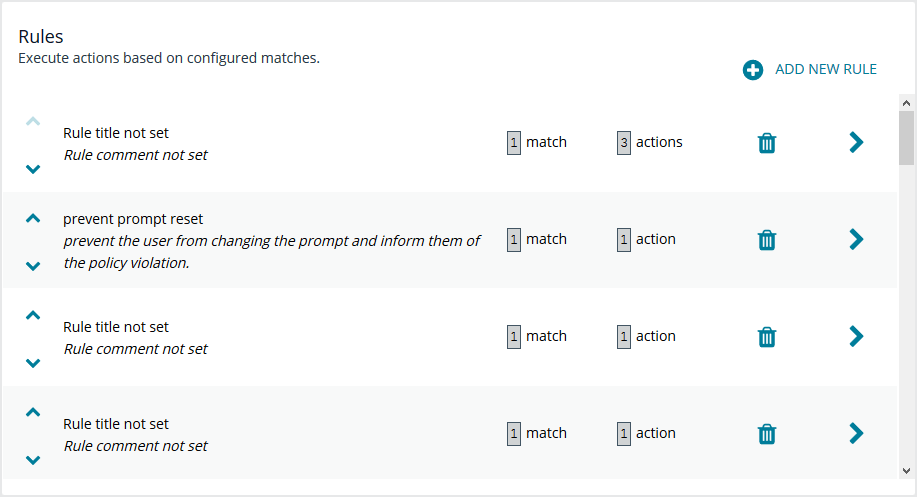
Rules
The core of Endpoint Privilege Management for Networks is handled in this section. The Rules summary page allows you to create a new Rule or reorder them.
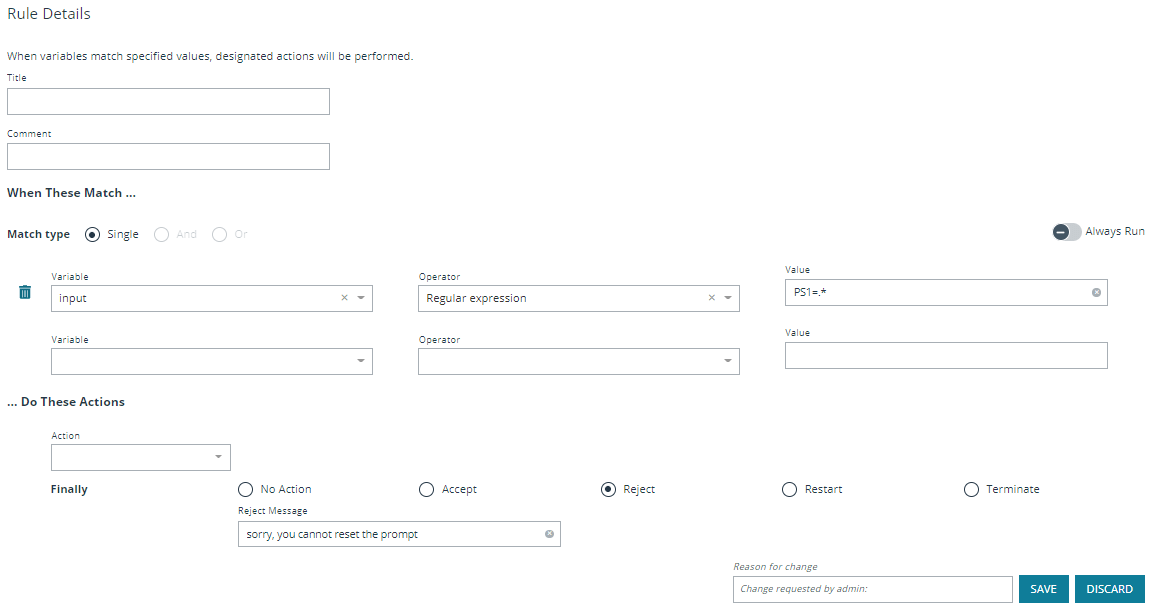
To add a new item, click Add New Rule. This brings up the Rule Details page. This is the same page that displays when you click on the chevron icon to edit an existing rule.
Within the editor one or more matches can be created where a match is a check of some sort. For example, variable equality or a regular expression result. More than one match can be joined together using either a logical and or logical or. If a match is found, the associated actions that are invoked can be configured using editor. Matches can have zero to many actions.
Add a Policy
To add a policy:
- On the Endpoint Privilege Management for Networks page, click Create New Policy.
- Enter the Policy name.
- In the Change requested by [loggedInUserName] field, enter a reason for the assignment or change.
- Click Create.
Delete a Policy
On the Endpoint Privilege Management for Networks page, click the trash bin icon on the policy you want to remove. Click OK to confirm.
Clone a Policy
You may want to clone a policy in order to make a backup, or use it as a template to create a new one. On the Endpoint Privilege Management for Networks page, click the clone icon on an existing policy, enter a unique Policy name, and click Clone.
Each policy requires a unique name. In order to clone a policy, you must give it a new name; otherwise, the Clone button does not activate.
Configure Endpoint Privilege Management for Networks
To configure Endpoint Privilege Management for Networks, the path to a valid Password Safe runfile script and certificate must be provided, as well as a list of Password Safe servers that can provide credentials.
To configure Endpoint Privilege Management for Networks:
- Go to the Policy Management page.
- In the Hostname list, select a server entry, and then at the far right, click the vertical ellipsis menu icon and select Server Details.
- On the Server Details page, select Settings & Configuration > Endpoint Privilege Management for Networks Configuration.
- Configure the following options:
- Password Safe Runfile
- Certificate path
- Password Safe Servers
- In the Change requested by [loggedInUserName] field, enter a reason for the assignment or change.
- Click Save.