Integrate Blue Prism with Password Safe
Blue Prism is a global leader in intelligent enterprise automation, improving how employees work. Blue Prism helps organizations enhance operational efficiency by enabling users to automate tasks.
This guide covers how to use Password Safe as the central repository for just-in-time access to credentials in Blue Prism processes for automation.
Password Safe provides a secure, flexible, and scalable credential provider for Blue Prism. With the additional support for Secrets Safe, organizations can provide Blue Prism users with the flexibility they need, while aligning with best practices when it comes to the protection and governance of privileged accounts.
For more information on obtaining the integration, please see Blue Prism Digital Exchange.
Create and Configure the Blue Prism Service Account
To configure a Blue Prism service account in Password Safe:
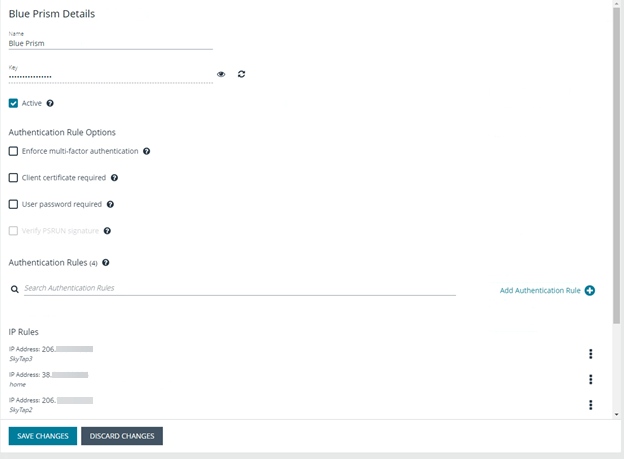
- Create an API registration for Blue Prism.
- Add IP rules to give the Blue Prism service account access to the Password Safe API interface.
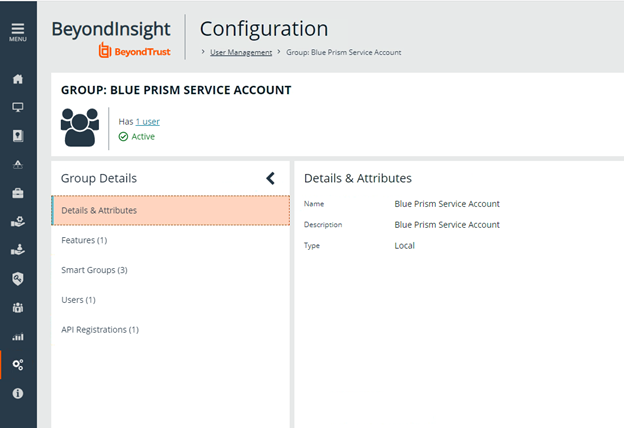
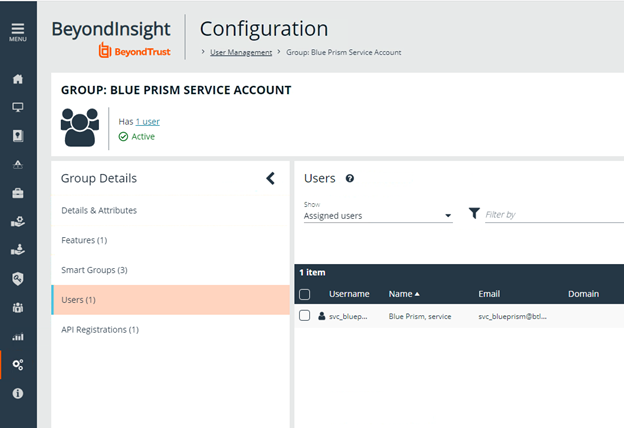
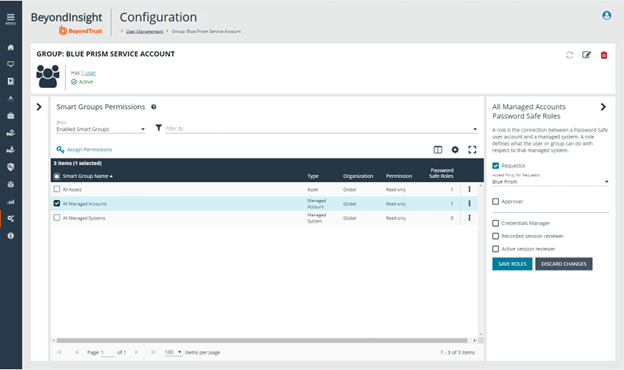
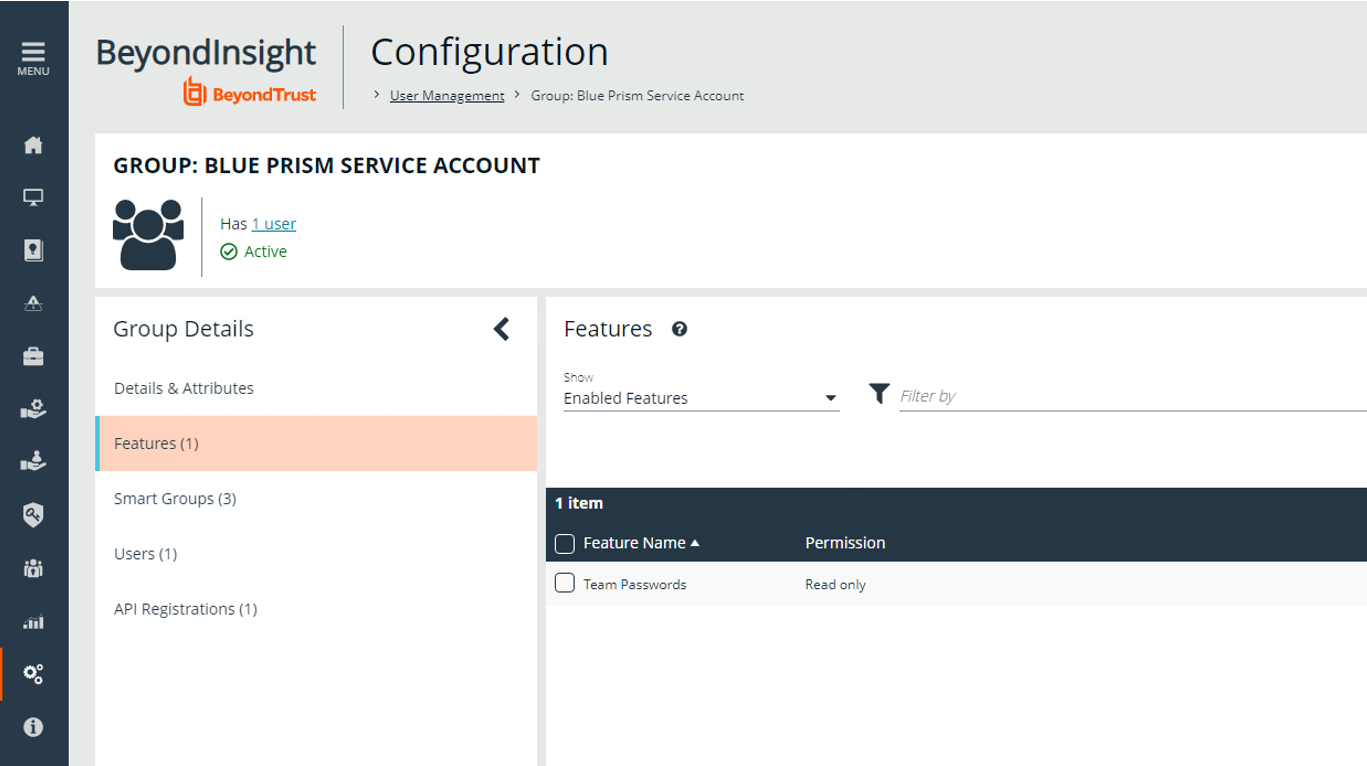
- Under Configuration > User Management, create a group for the service account, and assign the API registration to the group.
- Create a user to add to the group. For example, svc_blueprism.
Permissions are always assigned to a group in Password Safe.
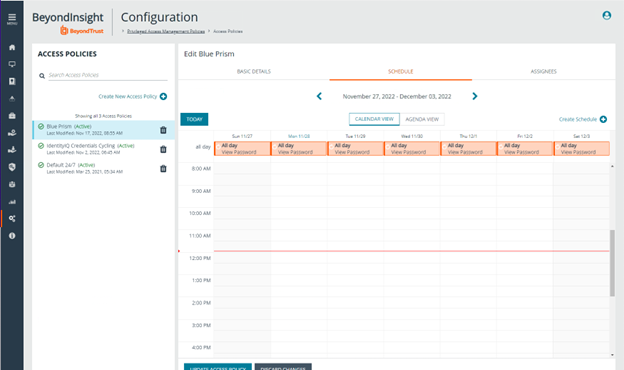
- To create an access policy, go to Configuration > Privileged Access Management Policies > Access Policies.
