Configure SAML 2.0 for Password Safe using Entra ID App
Entra ID, part of Microsoft Entra, is an enterprise identity service that provides single sign-on, multifactor authentication, and conditional access to guard against a wide range of cybersecurity attacks.
A BeyondTrust app, available in Entra ID App Gallery, provides Single Sign-On and provisioning via SAML. This app supports Remote Support and public portals, Privileged Remote Access, Password Safe, and Password Safe Cloud.
Install and Configure
Follow the steps below to install and configure this app.
- Locate the BeyondTrust SAML app in Microsoft Entra ID Gallery.
- Change the name to your preferred descriptive name, for example, BeyondTrust SAML – Password Safe. Some screenshots below use BeyondTrust Privileged Remote Access for examples, however the process is the same for Password Safe.
While a single instance of the app can service multiple BeyondTrust products simultaneously, we recommend creating a separate app instance for Password Safe, if you are using that product.
- Click Create.
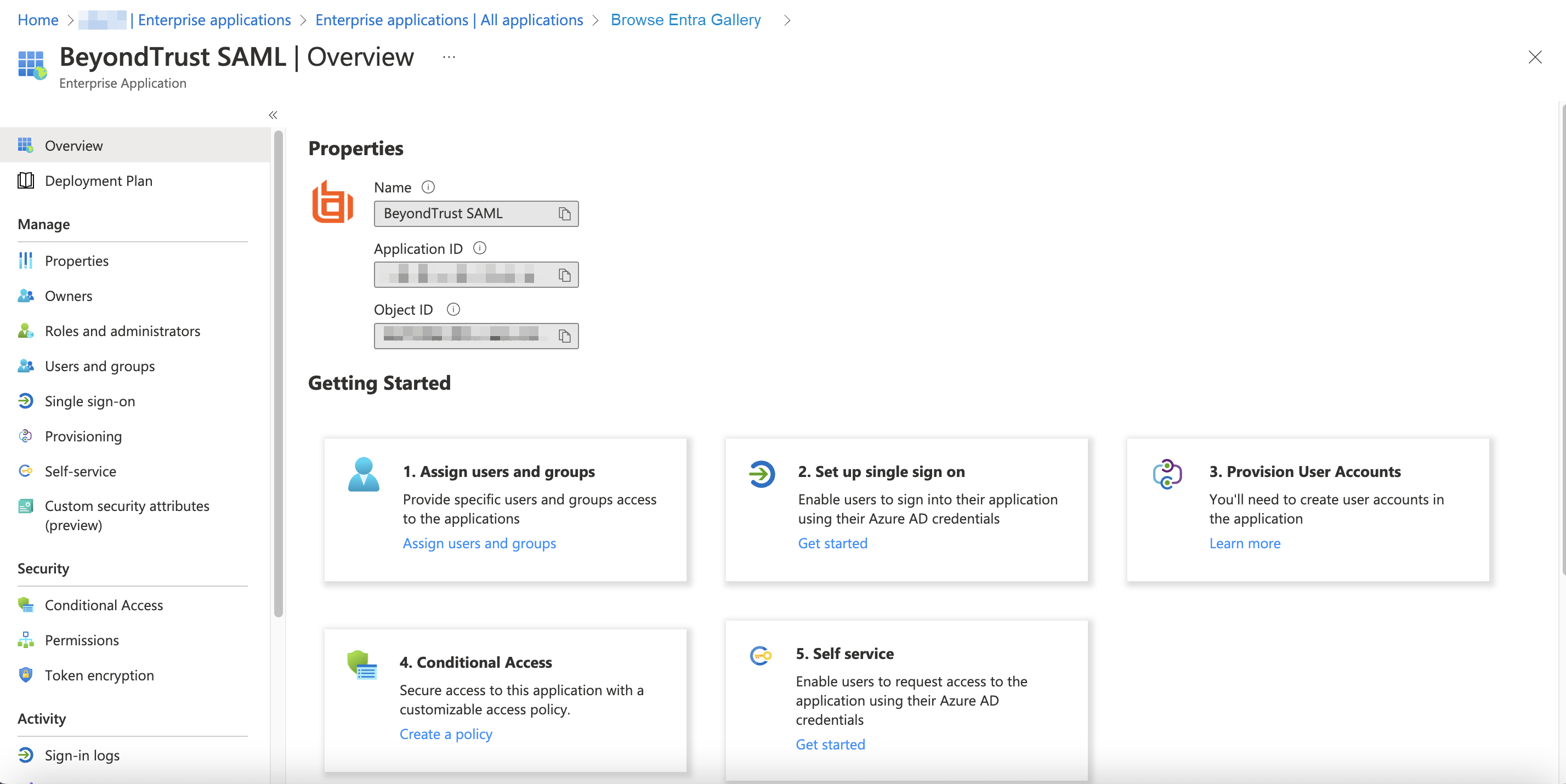
- Information about the BeyondTrust SAML app displays when creation is completed.
