Configure BeyondInsight Clarity Analytics
BeyondInsight Clarity is a behavior analytics tool that examines and classifies events and activities to identify outliers or anomalies. An outlier is an observation which deviates so much from the other observations that it arouses suspicion. Clarity ranks activities and classifies assets according to their deviation from normal activity. The normal activity or baseline is formed from:
- History of past activities
- Risk attributes of an observed activity
Each activity or event has several key characteristics. When an observed characteristic goes beyond normal, an alert is issued. More flagged alerts indicates higher level of abnormality and threat level. The numeric threat level is the sum of all flagged alerts. In addition, all assets are grouped into clusters by similarity, taking into account all available information including vulnerabilities, attacks, installed applications, services, open ports, running applications, etc.
As a result, the behavior analytics:
- Assigns a threat level to each event from BeyondTrust Discovery Scanner, Endpoint Privilege Management, Privilege Management for Unix & Linux, and Password Safe.
- Assigns cluster ID to all assets.
You can use Clarity to analyze data from the following sources:
- Endpoint Privilege Management
- Privilege Management for Unix & Linux
- BeyondTrust Discovery Scanner
- Password Safe
- Third-party imports
To work with BeyondInsight Clarity, you must configure settings in the BeyondInsight management console.
Configure the Analytics Calculation
- In the console, click Configuration.
- Under Analytics & Reporting, click Clarity Analytics.
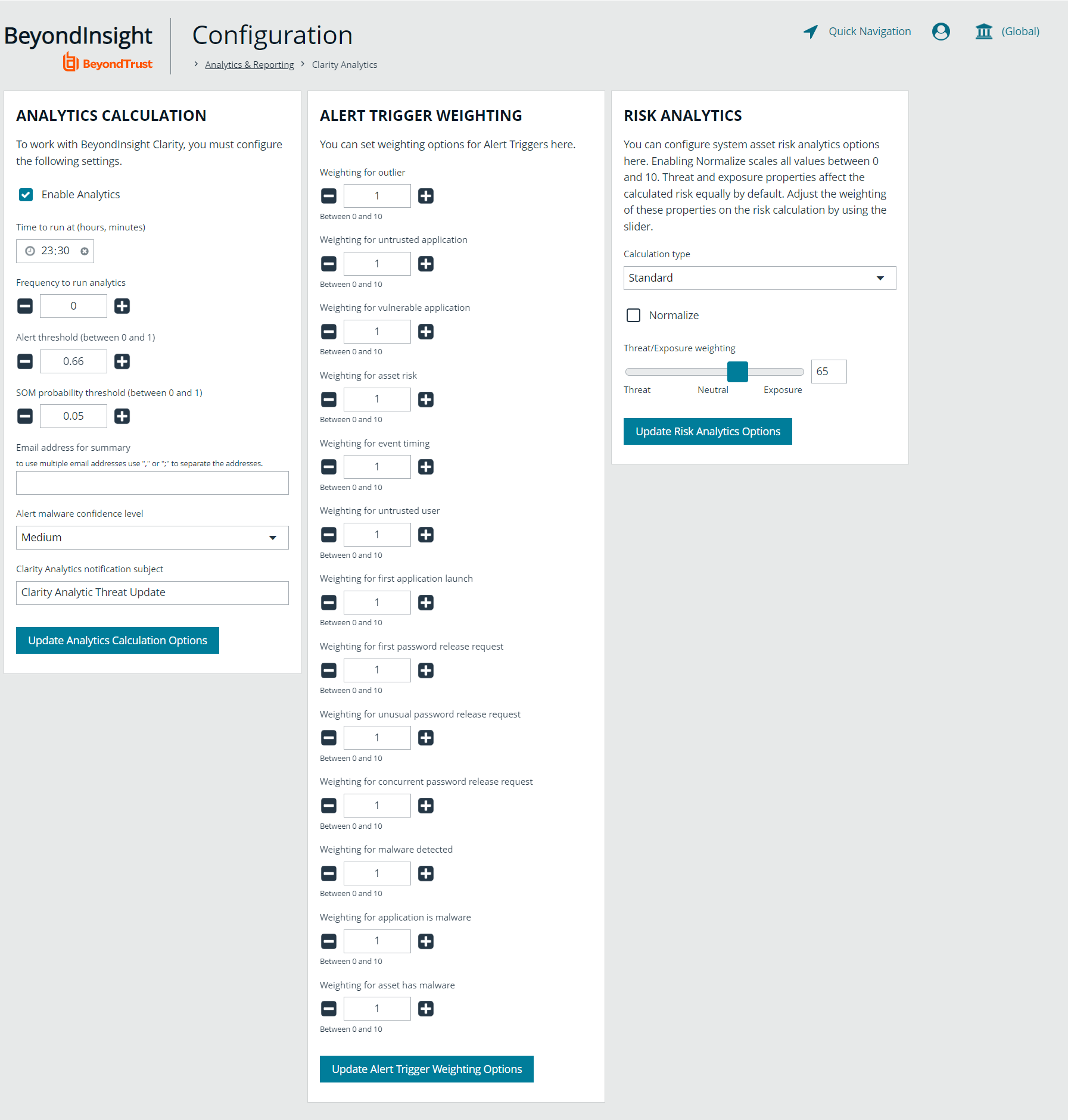
- From the Analytics Calculation section, you can:
- Enable and disable analytics.
- Select the hours and minutes for Time to run at.
- Select the frequency for running analysis.
- Set the Alert Threshold for flagging explicit alerts. The higher the value, the higher the sensitivity and the fewer flagged alerts. The range is from 0 to 1. The default value is 0.65.
- Set the Som Probablity Threshold for flagging pattern alerts. The lower the value, the higher the sensitivity and the fewer flagged alerts. The range is from 0 to 1. The default value is 0.05.
- Enter an email address to send notifications to.