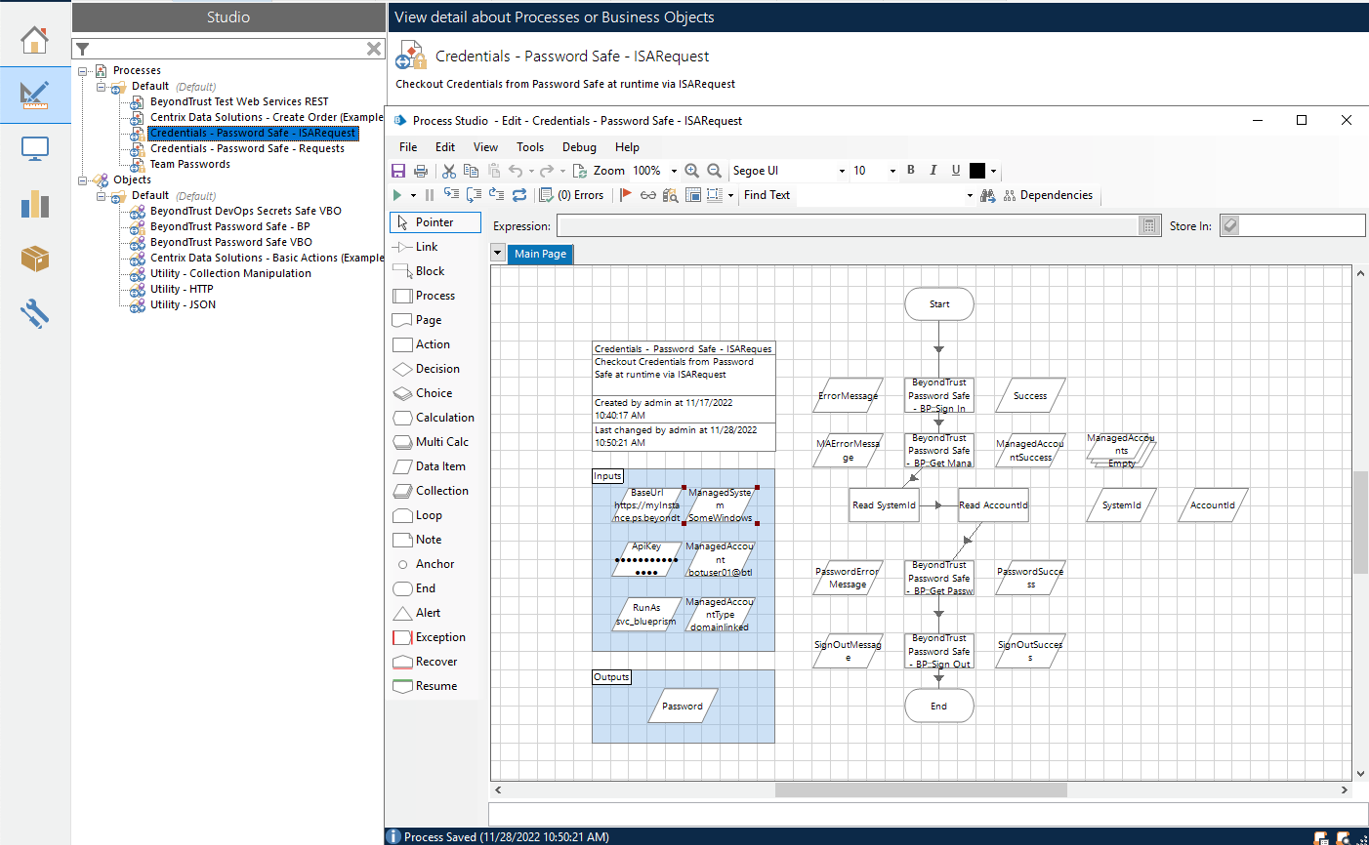
Password Safe User Requests
Configure the group with the Requestor role.