- Click Set up single sign on under Getting Started.
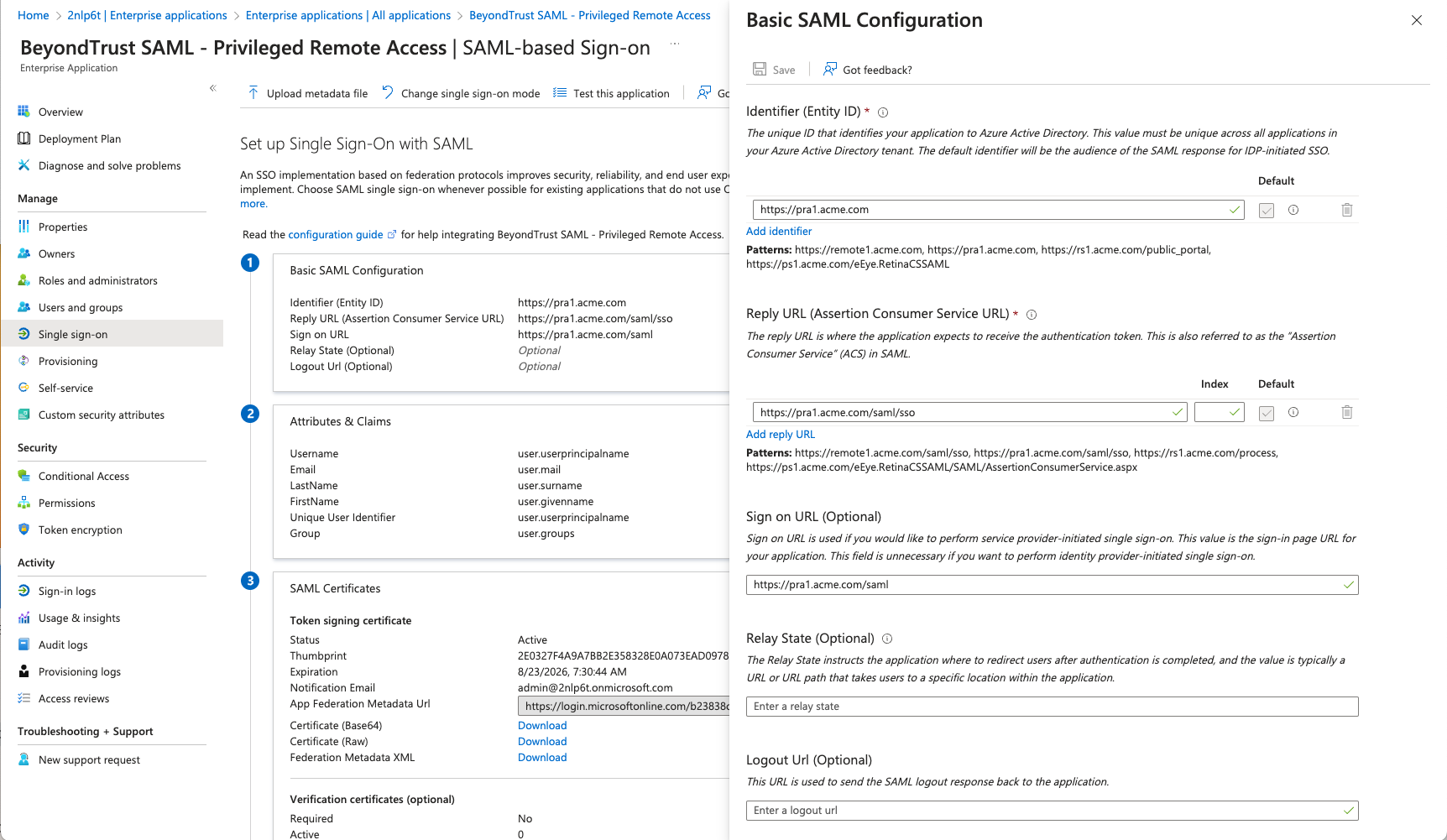
- Configure Basic SAML Configuration to match your Password Safe instance. The Entity IDs are specific to the instances for each product.
