Assign Access Control Groups in AD Bridge
You can apply access control to UNIX and Linux agents (hosts) using the access control group setting that is available through AD Bridge Cell Settings. Using an access control group you can apply restrictive access control to the AD Bridge hosts and users that can access those hosts.
An access control group can be used to supplement existing Group Policy Allow Logon Rights settings and cumulative policy settings. The resultant set of groups will be a combination of the group membership for the AD Bridge host together with the Group Policy Allow Logon Rights settings and cumulative policy.
Configuring and using access control groups is a two-step process:
- Create an Active Directory group: this is a host access group. Create host access groups using a common attribute in the naming convention. For example, prefix all group names with ADB_.
- Add the groups to the Access Control Groups associated with the AD Bridge Cell.
Add the user accounts and the AD Bridge hosts to the group.
Members can be added directly to the group or through nested group membership. For a user to access an AD Bridge agent, the user and the agent must be a member of the same host access group (directly or through nested groups).
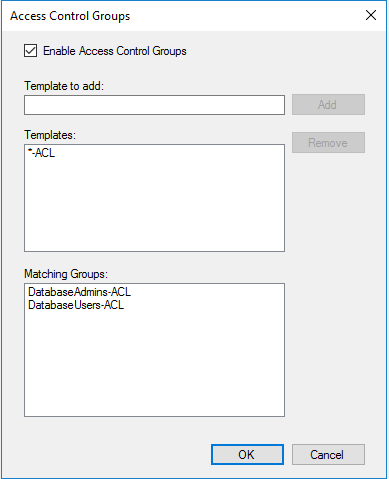
A template is a way to associate the groups with the cell. Host access templates identify the groups to use for the Access Control Group. The host access template can match on group names using wildcards. The name matching is applied to the “Group name (pre-Windows 2000) attribute”. This is the sAMAccountName attribute.
When an AD Bridge agent has no membership in any host access group, restrictions will not apply to that host. This can be confusing when removing a host from a host access group. If you want the default behavior to disable access to all AD Bridge hosts unless they are a member of a host access group then create a host access template for Domain Computers where only hosts are defined.
Apply Changes to the Access Control Group
The agent checks for changes to the Access Control Group during the lsass refresh. Each group the computer object belongs to that also matches the template name is added to the Host Access Groups. The lsass refresh interval is every 30 minutes. To apply the settings immediately, run the following command:
/opt/pbis/bin/lwsm refresh lsass
Confirm Configuration on the Agent
To confirm the templates are applying on an agent system use the pbis acl command. This returns the template that is configured and all the matching groups that have been applied.
Example Scenario
In a database environment, control access is required on a set of hosts running database applications that include the following:
- Group of database server hosts DatabaseServers: dbsrv1, dbsrv2, dbsrv3
- Group of database client hosts DatabaseClients: dbcli1, dbcli2, dbcli3
- Group of database administrator accounts: DatabaseAdmins: dbadm1, dbadm2, dbadm3
- Group of database application user accounts: DatabaseUsers: dbusr1, dbusr2, dbusr3
Database administrators can access all database hosts by creating a DatabaseAdmins-ACL group that includes the following groups as members: DatabaseServers, DatabaseClients and DatabaseAdmins.
Database users can access only database client hosts by creating a DatabaseUsers-ACL group that includes the following groups as members: DatabaseClients and DatabaseUsers.
On the Access Control Groups dialog box, enter the template name similar to the following: *-ACL. The wildcard matching adds all groups that contain -ACL to the list, as shown.