- Add one or more managed account Smart Groups to the newly created group.
- Add the Password Safe Requestor role and the access policy for Blue Prism.
- Populate the Blue Prism inputs with the following:
- Base URL
- API key
- Run As service account name
- Managed System and Managed Account names, and Managed Account type.
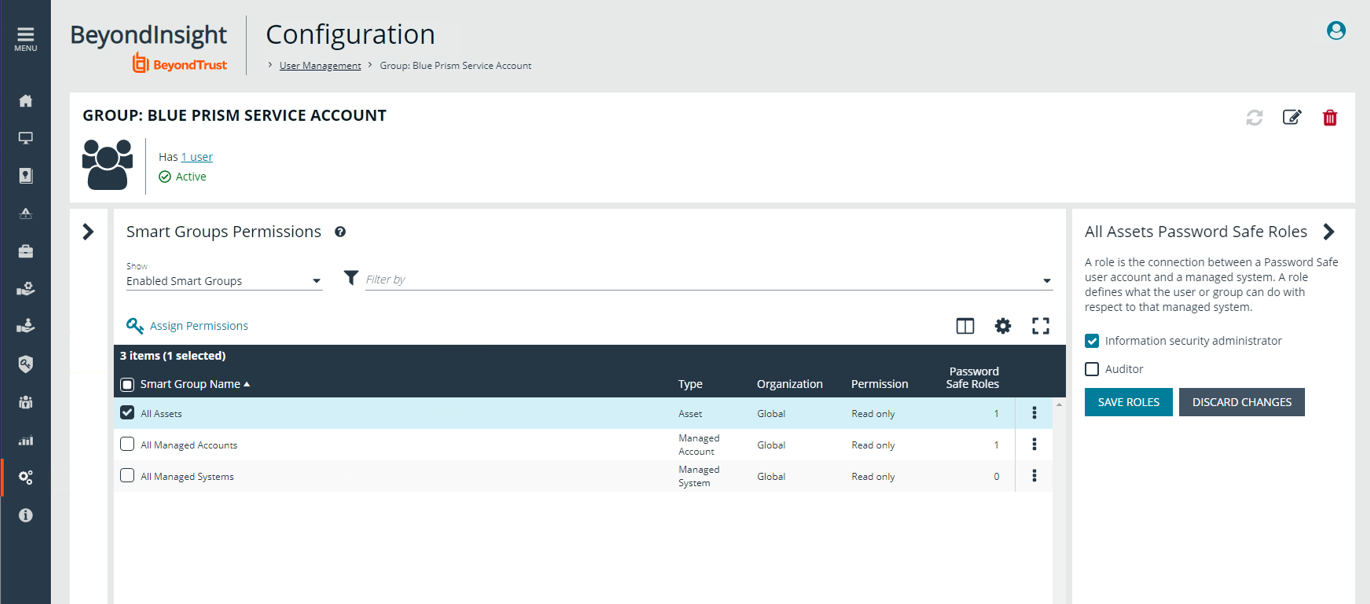
Password Safe ISA (Info Sec Admin) Requests
Configure the Blue Prism group with the Password Safe ISA role.
- For the group, add the Information security administrator role for one or more assets Smart Groups.
- In Blue Prism, populate the following:
- Base URL
- API key
- Run As service account name
- Managed System
- Managed Account name
- Managed Account type
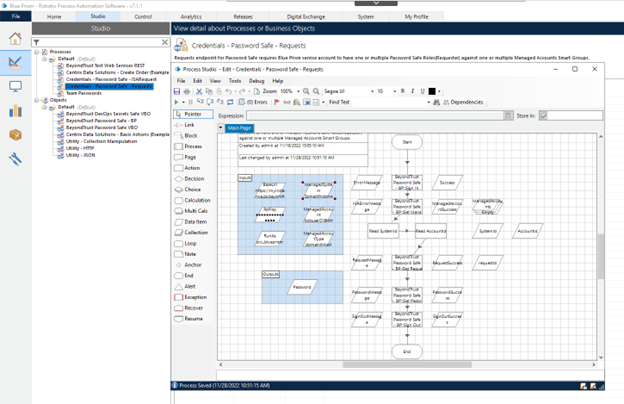
Password Safe Secrets Safe Requests
Configure the Blue Prism group with the Secrets Safe (formerly, Team Passwords) role.