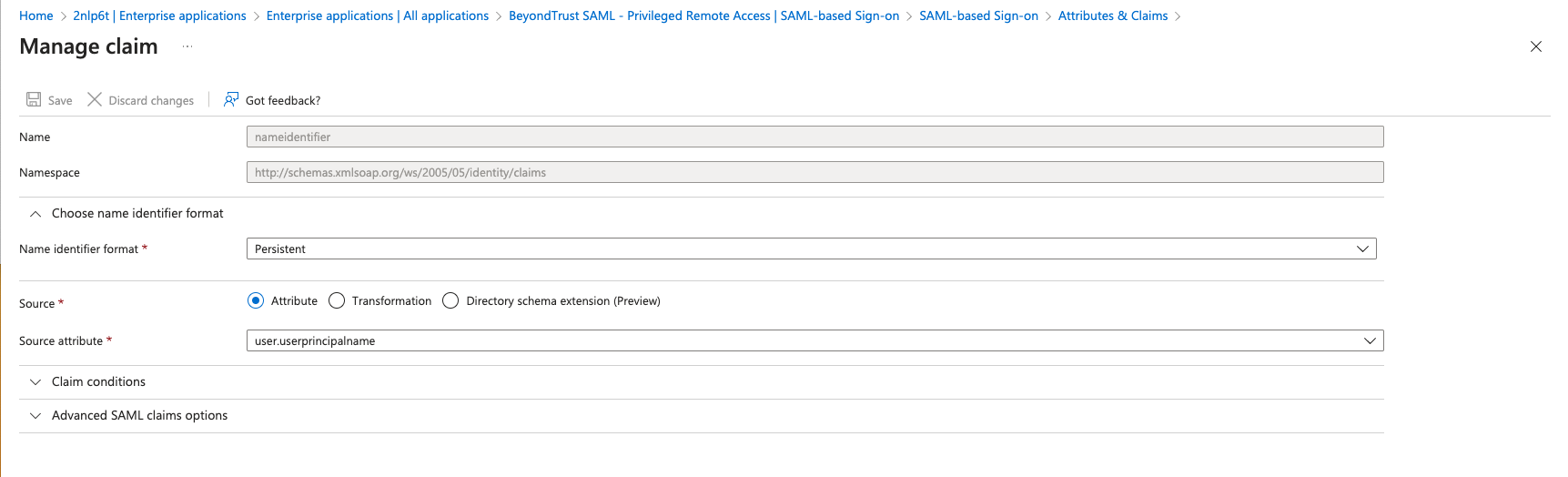
- Change the Unique Identifier (Name ID) to the Persistent format.