- Set the notification subject.
- Click Update Analytics Calculation Options.
Set Alert Trigger Weighing
From the Alert Trigger Weighing section, you can configure Clarity to prioritize or weigh specific alerts. If an alert with a higher weight is triggered, the alert appears more prominently in the Clarity analysis. This allows you to quickly see and react to critical alerts.
To configure a weight for an alert, click the minus and plus buttons to modify its numeric value, ranging from 0 to 10. When you are satisfied with your selections, click Update Alert Triggering Weighing Options to finalize.
Configure Risk Analytics
Using the risk analytics values, you can focus the results data on the highest risk assets.
Enabling Normalize scales all values between 0 and 10. When you choose to normalize the data, the asset at the highest risk is assigned the highest rating. All other assets are rated and organized below the highest risk asset. Normalizing the results provides a way to distribute the assets in a more meaningful way to analyze the data.
Threat and exposure properties affect the calculated risk equally by default. Adjust the weighting of these properties on the risk calculation by using the slider. You can change the results to emphasize risk levels based on exposures or threats. For example, if you move the slider to Exposure, asset exposure risk factors are given greater weighting in the final risk calculation and increase an asset's risk score.
Clarity Reports
The following reports are available to run against Clarity data:
- Event Review - Endpoint Privilege Management: Breakdown of alert triggers for events by threat level. Includes relevant event details, and is ordered by threat level from largest to smallest.
- Event Review - Password Safe Release Events: Breakdown of alert triggers for Password Safe release events by threat level.
- Event Review - Privilege Management for Unix & Linux Breakdown of alert triggers for Privilege Management for Unix & Linux events by threat level. Includes relevant event details, and is ordered by threat level from largest to smallest.
- Top 10 Assets by Total Threat Level: Displays top 10 assets based on overall threat level.
- Top 10 Users by Threat Level: Displays top 10 users based on overall threat level.