Create and Configure a SAML Security Provider for Representatives and Public Portals
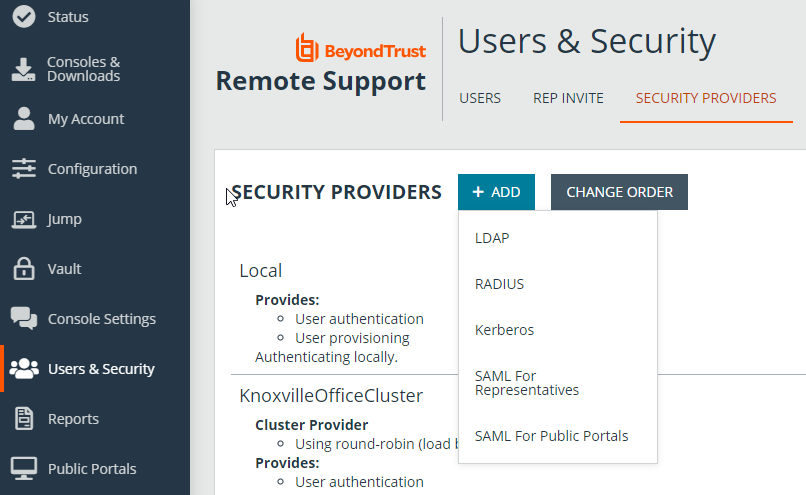
Go to /login > Users & Security > Security Providers.
From the + ADD dropdown, select the type of server you want to configure.
You can configure only one SAML provider for public portals. Multiple SAML providers can be configured for representatives, but a representative who is defined in more than one provider can only be mapped to the first provider.
SAML For Representatives Settings
Name
Enter a unique name to help identify your provider.
Enabled
If checked, your BeyondTrust Appliance B Series can search this security provider when a user attempts to log in to the representative console or /login. If unchecked, this provider will not be searched.
Associated Email Domains
This setting only applies if you have more than one active SAML provider and is ignored otherwise.
Add any email domains that should be associated with this SAML provider, one per line. When authenticating, users are asked to enter their email. The domain of their email is matched against this list, and they are redirected to the appropriate identity provider for authentication.
If multiple SAML providers are configured and the user's email does not match any of the associated domain on any provider, then they are not allowed to authenticate.
Identity Provider Settings
Metadata
The metadata file contains all the information needed for the initial setup of your SAML provider and must be downloaded from your identity provider. Save the XML file, and then click Upload Identity Provider Metadata to select and upload the selected file.
Entity ID
Unique identifier for the identity provider you are using.
Server Certificate
This certificate will be used to verify the signature of the assertion sent from the identity provider.
The fields for Entity ID, Single Sign-On Service URL, and Certificate are automatically populated from the identity provider's metadata file. If you cannot get a metadata file from your provider, this information can be entered manually. For metadata files with multiple identity providers, enter the Entity ID of the desired Identity Provider in the field below before uploading the metadata.
Single Sign-On Service URL
When you want to log in to BeyondTrust using SAML, this is the URL where you are automatically redirected so you can log in.
SSO URL Protocol Binding
Determines whether a user posts or is redirected to the sign on URL. This should be left defaulted to redirect unless otherwise required by the identity provider.
If request signing is enabled (under Service Provider settings), protocol binding is limited to redirect only.
Service Provider Settings
Download Service Provider Metadata
Download the BeyondTrust metadata, which must then be uploaded to your identity provider.
Entity ID
This is your BeyondTrust URL. It uniquely identifies the service provider.
Private Key
If necessary, you can decrypt messages sent by the identity provider, if they support and require encryption. Click Choose File to upload the private key necessary to decrypt the messages sent from the identity provider.
Signed AuthnRequest
Check to enable request signing. If enabled, SSO URL protocol binding is limited to redirect only. The SSO URL protocol binding field is updated automatically, if necessary.
A private key and signing certificate is required for request signing.
User Attribute Settings
SAML attributes are used to provision users within BeyondTrust. The default values match BeyondTrust-certified applications with various identity providers. If you are creating your own SAML connector, you may need to modify the attributes to match what is being sent by your identity provider. If your identity provider requires case-insensitivity for the NameID attribute, select Use case-insensitive comparison for NameIDs.
Authorization Settings
Lookup Groups Using This Provider
Enabling this feature allows faster provisioning by automatically looking up groups for this user, using Group Lookup Attribute Name and Delimiter. We recommend enabling this feature. If not used, SAML users must be manually assigned to group policies after their first successful authentication.
Group Lookup Attribute Name
Enter the name of the SAML attribute that contains the names of groups to which users should belong. If the attribute value contains multiple group names, then specify the Delimiter used to separate their names.
If left blank, SAML users must be manually assigned to group policies after their first successful authentication.
Group Lookup Delimiter
If the Delimiter is left blank, then the attribute value may contain multiple XML nodes with each one containing a different name.
Available Groups
This is an optional list of SAML groups always available to be manually assigned to group policies. If left blank, a given SAML group is made available only after the first successful authentication of a user member of such group. Please enter one group name per line.