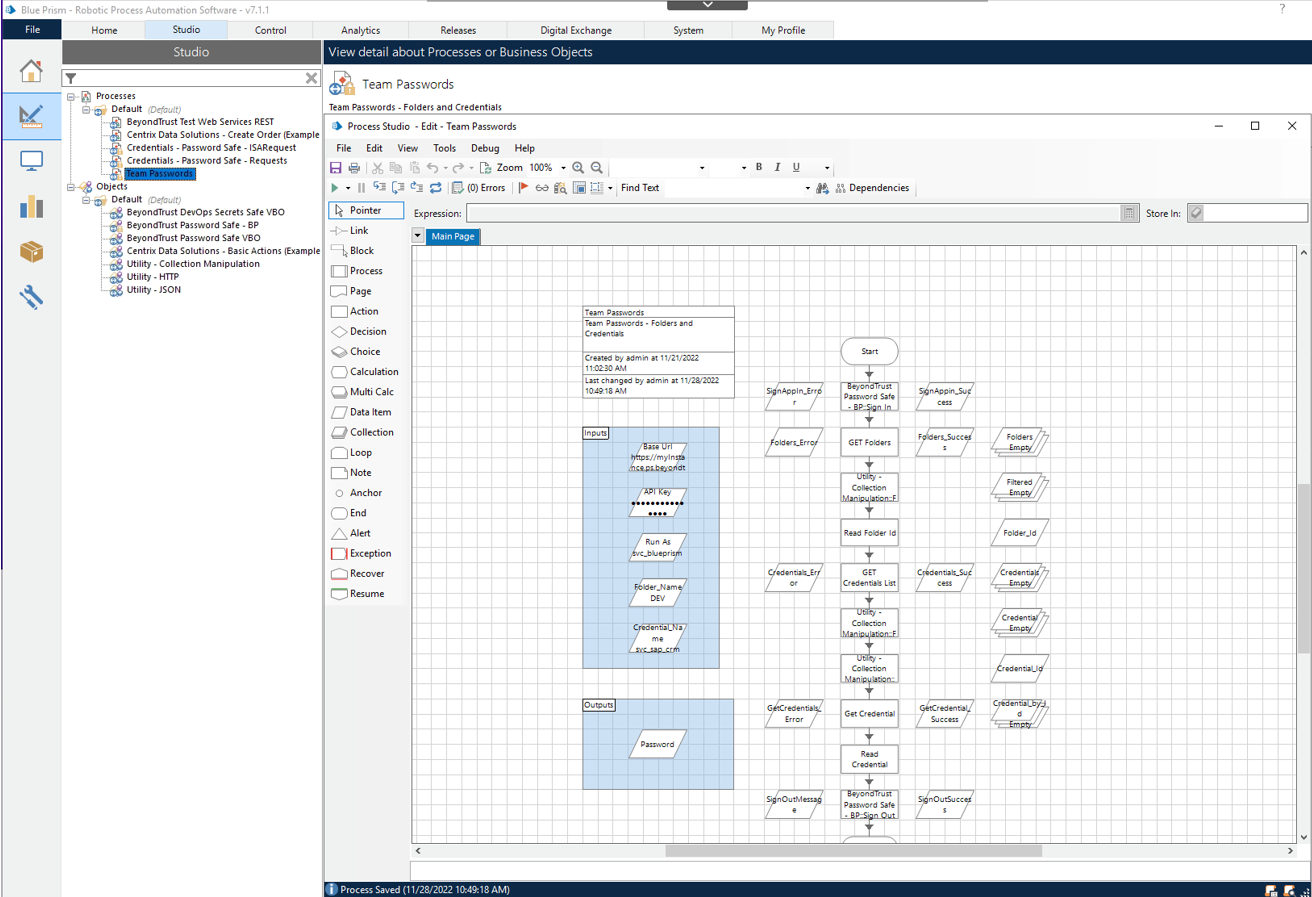
When the Password Safe and Blue Prism integration was initially set up, the feature was called Team Passwords. The feature name has since changed to Secrets Safe. The screen captures in this guide show Team Passwords.
- For the group, add the feature called Secrets Safe, with Read only permission.
-
Using the process example (shown in the screen capture), provide inputs for the following:
- Base URL
- API key
- Run As service account name
- Folder name
- Credential name
For more information about configuring Password Safe, please see: