Configure an HSM Using the BeyondInsight Configuration Tool
BeyondInsight communicates with HSM appliances using a commonly supported API called PKCS#11. Most HSM appliances include a PKCS#11 driver with their client software installation. This allows applications to leverage the device without requiring specific knowledge of the make, model, or configuration of the appliance.
HSM appliances vary in a number of ways depending on the model, and each appliance comes with its own documentation supplied by the vendor. Each HSM appliance has its own set of steps and requirements for configuration and client software installation, such as ports used, network topology and architecture, client authentication protocol, and firewall rules. Prior to configuring the HSM within BeyondInsight, these processes must be performed according to the documentation provided with the appliance, using the tools provided as part of the HSM client software suite.
The BeyondInsight integration with the HSM appliance treats the appliance as an external API that only requires credentials. Advanced configurations and features, such as high-availability implementations, are typically transparent in BeyondInsight. For example, the client software might allow a group of multiple HSM appliances to be presented as a single token in a single slot. In this case, BeyondInsight accesses the group the same way it accesses a single appliance. Configuring the group and synchronizing key data is outside the scope of the BeyondInsight software and must be performed according to the guidelines for the specific hardware. If necessary, seek assistance from the HSM vendor.
Prerequisites
- A BeyondInsight server, typically a U-Series Appliance. For legacy installations, this may be a Windows server that hosts BeyondInsight.
- A supported HSM, configured and accessible to the BeyondInsight instance.
- The path to both the 32-bit and 64-bit PKCS#11 drivers (typically included when the client software is installed and listed in the documentation provided with the U-Series Appliance). Both driver locations are required during HSM configuration.
- The name of the token to which BeyondInsight should connect (specified as part of the U-Series Appliance configuration process).
- The PIN or password for an HSM user who can create and use keys (specified as part of the U-Series Appliance configuration process).
- There must be no other credentials configured in the database when the HSM configuration procedure is executed.
Supported Configurations
- Password Safe v6.2 and later releases
- An HSM that provides a PKCS#11 driver
Add an HSM Credential to BeyondInsight
- Log in to the BeyondInsight instance that is configured to access the HSM.
- Open the BeyondInsight Configuration tool:
Start > Apps > eEye Digital Security > BeyondInsight Configuration.
- If a User Account Control dialog box appears, click Yes to continue.
- Click Configure HSM Credentials.
- Select Edit > Add New HSM Credential.
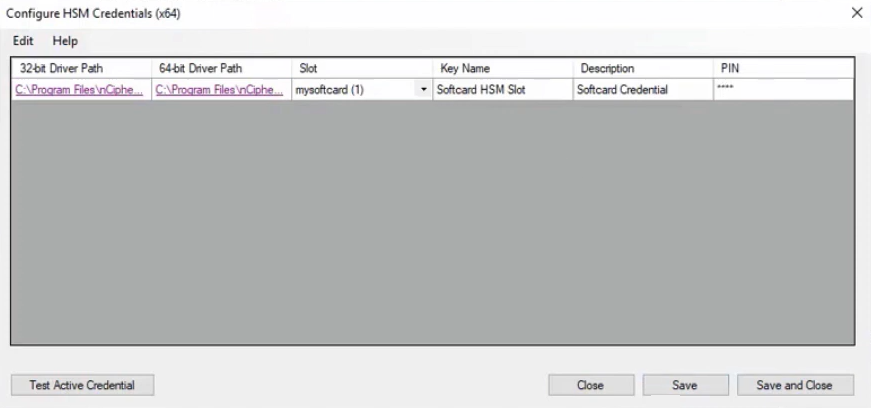
- Enter HSM details as defined below, and then click Save.
- 32-bit Driver Path: Select the 32-bit PKCS#11 driver that was supplied with your HSM client software. The location of the PKCS#11 driver is provided in the documentation that came with your HSM.
- 64-bit Driver Path: Select the 64-bit PKCS#11 driver that was supplied with your HSM client software. The location of the PKCS#11 driver is provided in the documentation that came with your HSM.
- Label/Slot: After a valid 32-bit driver is selected, this dropdown contains a list of the tokens presented by the driver in the format of label (slot number). The label is the name of the HSM token. Some U-Series Appliances might have a default name. Otherwise, it is a name set when you configured your HSM. The slot number is an index number starting at 0, indicating the token’s position within the list of tokens presented by the driver.
In addition to its index/position, a slot also has an ID number that might or might not match the index. Some vendors use the slot ID rather than the index when enumerating slots/tokens in their own software. For example, Gemalto’s Version 5.x software uses an ID that is 1 greater than the index; meaning that what their software calls slot 1 is actually slot 0, slot 2 is actually slot 1, etc.
- Key Name: HSM keys are identified labels. A unique name must be provided for each key in order to associate encrypted credentials with the key used to encrypt and decrypt them. Any key name may be used as long as it is unique.
- Description: Information about the key (for display purposes only).
- PIN: The PIN for the HSM user that was set up for use by BeyondInsight. The user must have permission to create and access keys on the HSM.