Default Group Policy
Each user who authenticates against an external server must be a member of at least one group policy in order to authenticate to your B Series Appliance, logging into either the /login interface or the representative console. You can select a default group policy to apply to all users allowed to authenticate against the configured server.
If a default policy is defined, any allowed user who authenticates against this server might have access at the level of this default policy. Therefore, we recommend you set the default to a policy with minimum privileges to prevent users from gaining permissions you do not wish them to have.
If a user is in a default group policy and is then specifically added to another group policy, the settings for the specific policy always take precedence over the settings for the default, even if the specific policy is a lower priority than the default, and even if the default policy's settings are set to disallow override.
SAML For Public Portals Settings
Name
The name for your SAML provider is auto-generated and cannot be edited at this time.
Enabled
If checked, your BeyondTrust Appliance B Series can search this security provider when a user attempts to log in to the public portal. If unchecked, this provider is not searched.
Identity Provider Settings
Metadata
The metadata file contains all the information needed for the initial setup of your SAML provider and must be downloaded from your identity provider. Save the XML file, and then click Upload Identity Provider Metadata to select and upload the selected file.
Entity ID
Unique identifier for the identity provider you are using.
Server Certificate
This certificate will be used to verify the signature of the assertion sent from the identity provider.
The fields for Entity ID, Single Sign-On Service URL, and Certificate are automatically populated from the identity provider's metadata file. If you cannot get a metadata file from your provider, this information can be entered manually. For metadata files with multiple identity providers, enter the Entity ID of the desired Identity Provider in the field below before uploading the metadata.
Single Sign-On Service URL
When you want to log in to BeyondTrust using SAML, this is the URL where you are automatically redirected so you can log in.
SSO URL Protocol Binding
Determines whether a user posts or is redirected to the sign on URL. This should be left defaulted to redirect unless otherwise required by the identity provider.
If request signing is enabled (under Service Provider settings), protocol binding is limited to redirect only.
Service Provider Settings
Download Service Provider Metadata
Download the BeyondTrust metadata, which must then be uploaded to your identity provider.
Entity ID
This is your BeyondTrust URL. It uniquely identifies the service provider.
Private Key
If necessary, you can decrypt messages sent by the identity provider, if they support and require encryption. Click Choose File to upload the private key necessary to decrypt the messages sent from the identity provider.
Signed AuthnRequest
Check to enable request signing. If enabled, SSO URL protocol binding is limited to redirect only. The SSO URL protocol binding field is updated automatically, if necessary.
A private key and signing certificate is required for request signing.
User Attribute Settings
SAML attributes are used to provision users within BeyondTrust. The default values match BeyondTrust-certified applications with various identity providers. If you are creating your own SAML connector, you may need to modify the attributes to match what is being sent by your identity provider. The SAML attributes can also be associated with customer sessions by adding custom fields with matching code names on the Custom Fields page in /login.
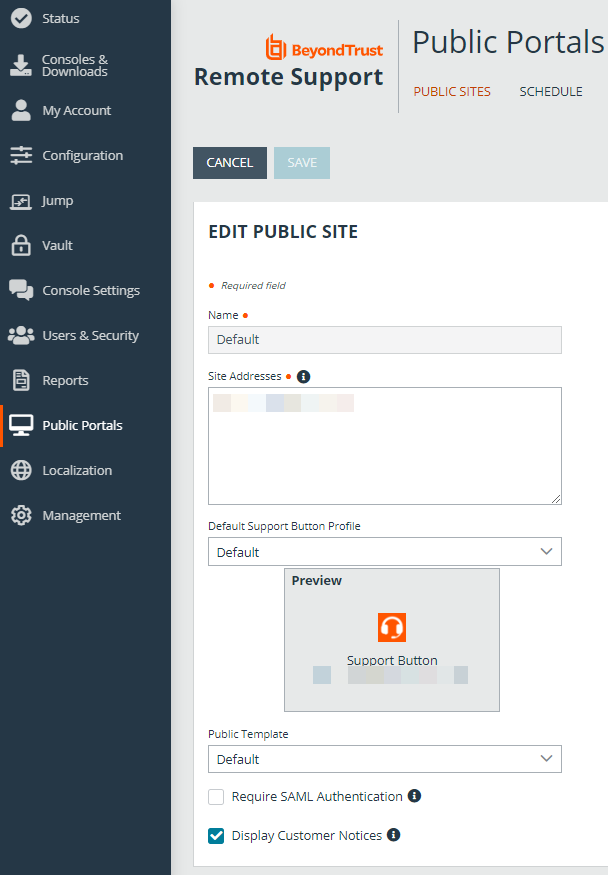
Enable SAML Authentication on a Public Site
Once SAML for Public Portals settings have been configured, you can enable SAML authentication on a public site in /login as follows:
- Go to Public Portals > Public Sites.
- Click Edit next to the desired public site.
- Select Require SAML Authentication.
- Click Save.