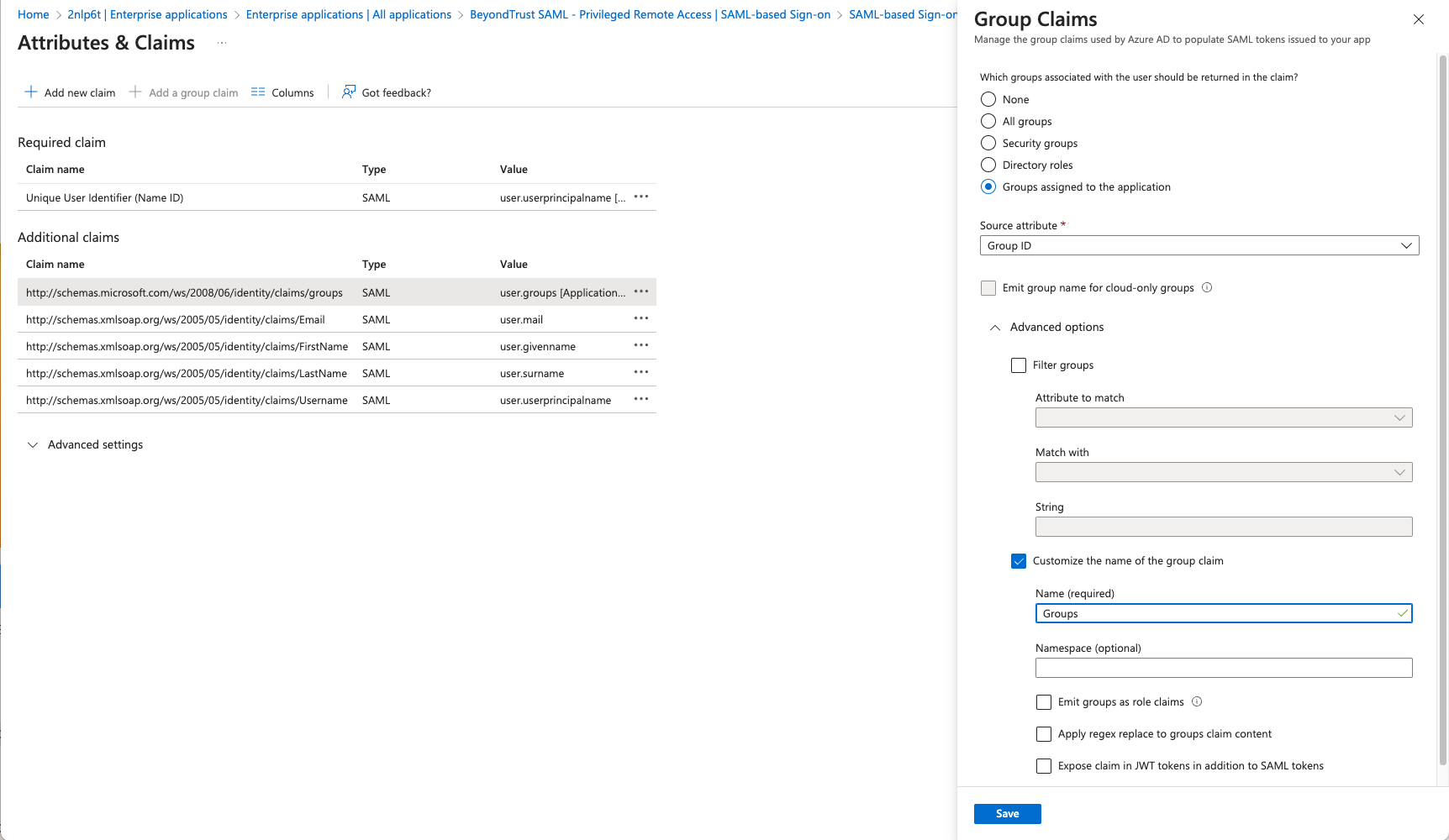
- Configure Attributes & Claims sources and values as shown in the table below, then add a group claim as show in the image below:
| Source | Value |
|---|---|
| Username | user.principalname |
| FirstName | user.givenname |
| LastName | user.surname |
| user.email | |
| Group Claim | Group ID |
The group claim must be configured to use only groups assigned to the application, to prevent errors that may occur if a user belongs to more than 150 AD groups. For more information, please see Configure group claims for applications by using Entra ID.
- Click Edit on the SAML certificates section.
- For Signing Option, select Sign SAML response and assertion.
- Download the Federation Metadata XML.